Disclaimer, guide line in sharing of research material and malicious source code
25 May 20141. LEGAL DISCLAIMER
Any research material, source code, original terminology, process or security information technology published on the agreement may be the subject of Intellectual Property rights reserved by MalwareMustDie, NPO, its subsidiaries or partners, and are not licensed hereunder. Any malicious software research and codes, programs and any corrections, with its updates or new versions that may be made available by MalwareMustDie, NPO through the agreement are provided subject to the additional terms, conditions and restrictions indicated in the applicable section of the agreement.
If no additional terms are provided on such agreement, malicious software research materials and codes written by all MalwareMustDie,NPO research sites is governed by this provision.
All information provided via the agreement, including, without limitation, any MalwareMustDie, NPO or its subsidiaries' source code or service plans, original terminology, malicious software research programs, malicious software research code, offerings, or programs, statements of future directions, DISCLOSURES or other technical or marketing materials (collectively, "Information") is intended for informational purposes only and is subject to change or withdrawal by MalwareMustDie, NPO at any time without notice. MalwareMustDie, NPO assumes no responsibility for the accuracy or completeness of the Information. THE INFORMATION IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, INCLUDING (WITHOUT LIMITATION) ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT. MALWAREMUSTDIE, NPO, FURTHER DISCLAIMS ANY LIABILITY IN CONNECTION WITH THE SITES OR THE INFORMATION PROVIDED HEREIN. Some jurisdictions do not allow the exclusion of implied warranties, so the above exclusion may not apply to you. IN NO EVENT WILL MALWAREMUSTDIE, NPO BE LIABLE TO ANY PARTY FOR ANY DIRECT, INDIRECT, SPECIAL OR OTHER CONSEQUENTIAL DAMAGES FOR ANY USE OF THE SITES, THE INFORMATION, THE CODES, OR ON ANY OTHER HYPERLINKED MATERIALS, INCLUDING, WITHOUT LIMITATION, ANY LOST PROFITS, BUSINESS INTERRUPTION, LOSS OF PROGRAMS OR OTHER DATA ON YOUR INFORMATION HANDLING SYSTEM OR OTHERWISE, EVEN IF CA IS EXPRESSLY ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
All violation for the disclaimer and its agreement will be against World Intellectual Property Policy and International Patent Policy, to be escalated as claim to the court of law as violation of Malware MustDie, NPO property by duplication, making, using, selling, importing, or distributing a patented invention without permission.
(c)MalwareMustDie(TM),the NPO, 2012-2016.
2. RESEARCH MATERIAL SHARING GUIDELINE
All of the research materials, original terminology announced and posts in MalwareMustDie threat analysis blog (this blog), Google project, Pastebin, Imgur and Mediafire shared documents and some other media sites are the subject of Intellectual Property rights reserved by MalwareMustDie, NPO, its subsidiaries or partners, and are not licensed hereunder, and the subject of the disclaimer stated in previous "Disclaimer" section.
You may read and share, copy, quote, comment and re-publish the material with the written mention addressed to MalwareMustDie, NPO with the link to the related material or post. We have the right to confirm and assess any publicity that is not following this guide line, by legal approach accordingly. And all violation for the disclaimer and this guide line will be against World Intellectual Property Policy and International Patent Policy, to be escalated as claim of violation against the MalwareMustDie, NPO intellectual property by duplication, making, using, selling, importing, illegal copy, illegal quoting or distributing a patented invention without permission.
(c)MalwareMustDie(TM),the NPO, 2012-2016.
3. MALCODE SHARING GUIDELINE
For security reasons we are limiting the sharing of malicious source codes that we secured from bad actors environment under the following explanation.
Basically an archive of a malcode is shared for known, trusted and close security industry community ONLY via our colleague's trusted vetted secure communication. So if you are in AntiVirus, Malware Filtration, or Web/Proxy Attack Filtration (+IDS/IPS) industry's/entity's researchers and want to have the sample but not getting it yet, you can send request by writing comment under related post by including your active security entity's email address you are working for, (it will be not published), or ping us directly in twitter DM and sending mail address with explain about yourself and the security organization you work for. Your request will be checked and followed properly. This procedure will be applied the same way to Government Security Agencies and Law Enforcement Agencies and Incident Response researchers.
The reason why we are limiting the shares is: security. It is not us for being "a picky" to whom we share the materials to, malware source
codes are different to handle.
This area is very sensitive considering the following two points. (1) There is a possibility of an active investigation on the related case.
(2) The subjects are NOT malware samples to be sharable to be learned to crack/reverse/analyze to, but these are the
real malware source codes or malicious tools.. in ready to use form, shortly: the real
crime/stealer/hacking tools! Owning these tools is against the law and order in many countries, and can make yourself being jailed
in some countries. Some of these tools may still be actively spotted in crime operation scene in the internet. Which means: IF these bad tools leak
or go to the irresponsible hands..this can be used for the VERY VERY BAD purpose and MalwareMustDie is not going to take responsibility for that
risk and this disclaimer is designed to make that risk to be as minimum as possible.
In some countries that we are actually living, it is forbidden to pass around these kind of tools w/o strict permission form law enforcement to the appointed limited security entities only. So we are sorry for the bummer to the researcher friends whose are not getting any codes, we do want to share everything, but in your case(s) somehow the requirement doesn't fit to the above. Yet if you still very eager to have the requested materials, please kindly contact to your known security entity or law enforcement in your territory to give you written reference of the research and purpose as the background of your request, to then we can re-discuss the possibility for the purpose.
Why did we post here and announce "the sharing" then? Because in reality there are many security legit entity which haven't seen the shared materials, the knowledge and the awareness is a must-share (to all user-level), since victims must know what & how they get hit by the cyber crime actually.
In sharing, we assure you, we vetted the contacts, we have the right to record and monitor the distribution activity as detailed log to make sure unnoticed party can not access, we don't share to individual/unknown person and we will be happy to deal with legit security entity for sharing the threat information to the widest reachable audience in security community and law enforcement. Please be noted: By the time the object has been downloaded to the requester we DO NOT hold any responsibility for the misused of the materials, yet we will fully cooperative to any law enforcement request to share the download log and share record of a certain sharing event upon asked.
And we have to state this too: We have every right to choose which individual or entity to share with. And also we have every right to change our decision due to some security issue without announcing any notification in advance. We are NOT obligated to share any form of any of malware investigation and research we conduct by default. To share or NOT to share is the decision that our related volunteer team members involved to the case should decide in case by case basis.
In the end, we are terribly sorry if our scheme is not satisfactory to individual security researchers friends. Be free to send us comment or feedback at the below of this post with explaining your real identification or with the proof of your security research, then I am assuring you that you will be assisted upon your status is checked, either way, your information and privacy is remain save and unpublished. Further, without clear identification or by sending us a message by using email from any free any email accounts will not be followed accordingly.
This (see the below picture) is the evidence of what some bad actors in an indecent anti-security forum are actually think
they can get our shared material by contacting us with faking credential of/as a security researcher:
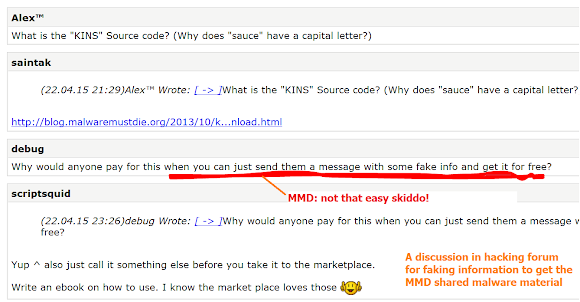
..and because of them we must
conduct strict sharing scheme.
(c)MalwareMustDie(TM),the NPO, 2012-2016.
Thank you for your understanding and support!
Salve, Regina, mater misericordiae, vita, dulcedo et spes nostra, salve.
Ad te clamamus, exules filii Hevae.
Ad te suspiramus gementes et flentes in hac lacrimarum valle.
Eia ergo, advocata nostra, illos tuos misericordes oculos ad nos converte.
Et Jesum, benedictum fructum ventris tui, nobis post hoc exsilium ostende.
O clemens, o pia, o dulcis Virgo Maria.
Ora pro nobis, sancta Dei Genitrix.
Ut digni efficiamur promissionibus Christi.
MalwareMustDie, Non-Profit Organization (NPO)
malwaremustdie.org
(c)MalwareMustDie, 2012-2015