When #malware infector goes to Cloud: Trojan Banker in Free Cloud Storage - MediaFire
06 Sep 2012 This is really sad to know the infection goes to cloud, this is one true case example.I grep the trojan infections in the phising databases just now, came to my interest the list of the file "Application+Form.zip" saved in the many infector urls. As I dns-reversed it came up with the Free Cloud Storage - MediaFire's url. The list and proof itself is as per below:
NetRange: 199.91.152.0 - 199.91.159.255
CIDR: 199.91.152.0/21
OriginAS: AS46179
NetName: MEDIAFIRE-IP-199-91-159-0-21
IP: 199.91.154.64
h00p://199.91.154.64/0zosrljb8eig/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/axfmj3yimhog/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/cbjb39yy2mtg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/mbl6b62bplfg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/q2p8bqdtdawg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/q8fm4zqkmkjg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/su5qgslo1dlg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/txh6n26njnlg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/v9c3p3zh5vqg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/0g1ttmtrg8pg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/f7rq37qx1s9g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/k5493ofo85lg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/42tt073rt8mg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/sze9xfm656qg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.64/uomppw789gbg/uoqv786sj08g7e2/ApplicationForm.zipNetRange: 199.91.152.0 - 199.91.159.255
CIDR: 199.91.152.0/21
OriginAS: AS46179
NetName: MEDIAFIRE-IP-199-91-159-0-21
IP: 199.91.154.107
h00p://199.91.154.107/1alpy8w96qjg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/613u633z438g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/c6oipid67kzg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/l45b9swc4lvg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/rjim6bnfwjzg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/ud90mqgbtggg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/un8fcnc6npgg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/ynvn4i7525qg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/dsxdicu0oscg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.154.107/xagqhgwml7hg/uoqv786sj08g7e2/ApplicationForm.zipNetRange: 205.196.120.0 - 205.196.123.255
CIDR: 205.196.120.0/22
OriginAS: AS46179
NetName: MEDIAFIRE-IP-205-196-120-0-22
IP: 205.196.120.110
h00p://205.196.120.110/0zsxf2wmc7zg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/1zkvem7l3ipg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/d1yheukvdr8g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/dfdi9b6chudg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/hj0bpbgpc2rg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/sb9u45a424pg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/xsbmhu0su5rg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/28zr61bk88sg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/gi91y11z190g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/j3bab9zbovyg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/tmdto78d7pqg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/381r6n65yyng/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/cmc1sjgaazzg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/pv4jkdpb7nzg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/hedpcf570tgg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/cyy4oe5dimbg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/72095k6k72ag/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/s875tvod3mwg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/yu4td1yx6vdg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/bt6l2tp1nwcg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/t0w3djft3pfg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://205.196.120.110/kl8a20aaadkg/uoqv786sj08g7e2/ApplicationForm.zipNetRange: 199.91.152.0 - 199.91.159.255
CIDR: 199.91.152.0/21
OriginAS: AS46179
NetName: MEDIAFIRE-IP-199-91-159-0-21
IP: 199.91.153.124
h00p://199.91.153.124/4cd3dm7gtpzg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/zk1e4ecxarag/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/0okt4q6bj5wg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/3erqoa6mwalg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/420ko8d0jmng/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/7p3zi7vggg0g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/7dqs3rj203ng/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/v73t589ijw1g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/35jbz97j4vkg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/af1ofxzwxz6g/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/e4zta0q4y2ng/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/k5e5qrpfvqxg/uoqv786sj08g7e2/ApplicationForm.zip
h00p://199.91.153.124/iddo976x8rkg/uoqv786sj08g7e2/ApplicationForm.zip
A download PoC are below:
Case 1:--22:40:15-- h00p://199.91.154.64/0zosrljb8eig/uoqv786sj08g7e2/ApplicationForm.
zip
=> `ApplicationForm.zip'
Connecting to 199.91.154.64:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: h00p://www.mediafire.com/?uoqv786sj08g7e2 [following]
--22:40:15-- h00p://www.mediafire.com/?uoqv786sj08g7e2
=> `index.html@uoqv786sj08g7e2'
Resolving www.mediafire.com... 205.196.120.6, 205.196.120.8
Connecting to www.mediafire.com|205.196.120.6|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: h00p://205.196.122.152/ipb7dusor0zg/uoqv786sj08g7e2/Application+Form.z
ip [following]
--22:40:16-- h00p://205.196.122.152/ipb7dusor0zg/uoqv786sj08g7e2/Application+Fo
rm.zip
=> `Application+Form.zip'
Connecting to 205.196.122.152:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 640,712 (626K) [application/zip]
100%[====================================>] 640,712 148.40K/s ETA 00:00
22:40:21 (130.61 KB/s) - `Application+Form.zip' saved [640712/640712]
GET /0zosrljb8eig/uoqv786sj08g7e2/ApplicationForm.zip HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: 199.91.154.64
Connection: Keep-Alive
HTTP/1.1 302 Found
Location: h00p://www.mediafire.com/?uoqv786sj08g7e2
Connection: Close
GET /?uoqv786sj08g7e2 HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: www.mediafire.com
Connection: Keep-Alive
HTTP/1.1 302 Found
Date: Thu, 06 Sep 2012 13:41:36 GMT
Cache-control: no-cache
Pragma: no-cache
Expires: 0
Set-Cookie: ukey=7th4ubnj5cc2ucw0hhiemxt6bi6hh8z8;
expires=Thu, 07-Aug-2014 13:41:36 GMT;
path=/; domain=.mediafire.com; httponly
Location: h00p://199.91.153.246/4ejd935utdag/uoqv786sj08g7e2/Application+Form.zip
Vary: Accept-Encoding
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8
Server: MediaFire
GET /4ejd935utdag/uoqv786sj08g7e2/Application+Form.zip HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: 199.91.153.246
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: LRBD-stable-724
Date: Thu, 6 Sep 2012 13:41:37 GMT
Connection: close
Accept-Ranges: bytes
Content-transfer-encoding: binary
Content-Length: 640712
Content-Disposition: attachment; filename="Application Form.zip"
Content-Type: application/zip
Case 2 :--22:46:34-- h00p://205.196.120.110/hj0bpbgpc2rg/uoqv786sj08g7e2/ApplicationForm.zip
=> `ApplicationForm.zip'
Connecting to 205.196.120.110:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: h00p://www.mediafire.com/?uoqv786sj08g7e2 [following]
--22:46:35-- h00p://www.mediafire.com/?uoqv786sj08g7e2
=> `index.html@uoqv786sj08g7e2'
Resolving www.mediafire.com... 205.196.120.6, 205.196.120.8
Connecting to www.mediafire.com|205.196.120.6|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: h00p://199.91.153.58/3h59697w91jg/uoqv786sj08g7e2/Application+Form.zip
[following]
--22:46:36-- h00p://199.91.153.58/3h59697w91jg/uoqv786sj08g7e2/Application+Form
.zip
=> `Application+Form.zip.1'
Connecting to 199.91.153.58:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 640,712 (626K) [application/zip]
100%[====================================>] 640,712 155.64K/s ETA 00:00
22:46:40 (149.68 KB/s) - `Application+Form.zip.1' saved [640712/640712]
GET /hj0bpbgpc2rg/uoqv786sj08g7e2/ApplicationForm.zip HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: 205.196.120.110
Connection: Keep-Alive
HTTP/1.1 302 Found
Location: h00p://www.mediafire.com/?uoqv786sj08g7e2
Connection: Close
GET /?uoqv786sj08g7e2 HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: www.mediafire.com
Connection: Keep-Alive
HTTP/1.1 302 Found
Date: Thu, 06 Sep 2012 13:46:27 GMT
Cache-control: no-cache
Pragma: no-cache
Expires: 0
Set-Cookie: ukey=5l8f4622p85a2nl61q8yadidbjjyx0wr;
expires=Thu, 07-Aug-2014 13:46:27 GMT;
path=/; domain=.mediafire.com; httponly
Location: h00p://199.91.153.58/3h59697w91jg/uoqv786sj08g7e2/Application+Form.zip
Vary: Accept-Encoding
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8
Server: MediaFire
GET /3h59697w91jg/uoqv786sj08g7e2/Application+Form.zip HTTP/1.0
User-Agent: MalwareMustDie/1.10.1
Accept: */*
Host: 199.91.153.58
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: LRBD-stable-724
Date: Thu, 6 Sep 2012 13:46:27 GMT
Connection: close
Accept-Ranges: bytes
Content-transfer-encoding: binary
Content-Length: 640712
Content-Disposition: attachment; filename="Application Form.zip"
Content-Type: application/zip
I bet there are more of these, since I have to stop my scanning script
because it looks never ending..
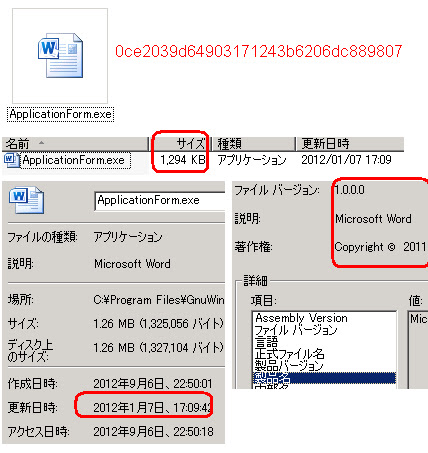
I downloaded it and it was a plain zip file contains this file:
According to the server's time stamp it looks like months ago
released / uploaded trojan. A quicky of binary analysis below:*) PE Information:
Entry Point at 0x132d3e
Virtual Address is 0x53493e
Sections:
.text 0x2000 0x132944 1255936 <---Entry Point
.sdata 0x136000 0x7d 512
.rsrc 0x138000 0x10470 67072
.reloc 0x14a000 0xc 512
*) Suspicious Points:
CRC Fail! Claimed: 0 Actual: 1358198
Compiled: 0x4F087C53 [Sat Jan 07 17:09:39 2012 UTC]
Compiler Trace: Microsoft Visual C# / Basic .NET /Microsoft Visual Studio .NET
Some URLs:
Checking h00p://ns.adobe.com/xap/1.0/sType/ResourceRef# ... OK
Checking h00p://purl.org/dc/elements/1.1/ ... OK
Checking h00p://www.w3.org/1999/02/22-rdf-syntax-ns# ... OK
Checking h00p://ns.adobe.com/xap/1.0/mm/ ... OK
Checking h00p://ns.adobe.com/xap/1.0/ ... OK
Checking h00p://ns.adobe.com/photoshop/1.0/ ... OK
Checking h00p://ns.adobe.com/exif/1.0/ ... OK
Checking h00p://ns.adobe.com/tiff/1.0/ ... OK
Checking h00p://www.apple.com/DTDs/PropertyList-1.0.dtd ... OK
*) Attribute:
LangID: 000004b0
LegalCopyright: Copyright \xa9 2011
Assembly Version: 1.0.0.0
InternalName: ApplicationForm.exe
FileVersion: 1.0.0.0
ProductName: Microsoft Word
ProductVersion: 1.0.0.0
FileDescription: Microsoft Word
OriginalFilename: ApplicationForm.exe
I bet many others already analyzed this sample so I just checked in into VT:MD5: 0ce2039d64903171243b6206dc889807
File size: 1.3 MB ( 1325056 bytes )
File name: ApplicationForm.exe
File type: Win32 EXE
Detection: 30 / 42
Analysis date: 2012-05-07 20:38:32 UTC ( 4month ago )
URL: --->>>[CLICK]
Malware Names:
CAT-QuickHeal : TrojanBanker.MSIL.MultiPhishi
McAfee : Artemis!0CE2039D6490
K7AntiVirus : Trojan
TheHacker : Trojan/MultiPhishing.aa
NOD32 : a variant of MSIL/Spy.Banker.O
Symantec : Infostealer.Bancos
Norman : W32/Troj_Generic.NPFX
TrendMicro-HouseCall : TROJ_SPNR.06B512
Avast : MSIL:Banker-A [Trj]
eSafe : Win32.Infostealer.Ba
Kaspersky : Trojan-Banker.MSIL.MultiPhishing.aa
BitDefender : Gen:Variant.Kazy.42127
Comodo : UnclassifiedMalware
F-Secure : Gen:Variant.Kazy.42127
DrWeb : Trojan.Siggen3.42852
VIPRE : Trojan.Win32.Generic!BT
AntiVir : TR/Kazy.42127.34
TrendMicro : TROJ_SPNR.06B512
McAfee-GW-Edition : Artemis!0CE2039D6490
Emsisoft : Trojan-Banker.MSIL!IK
Jiangmin : Trojan/Banker.MSIL.x
Antiy-AVL : Trojan/MSIL.MultiPhishing.gen
Microsoft : Trojan:Win32/Sisron
GData : Gen:Variant.Kazy.42127
VBA32 : TrojanBanker.MSIL.MultiPhishing.aa
PCTools : Trojan-PSW.Bancos!rem
Ikarus : Trojan-Banker.MSIL
Fortinet : W32/MultiPhishing.AA!tr
AVG : Generic26.CGTQ
Panda : Generic Trojan
Yep, this is the trojan banker which steals your credentials.
It was last detected 4months ago according to the VT database.
I am not going to analyze this because of is an obvious known & well handled malware.
Complete technical analysis can be found in microsoft site↓
And this trojan was reported suddenly grows according to this news↓
Hope Media Fire see this blog to soon get rid of them from their server.