The result on 48hours+ in battle with Kelihos < request for FURTHER block/dismantle cooperation & support. #Tango is going down..
08 Aug 2013 This post is dedicated to many.. so many of wonderful individuals involved with the effort to stand against Kelihos P2P malware infection. This is an example on WHAT CAN BE DONE if InfoSec are gathered to fight malware infection. This report is totally an effort of a team contains members who simply believe the same dream, to free our internet from malware. We cannot make a list of your (so many) names but we are all know who you are and what you did. Sincerely respect with thank you very much. There were many bumpy communication was initially made, for the tense and rogue communication we apology to every inconveniences. I personally am so happy to live in an era of gentlemen like you are! #MalwareMustDie!First, you need to know what the Kelihos Botnet & malware threat is, our previous post gives you good illustration about the threat here-->>[Previous Post]. As per you maybe noticed in the our twitter timeline, we are doing our best effort in battle with the Kelihos malware scum, yes we were haunted by this infection via RedKit Exploit Kits, TDSS, direct spam or via its botnet self-updating function itself and this "scum" still out there and feeling happy-ever-after infecting us, we just can not accept this fact.
Therefore we executed every possible effort that can be done as a bunch of volunteers of an NPO entity to suppress their growth in internet. As the efforts itself is varied from suspension, sinkhole, DNSBL block, VT/URLQuery (+etc) blacklisting, OpenDNS/GoogleDNS blocking, parallel with bunch of reports to the regional basis authorities (CERTs, GroupIB, ISPs, Registrar, ICANN, Microsoft) and to varied Sinkhole entities.
We recieved the great help and support from the people in the entities mentioned above, and also with a perfect work delegation between our team in twitter so we are able to gain a good fight and successfully resulted some good achivements within 48hours+. It is unfair to let people who help and support us by seeing only twitter as result that's why I posted our effort's report here, together with some tips and tricks used in fighting this infection in our beloved MalwareMustDie blog.
And this post is the report of the mentioned effort. Here we go..
1. Stopping the new Kelihos NS based .COM services
By the time we started this effort, Kelihos started to switch their DNS from something with ns[1-6]."\][a-z]\{7\,8\}\.".RU into the .COM tld domains with the format ns[1-6]."\][a-z]\{7\}\.".COM , we found that all of the domains was released by INTERNET.BS a well-known registrar of being abused by the cybercrime to release their infector domains. And with the great help from the very dedicated individuals mentioned above we took these domains (see below) off internet:
DUSSEVA.COMbelow is the PoC of the suspension and sinkholing result:
BEUHNIM.COM
GULFKAT.COM
ZUNCHER.COM
FLOWSRE.COM
OMBUGEW.COM
WIDERAT.COM
DAVUJUZ.COM
XEXUMYB.COM
KAROZGI.COM
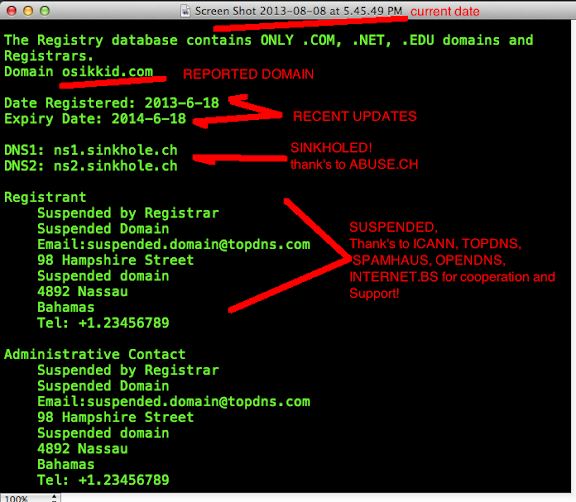
OSIKKID.COM
NIGUCGU.COM
This is how they got into internet:
The following is some of PoC and hard evidence of the .COM that Kelihos used are in the extracted INTERNET.BS released domains database-->>[PASTEBIN]#MalwareMustDie! Bahama registrar @internetbs was proven releasing #Kelihos 12(twelve) .COMs in past 2mnth as main NS infector! #PlsHelpRT
— MalwareMustDie, NPO (@MalwareMustDie) August 8, 2013
2. The dismantling effort of .RU infectors
Currently, the main basis of the Kelihos infecion are using the .RU basis ccTLD domain. It is very important to suppress their growth in their home-base also. With the great coordination and help fro GroupIB we made effort to dismantle the other "NEW" 101 .RU "weaponized domains as per listed below:
Date: Thu Aug 8 19:54:43 JST 2013From the status of weaponized by Kelihos to infect as per recorded HLUX's A records in here:
ABJIQFIR.RU,, ns[1-6].karozgi.com
ACXYPZUK.RU,, ns[1-6].karozgi.com
AFEBIRYN.RU,, ns[1-6].karozgi.com
ANGENJEJ.RU,, ns[1-6].karozgi.com
BADMYVOK.RU,, ns[1-6].karozgi.com
BEZGESUK.RU,, ns[1-6].karozgi.com
BITITROJ.RU,, ns[1-6].karozgi.com
BOVEWHAV.RU,, ns[1-6].karozgi.com
BOWRETTI.RU,, ns[1-6].karozgi.com
CICDIWYH.RU,, ns[1-6].karozgi.com
COLYDQEC.RU,, ns[1-6].karozgi.com
CYVWYDJE.RU,, ns[1-6].karozgi.com
DAHADKYZ.RU,, ns[1-6].karozgi.com
DEPCOPUQ.RU,, ns[1-6].karozgi.com
DEQYPPIL.RU,, ns[1-6].karozgi.com
DIICUHXA.RU,, ns[1-6].karozgi.com
EJOPOWOZ.RU,, ns[1-6].karozgi.com
EJQIURMY.RU,, ns[1-6].karozgi.com
FITUZVOF.RU,, ns[1-6].karozgi.com
FOJEGGUF.RU,, ns[1-6].karozgi.com
GAJKUKUC.RU,, ns[1-6].karozgi.com
GECAKCEM.RU,, ns[1-6].karozgi.com
GYCBOKUD.RU,, ns[1-6].karozgi.com
HURVINEV.RU,, ns[1-6].karozgi.com
HUZNEJEX.RU,, ns[1-6].karozgi.com
HYNEQREL.RU,, ns[1-6].karozgi.com
IMKYHTUG.RU,, ns[1-6].karozgi.com
IPXYJYOQ.RU,, ns[1-6].karozgi.com
ITWILMEP.RU,, ns[1-6].karozgi.com
IWKYXSEZ.RU,, ns[1-6].karozgi.com
IXMUTIRI.RU,, ns[1-6].karozgi.com
JAHKUXYV.RU,, ns[1-6].karozgi.com
JEFDYWSO.RU,, ns[1-6].karozgi.com
JIQLIDOX.RU,, ns[1-6].karozgi.com
JOKLASAN.RU,, ns[1-6].karozgi.com
KAPKICOH.RU,, ns[1-6].karozgi.com
KEBWAKQY.RU,, ns[1-6].karozgi.com
KICSIHOP.RU,, ns[1-6].karozgi.com
KIZCIVZE.RU,, ns[1-6].karozgi.com
KUBGYBOH.RU,, ns[1-6].karozgi.com
KYCROTUS.RU,, ns[1-6].karozgi.com
LICLAJLE.RU,, ns[1-6].karozgi.com
LIMJOZEH.RU,, ns[1-6].karozgi.com
LIZECGIJ.RU,, ns[1-6].karozgi.com
LUFRUDET.RU,, ns[1-6].karozgi.com
LUPQUXSE.RU,, ns[1-6].karozgi.com
LYOHGEOF.RU,, ns[1-6].karozgi.com
MAPUHXAF.RU,, ns[1-6].karozgi.com
MOHGOXEB.RU,, ns[1-6].karozgi.com
MYBFABWI.RU,, ns[1-6].karozgi.com
NECUWFEW.RU,, ns[1-6].karozgi.com
NENKUDYF.RU,, ns[1-6].karozgi.com
NICLYCOM.RU,, ns[1-6].karozgi.com
NOJQAVYJ.RU,, ns[1-6].karozgi.com
NORWOLLU.RU,, ns[1-6].karozgi.com
NUKUNNOQ.RU,, ns[1-6].karozgi.com
ONSUGNEM.RU,, ns[1-6].karozgi.com
ORNEVKYC.RU,, ns[1-6].karozgi.com
PEXDAJYP.RU,, ns[1-6].karozgi.com
PIVGEVIT.RU,, ns[1-6].karozgi.com
PIYMNYFA.RU,, ns[1-6].karozgi.com
POWERWIK.RU,, ns[1-6].karozgi.com
PUPUXHEF.RU,, ns[1-6].karozgi.com
PYDAJZYK.RU,, ns[1-6].karozgi.com
QABADPIX.RU,, ns[1-6].karozgi.com
QOFHIRAW.RU,, ns[1-6].karozgi.com
QYSQUWKO.RU,, ns[1-6].karozgi.com
RIFAUTIR.RU,, ns[1-6].karozgi.com
RIZIKCUG.RU,, ns[1-6].karozgi.com
ROVSYMWO.RU,, ns[1-6].karozgi.com
RYTEOPBY.RU,, ns[1-6].karozgi.com
SAWSOBCY.RU,, ns[1-6].karozgi.com
SOMOXBET.RU,, ns[1-6].karozgi.com
TAFIBCUM.RU,, ns[1-6].karozgi.com
TAZGYVAX.RU,, ns[1-6].karozgi.com
TITGOQTE.RU,, ns[1-6].karozgi.com
TYZFOWFE.RU,, ns[1-6].karozgi.com
UWPAYTNU.RU,, ns[1-6].karozgi.com
VEFLOHGY.RU,, ns[1-6].karozgi.com
VEKDEGYL.RU,, ns[1-6].karozgi.com
VUZNIQIK.RU,, ns[1-6].karozgi.com
VYFUXTIS.RU,, ns[1-6].karozgi.com
WANZAWBY.RU,, ns[1-6].karozgi.com
WODYFWOD.RU,, ns[1-6].karozgi.com
WORLIPXO.RU,, ns[1-6].karozgi.com
XAKRYXOG.RU,, ns[1-6].karozgi.com
XIMIRSEX.RU,, ns[1-6].karozgi.com
XIMXAMLI.RU,, ns[1-6].karozgi.com
XUGNEMYQ.RU,, ns[1-6].karozgi.com
YFKYTXIX.RU,, ns[1-6].karozgi.com
YFXIGUSO.RU,, ns[1-6].karozgi.com
YGXEYVXI.RU,, ns[1-6].karozgi.com
YJSEYGFY.RU,, ns[1-6].karozgi.com
YWHYIWDY.RU,, ns[1-6].karozgi.com
ZADNAZVO.RU,, ns[1-6].karozgi.com
ZUNCUHAK.RU,, ns[1-6].karozgi.com
ZUVNENAX.RU,, ns[1-6].karozgi.com
ZUZVAQAW.RU,, ns[1-6].karozgi.com
ZYHIJWIN.RU,, ns[1-6].karozgi.com
ZYRTYDAJ.RU,, ns[1-6].karozgi.com
Date: Fri, 2 Aug 2013 11:43:40 -0700 (PDT)And currently in blocking effort with OpenDNS & sinkhole the below RU domains:
ABJIQFIR.RU,188.209.251.38,
ACXYPZUK.RU,109.89.137.178,
AFEBIRYN.RU,,
ANGENJEJ.RU,,
BADMYVOK.RU,77.122.196.95,
BEZGESUK.RU,77.122.139.203,
BITITROJ.RU,109.191.82.32,
BOVEWHAV.RU,93.79.91.188,
BOWRETTI.RU,,
CICDIWYH.RU,89.229.196.228,
COLYDQEC.RU,46.56.67.7,
CYVWYDJE.RU,190.220.70.5,
DAHADKYZ.RU,178.75.46.67,
DEPCOPUQ.RU,89.149.105.201,
DEQYPPIL.RU,109.87.198.110,
DIICUHXA.RU,95.111.205.207,
EJOPOWOZ.RU,79.112.214.164,
EJQIURMY.RU,188.129.240.79,
FITUZVOF.RU,37.229.99.95,
FOJEGGUF.RU,,
GAJKUKUC.RU,176.37.121.102,
GECAKCEM.RU,77.122.191.111,
GYCBOKUD.RU,176.8.231.155,
HURVINEV.RU,46.237.110.5,
HUZNEJEX.RU,95.65.80.117,
HYNEQREL.RU,94.76.110.237,
IMKYHTUG.RU,37.252.67.195,
IPXYJYOQ.RU,93.79.231.55,
ITWILMEP.RU,,
IWKYXSEZ.RU,178.218.66.19,
IXMUTIRI.RU,109.207.113.126,
JAHKUXYV.RU,46.185.24.210,
JEFDYWSO.RU,93.125.45.196,
JIQLIDOX.RU,109.201.107.204,
JOKLASAN.RU,88.206.28.89,
KAPKICOH.RU,109.207.118.98,
KEBWAKQY.RU,109.251.94.117,
KICSIHOP.RU,77.120.229.169,
KIZCIVZE.RU,86.101.22.28,
KUBGYBOH.RU,77.122.217.253,
KYCROTUS.RU,94.253.45.147,
LICLAJLE.RU,46.33.55.77,
LIMJOZEH.RU,93.126.126.71,
LIZECGIJ.RU,,
LUFRUDET.RU,159.224.76.42,
LUPQUXSE.RU,37.115.91.192,
LYOHGEOF.RU,109.87.162.4,
MAPUHXAF.RU,37.46.226.241,
MOHGOXEB.RU,194.28.4.29,
MYBFABWI.RU,27.49.104.107,
NECUWFEW.RU,94.231.181.24,
NENKUDYF.RU,178.165.23.171,
NICLYCOM.RU,,
NOJQAVYJ.RU,98.193.167.182,
NORWOLLU.RU,178.137.203.149,
NUKUNNOQ.RU,24.49.38.150,
ONSUGNEM.RU,77.85.201.46,
ORNEVKYC.RU,219.70.195.200,
PEXDAJYP.RU,31.128.186.43,
PIVGEVIT.RU,,
PIYMNYFA.RU,46.173.112.16,
POWERWIK.RU,94.244.129.195,
PUPUXHEF.RU,176.8.38.115,
PYDAJZYK.RU,2.68.213.50,
QABADPIX.RU,46.211.63.25,
QOFHIRAW.RU,176.37.121.102,
QYSQUWKO.RU,178.137.72.42,
RIFAUTIR.RU,213.111.69.126,
RIZIKCUG.RU,,
ROVSYMWO.RU,,
RYTEOPBY.RU,89.146.79.57,
SAWSOBCY.RU,,
SOMOXBET.RU,121.129.93.208,
TAFIBCUM.RU,109.87.7.53,
TAZGYVAX.RU,180.110.156.205,
TITGOQTE.RU,189.199.182.2,
TYZFOWFE.RU,,
UWPAYTNU.RU,77.122.227.41,
VEFLOHGY.RU,,
VEKDEGYL.RU,46.173.77.173,
VUZNIQIK.RU,94.230.192.50,
VYFUXTIS.RU,151.0.27.230,
WANZAWBY.RU,212.142.96.18,
WODYFWOD.RU,77.85.201.46,
WORLIPXO.RU,77.121.79.14,
XAKRYXOG.RU,118.160.103.152,
XIMIRSEX.RU,220.137.79.242,
XIMXAMLI.RU,195.24.155.245,
XUGNEMYQ.RU,77.120.179.237,
YFKYTXIX.RU,46.211.85
YFXIGUSO.RU,195.24.155.245,
YGXEYVXI.RU,178.211.139.155,
YJSEYGFY.RU,,
YWHYIWDY.RU,123.236.68.229,
ZADNAZVO.RU,27.6.9.213,
ZUNCUHAK.RU,,
ZUVNENAX.RU,119.14.86.100,
ZUZVAQAW.RU,123.241.73.225,
ZYHIJWIN.RU,178.151.24.58,
ZYRTYDAJ.RU,31.42.119.142,
EJWOPWYZ.RU,188.27.168.54, ns[1-6].osikkid.comBelos is the official information received from GroupIB for SUSPENSION of 100 another domains Kelihos we reported, which was swiftly followed in less than 48 hours! :-)
EKREDTEF.RU,, ns[1-6].osikkid.com
EQGYQTAD.RU,46.250.23.59, ns[1-6].osikkid.com
EVLYLTUX.RU,94.154.224.58, ns[1-6].osikkid.com
FIBLOQAF.RU,, ns[1-6].osikkid.com
FINQIMIG.RU,, ns[1-6].osikkid.com
FOHKYQUW.RU,92.113.255.98, ns[1-6].osikkid.com
FOWAJKUG.RU,, ns[1-6].osikkid.com
FYBYNKEQ.RU,, ns[1-6].osikkid.com
FYDIWGAZ.RU,, ns[1-6].osikkid.com
FYGJUGLI.RU,180.176.172.93, ns[1-6].osikkid.com
FYJTIHOX.RU,, ns[1-6].osikkid.com
FYTUCTOX.RU,, ns[1-6].osikkid.com
GEGDYRAG.RU,, ns[1-6].osikkid.com
GEGMULAD.RU,36.229.82.210, ns[1-6].osikkid.com
GENUVBIZ.RU,, ns[1-6].osikkid.com
GIZROSCA.RU,, ns[1-6].osikkid.com
GUQIDRUV.RU,91.224.168.65, ns[1-6].osikkid.com
HAMOVLOX.RU,, ns[1-6].osikkid.com
HAZLYDUW.RU,85.198.179.73, ns[1-6].osikkid.com
HIHFELGO.RU,, ns[1-6].osikkid.com
HIILOSAB.RU,111.251.91.74, ns[1-6].osikkid.com
HIKKINUF.RU,, ns[1-6].osikkid.com
HOKKINYF.RU,62.231.183.49, ns[1-6].osikkid.com
IVKEUHUW.RU,178.150.244.54, ns[1-6].osikkid.com
IXCUPDAM.RU,124.123.169.123, ns[1-6].osikkid.com
JIBDEFUP.RU,, ns[1-6].osikkid.com
JIXUDRER.RU,, ns[1-6].osikkid.com
JUQUTSAF.RU,112.139.167.48, ns[1-6].osikkid.com
JURLYQYR.RU,129.15.40.86, ns[1-6].osikkid.com
JUVBEBEC.RU,, ns[1-6].osikkid.com
JYHVYCLI.RU,, ns[1-6].osikkid.com
JYSHIWIK.RU,, ns[1-6].osikkid.com
KANRUQYC.RU,, ns[1-6].osikkid.com
KEJIKKIB.RU,77.52.104.119, ns[1-6].osikkid.com
LAWNUPAS.RU,, ns[1-6].osikkid.com
LENEVRYP.RU,, ns[1-6].osikkid.com
LIFNAGCI.RU,, ns[1-6].osikkid.com
LILXAJTE.RU,, ns[1-6].osikkid.com
MEDULZAL.RU,, ns[1-6].osikkid.com
MOJJIQUF.RU,, ns[1-6].osikkid.com
MUBYBLAZ.RU,, ns[1-6].osikkid.com
NADKEWLO.RU,, ns[1-6].osikkid.com
NEQAJDAC.RU,, ns[1-6].osikkid.com
NUJOJPAL.RU,, ns[1-6].osikkid.com
PABOBBAH.RU,, ns[1-6].osikkid.com
PELVOJEL.RU,, ns[1-6].osikkid.com
PEQINNIR.RU,, ns[1-6].osikkid.com
PIGOVFIJ.RU,, ns[1-6].osikkid.com
PYMSILIQ.RU,, ns[1-6].osikkid.com
QAQIQGOD.RU,, ns[1-6].osikkid.com
QEGYRDAD.RU,, ns[1-6].osikkid.com
QEHWOCSI.RU,115.241.91.53, ns[1-6].osikkid.com
RALYMEBU.RU,77.198.70.248, ns[1-6].osikkid.com
RAWPENEP.RU,114.38.44.145, ns[1-6].osikkid.com
RAZCAMIT.RU,37.112.160.119, ns[1-6].osikkid.com
RETUCWYX.RU,, ns[1-6].osikkid.com
RIHSYCVO.RU,213.111.155.5, ns[1-6].osikkid.com
RIZOMCOF.RU,178.74.237.85, ns[1-6].osikkid.com
RYCNISAV.RU,, ns[1-6].osikkid.com
RYGXUQYF.RU,, ns[1-6].osikkid.com
SECZYPRY.RU,46.162.9.40, ns[1-6].osikkid.com
SEPOILOK.RU,, ns[1-6].osikkid.com
SIPVAQBE.RU,188.242.51.78, ns[1-6].osikkid.com
SOKXENBY.RU,37.221.142.107, ns[1-6].osikkid.com
TERUJBIH.RU,, ns[1-6].osikkid.com
TYVWUQAL.RU,, ns[1-6].osikkid.com
UDPYCBEL.RU,, ns[1-6].osikkid.com
UHHUWTEG.RU,, ns[1-6].osikkid.com
UJDOGVIC.RU,, ns[1-6].osikkid.com
UQEBENEW.RU,, ns[1-6].osikkid.com
VESYKVEL.RU,193.107.102.209, ns[1-6].osikkid.com
VUVSIMXO.RU,, ns[1-6].osikkid.com
WYMCEKIN.RU,, ns[1-6].osikkid.com
XUBQOBOH.RU,, ns[1-6].osikkid.com
XUVGYSCI.RU,, ns[1-6].osikkid.com
XYBYHCYZ.RU,, ns[1-6].osikkid.com
XYTFYRSU.RU,, ns[1-6].osikkid.com
ZAGTYCAM.RU,, ns[1-6].osikkid.com
ZEVIJAEF.RU,, ns[1-6].osikkid.com
ZUCFIZME.RU,, ns[1-6].osikkid.com
ZUQTIZYH.RU,, ns[1-6].osikkid.com
ZYCPOHDU.RU,, ns[1-6].osikkid.com
ZYVMYSXA.RU,1.168.215.194, ns[1-6].osikkid.com
Dear Partners,
Group-IB CERT (CERT-GIB) has suspended the following domains:
acbimnik.ru
ajwablet.ru
albodlyc.ru
aqxiwtil.ru
avdicsuw.ru
awpavdog.ru
bevywcoc.ru
bezekqen.ru
bivozhij.ru
cahmydjo.ru
cyjukpym.ru
cyknewyh.ru
cyqsuxon.ru
diijgyan.ru
dyotukci.ru
dyradleq.ru
ejwopwyz.ru
ekredtef.ru
eqgyqtad.ru
evlyltux.ru
fibloqaf.ru
finqimig.ru
fohkyquw.ru
fowajkug.ru
fybynkeq.ru
fydiwgaz.ru
fygjugli.ru
fyjtihox.ru
fytuctox.ru
gegdyrag.ru
gegmulad.ru
genuvbiz.ru
gizrosca.ru
guqidruv.ru
hamovlox.ru
hazlyduw.ru
hihfelgo.ru
hiilosab.ru
hikkinuf.ru
hokkinyf.ru
ivkeuhuw.ru
ixcupdam.ru
jibdefup.ru
jixudrer.ru
juqutsaf.ru
jurlyqyr.ru
juvbebec.ru
jyhvycli.ru
jyshiwik.ru
kanruqyc.ru
kejikkib.ru
lawnupas.ru
lenevryp.ru
lifnagci.ru
lilxajte.ru
medulzal.ru
mojjiquf.ru
mubyblaz.ru
nadkewlo.ru
neqajdac.ru
nujojpal.ru
pabobbah.ru
pelvojel.ru
peqinnir.ru
pigovfij.ru
pymsiliq.ru
qaqiqgod.ru
qegyrdad.ru
qehwocsi.ru
ralymebu.ru
rawpenep.ru
razcamit.ru
retucwyx.ru
rihsycvo.ru
rizomcof.ru
rycnisav.ru
rygxuqyf.ru
seczypry.ru
sepoilok.ru
sipvaqbe.ru
sokxenby.ru
terujbih.ru
tyvwuqal.ru
udpycbel.ru
uhhuwteg.ru
ujdogvic.ru
uqebenew.ru
vesykvel.ru
vuvsimxo.ru
wymcekin.ru
xubqoboh.ru
xuvgysci.ru
xybyhcyz.ru
xytfyrsu.ru
zagtycam.ru
zevijaef.ru
zucfizme.ru
zuqtizyh.ru
zycpohdu.ru
zyvmysxa.ru
3. How we PoC an NS infector in commercial TLD
This is how we always PoC the new infector in the wild, we share this as a know how for everyone to help to be able to spot and report the new infection, we use our PoC for OSIKKID.COM as per below:
'(1) Spreads the HLUX as per below checks:'
bash-3.2$ date
Thu Aug 8 12:57:18 JST 2013
// the HLUX IP..
bash-3.2$ while true; do dig +short OSIKKID.COM; sleep 1; done
119.14.28.104
218.166.2.199
125.215.84.135
77.123.42.134
183.72.199.4
36.234.222.167
114.38.198.134
117.197.230.88
95.30.210.87
160.75.9.240
46.250.101.113
175.111.40.232
46.250.99.105
[...]
'(2) Serving Payload malware of Kelihos'
and every A records is serving Kelihos payload:
// Below is the currently download PoC:
bash-3.2$ while true; do wget h00p://OSIKKID.COM/rasta01.exe; sleep 1; done
--2013-08-08 12:59:14-- h00p://osikkid.com/rasta01.exe
Resolving osikkid.com... 89.136.131.41
Connecting to osikkid.com|89.136.131.41|:80... connected.
HTTP request sent, awaiting response... 200
Length: 1221261 (1.2M) []
Saving to: ‘rasta01.exe’
100%
Last-modified header invalid -- time-stamp ignored.
2013-08-08 12:59:22 (260 KB/s) - ‘rasta01.exe’ saved [1221261/1221261]
--2013-08-08 12:59:42-- h00p://osikkid.com/rasta01.exe
Resolving osikkid.com... 124.111.249.204
Connecting to osikkid.com|124.111.249.204|:80... connected.
HTTP request sent, awaiting response... ç200
Length: 1221261 (1.2M) []
Saving to: ‘rasta01.exe.2’
Last-modified header invalid -- time-stamp ignored.
2013-08-08 12:59:53 (1003 KB/s) - ‘rasta01.exe.2’ saved [1221261/1221261]
[...]
'(3) INTERNET.BS registration is current MO.'
It is proven behind the registration process of this domains
We tried to remotely extracted the registrar: INTERNET.BS released
domain from current day until Jun the 1st, and this domain is one of it:
bash-3.2$ whois osikkid.com
Whois Server Version 2.0
Domain names in the .com and .net domains can now be registered
with many different competing registrars. Go to http://www.internic.net
for detailed information.
Domain Name: OSIKKID.COM
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS1.OSIKKID.COM
Name Server: NS2.OSIKKID.COM
Name Server: NS3.OSIKKID.COM
Name Server: NS4.OSIKKID.COM
Name Server: NS5.OSIKKID.COM
Name Server: NS6.OSIKKID.COM
Status: clientTransferProhibited
Updated Date: 06-aug-2013
Creation Date: 18-jun-2013
Expiration Date: 18-jun-2014
>>> Last update of whois database: Thu, 08 Aug 2013 04:03:30 UTC <<<
'(4) The linked DNS services used with the previous Kelihos reported NS services:'
The NS1. of this domains is linked with the same NS as previous reported:
ns1.OSIKKID.COM = ns3.davujuz.com
ns2.OSIKKID.COM = ns5.ns4, ns2.ns4.ombugew.com
ns3.OSIKKID.COM = ns1.davujuz.com
...and so on...
'(5) The infection raised in RU are causing by OSIKKD.COM NS server:'
The 100 domains RU are needed to be blocked with the same pattern as we previously reported to Group IB, under REGGI.RU, (and FYI the abuse of the RU by the kelihos is more than 12,000 domains not included this one... )
This is the PoC that the domains of RU was registered 24hrs more under the OSIKKD.COM NS :
domain: ACBIMNIK.RU
nserver: ns1.osikkid.com.
nserver: ns2.osikkid.com.
nserver: ns3.osikkid.com.
nserver: ns4.osikkid.com.
nserver: ns5.osikkid.com.
nserver: ns6.osikkid.com.
state: REGISTERED, DELEGATED, UNVERIFIED
person: Private Person
registrar: REGGI-REG-RIPN
admin-contact: https://panel.reggi.ru/user/whois/webmail/
created: 2013.08.06
paid-till: 2014.08.06
free-date: 2014.09.06
Below is the check of the reported RU affiliated by the NS of the OSIKKID.COM crossed by the IP and DNS:
ACBIMNIK.RU,, ns1.osikkid.com.
ns2.osikkid.com.
ns3.osikkid.com.
ns4.osikkid.com.
ns5.osikkid.com.
ns6.osikkid.com.
AJWABLET.RU,123.240.108.221, ns1.osikkid.com.
ns2.osikkid.com.
ns3.osikkid.com.
ns4.osikkid.com.
ns5.osikkid.com.
ns6.osikkid.com.
ALBODLYC.RU,, ns1.osikkid.com.
ns2.osikkid.com.
ns3.osikkid.com.
ns4.osikkid.com.
ns5.osikkid.com.
ns6.osikkid.com.
[...]
4. Monitoring The Actual Infection Range
As per today before the NS sinkholing on effect, with the great effort of our members we monitor the infection of the 1,287 IP address actively distributing Kelihos malware payload all over the world as per listed in our pastebin here-->>[LINK]
You can add the /rasta01.exe after the IP to get the latest Kelihos sample payload for your research purpose, as per below sample:
The below binary files also can be used for the same monitoring purpose:
/keybex4.exe
/bljat01.exe
/cuper01.exe
/rasta01.exe
/calc.exe
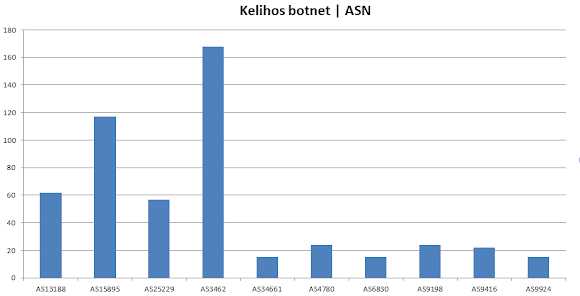
These infection is plotted in the good graphical interface by Chris J Wilson as per below:
Infection based per ASN:


Infection based by country:

Prologue
The effort is not stopping now.. see below:
And what a FAST action from our friends!! See the time stamp in the tweets, it is AMAZING to suspend & sinkhole malware domains THAT fast! :-)) (you guys rocks!!)#MalwareMustDie! The #Kelihos scums JUST register NEW domain NIGUCGU,COM <via @internetbs TODAY! #BLOCK & #Tango this pic.twitter.com/zCwiPyb8W4
— MalwareMustDie, NPO (@MalwareMustDie) August 8, 2013
#MalwareMustDie! Thank's for helps! NIGUCGU,COM is SUSPENDED + in SINKHOLE now! Let's hear #Kelihos scum CRY harder! pic.twitter.com/KKIgkRaLav
— MalwareMustDie, NPO (@MalwareMustDie) August 8, 2013
We work hard on trying to break this "Kelihos" legend methodologically and the method works!
Don't ever let the Kelihos scums enter the internet! Spot & stop them instantly, cooperate with the abused registrar to get the new infectors go to sinkholes and to suspend those new domains instantly.
They weakness is in their DNS, these services backboned their payload distribions of thousands IP and infector domains. And those DNS are using static addresses of un-removeable machines. This IS a target to be shutdown!
Thus, DO NOT let those NS getting any domains in our internet! Is not easy to shift their DNS, it hurts them very bad, they just change the name server domains time after time. And right now they need to have a non-RU domains for their DNS to survive their botnet longer.
Let's build the procedure to SPOT, BLOCK, SUSPEND & CLEAN-UP in one flow altogether!
We need your help, your support in coordination with Kelihos botnet's suppress effort. Please cooperate!
Recent Updates
#MalwareMustDie! #WARNING #KELIHOS NEW DOMAIN: OFCIWOX,COM http://t.co/YtKlsk6yFe <NEW Registrar: PDR LTD./ DOMALAND pic.twitter.com/Awa4k8g5Wu
— MalwareMustDie, NPO (@MalwareMustDie) August 9, 2013
#MalwareMustDie! Kelihos is using Registrar: PDR LTD. D/B/A http://t.co/yc1mHo1akL now with/RegDB: DOMALAND <#Monitor pic.twitter.com/klLEuFrSFv
— MalwareMustDie, NPO (@MalwareMustDie) August 9, 2013
#MalwareMustDie! Now "finally" we see the #Kelihos botnet IP in US (pic) http://t.co/cZZRisjXzp < better check.. pic.twitter.com/VOTy4JZfVH
— MalwareMustDie, NPO (@MalwareMustDie) August 9, 2013
#MalwareMustDie! Additional 8 NEW of #KELIHOS .COM was followed. Thank's @VriesHd & @DhiaLite , Copy of email report: http://t.co/FVGjjIzTSM
— MalwareMustDie, NPO (@MalwareMustDie) August 9, 2013
#MalwareMustDie! Gentlemen, Today's #Kelihos IP in breakdown details: http://t.co/3jtls5i45X < grep your CN, grep the network & spread this!
— MalwareMustDie, NPO (@MalwareMustDie) August 9, 2013
And even registrar also cooperated beforehand w.o waiting sinkhole :-) Thank you!#MalwareMustDie! Summary of the Kelihos fighting today: http://t.co/3Y4LUpjscA Thank's: @abuse_ch @opendns @GroupIB @DhiaLite @VriesHd
— MalwareMustDie, NPO (@MalwareMustDie) August 10, 2013
#MalwareMustDie! Great #ACT of @abuse_ch to SINKHOLE freshly spotted #Kelihos .COMs (pic) /c: @DhiaLite @VriesHd @ALL pic.twitter.com/HebriR5XMU
— MalwareMustDie, NPO (@MalwareMustDie) August 10, 2013
Our friend, Chris J Wilson was making great statistic of the latest infection data:
AS Number base infection data: 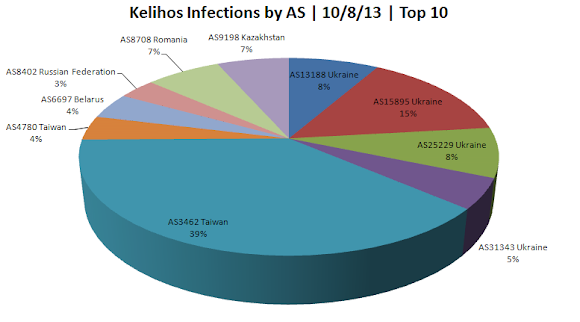
#MalwareMustDie #Kelihos .COM current sinkhole status (pic) @VriesHd @DhiaLite @ConradLongmore @abuse_ch pic.twitter.com/sUw8VVcyTq
— MalwareMustDie, NPO (@MalwareMustDie) August 11, 2013
#MalwareMustDie! Kelihos botnet IP milked today http://t.co/Bf4sn2qTw1 < please help to contact & clean up your CN/network from infection!
— MalwareMustDie, NPO (@MalwareMustDie) August 11, 2013
#MalwareMustDie! Here is the latest our official report on #Kelihos operation today: http://t.co/OGbw5rGkl3 THANK'S FOR YOUR HELP!! < ALL!
— MalwareMustDie, NPO (@MalwareMustDie) August 12, 2013
Terrific world map of infection by chris J Wilson:#MalwareMustDie! Current #Kelihos block list (pic) pic.twitter.com/xEOW6SRLXA
— MalwareMustDie, NPO (@MalwareMustDie) August 12, 2013
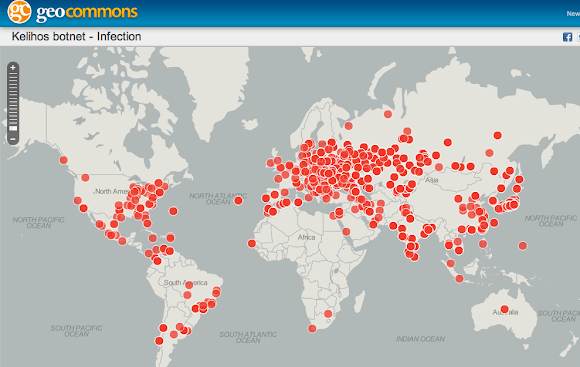
Graph URL is here-->>[LINK]
After .COM the Kelihos moronz shifts to .ME, .ORG & .INFO
Is an idiotic and pathetic act, they don't know with whom they are dealing with now.. 


#MalwareMustDie!


