MMD-0006-2013 - Rogue 302-Redirector "Cushion Attack", an attempt to evade IDS/IPS
21 Sep 2013 This is a quick post, of current on going web-driven malicious web traffic redirection threat with high possibility to malware infection. I was supervising some surveillance operations for one and a half month straight so I probably don't know recent progress whether any researchers already cover this, but since there many links for this threat raising up now, I dare myself peeling & exposing this threat for the awareness purpose. For the IDS/IPS industry this reading is a must read, for I am sure there is no coincidence regarding to this new phenomena in web threat.It's all started from an "Angel" (thank you so much!) who hinted me with the bunch of interesting URLs: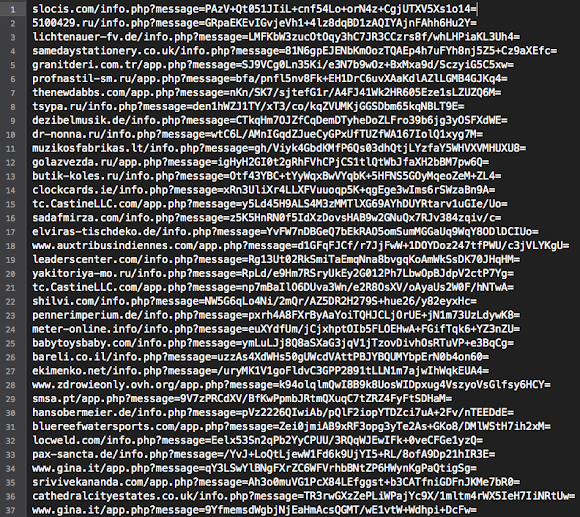
Since there is a possibility the hash will change, so practically it can be described with the regex below:
For confirming the regex above and the result, you can check it out in the URLQuery (w/thanks friends, can't research this well without your site!) in-->HERE
Seeing the url status, some of them are cleaned up stuffs (which is VERY GOOD), so I went to the "difficult to cure" sites to check the origin and native of the threat, and found the "alive" redirection base by the fake HTTP 302 redirection as per I captured below: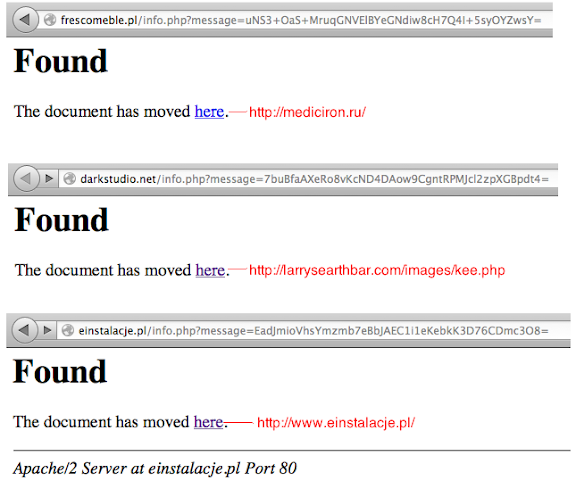
If we go all the way along with the list, (if the sites are alive) all we will see is the same fake 302 pages with redirection via their each link, deeper investigation confirming me these are URL redirectors with what looks like a given exact condition.
The challenge came by when you trace them one by one... here we go:
Threat Explanation
If you see in the picture about the one with the end page of kee.php is a CookieBomb threat, which can be set to go anywhere, you can see our previous post of the CookieBomb-->HERE, kindly bear me not to explain it further here.
One of the URL made be bump straight ahead to the RedKit URL: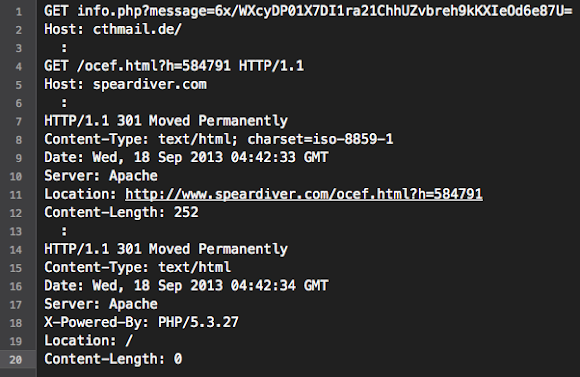
One link I trace activating the "like" script in facebook account implanted in a RBN domain, a highly suspicious domain:
With the script linked to PNG facebook icon downloaded below:
One request I followed redirect me into a TDS scheme that forwarding and forwarding me until ending up in Ukraine "hosting service" site (to make it short. I cut some http conversation) 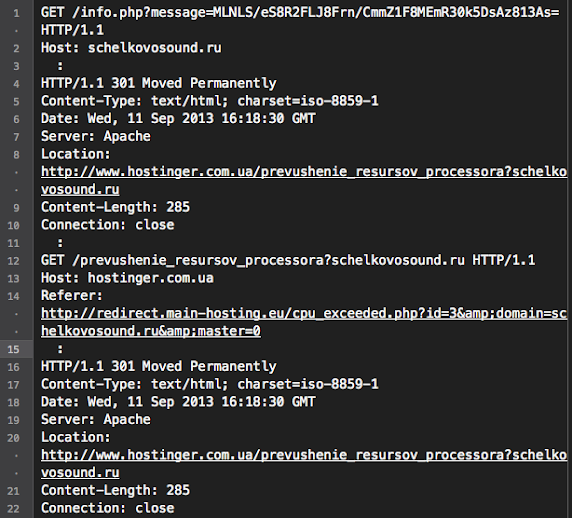

And so on..
What are these? What's the purpose?
Is not easy to explain this threat, I checked around 60-70 urls just now, come into a conclusion that these are a cushion that is used for evade web filtration/URL of IDS/IPS alerts for the following web driven attacks designed by the bad actors behind it. By the suspension of the redirection using the URL written in the rogue 302 page, the response from victim; to click the link mentioned to continue the flow of redirection/infection to next hop of the threat's site/URL; is needed.
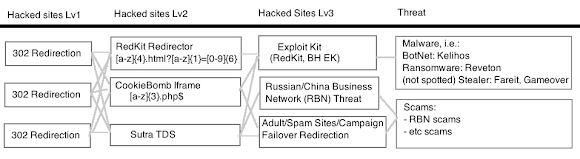
This new layer made by these rogue 302 redirection will add the link of threat chain, that's why I called it as a new "cushion for the further threat that come along behind it, I made simple graph for better understanding below:Obviously #CookieBomb now can be blocked by IDS/IDS sigs, to evade this,bad actors put a cushion of "Rogue 302 Redirection" http://t.co/L5FXaYSMXv
— (@unixfreaxjp) September 22, 2013
Proof of Concept
I collected/posted myself some urls for investigation of this case, also with other researchers posts also in there, that (again) can be seen in the URLQuery page mentioned above. The screenshot is as follows: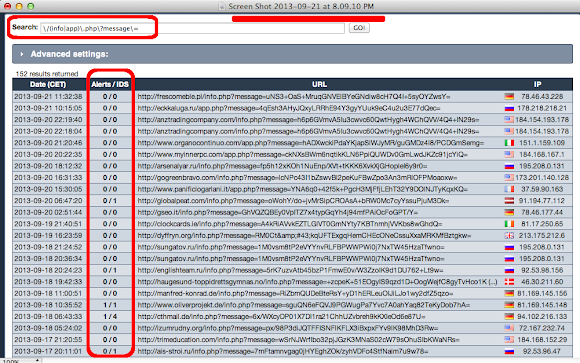
If you see the Alert in IDS/IPS column, it shows the very low detection of these rogue 302 pages, the evading was working as per expected by the scums who's planning these. I call this threat as Rogue "302-Redirectors" (as per it is..*smile*) to be use for the future reference.
If you see the end-point of the redirection and infection that can be caused by this threat, I do not surprise if the CookieBomb, RedKit and Kelihos people is behind this.
The Multiple Redirection Possibility
Speaking of the devil, the CookieBomb & TDS spread to infect Reveton that @kafeine (with thank's so much for the post) mentioned in his blog in-->HERE, contains a video demonstration of the malicious tool used to do mass-hack of exploited sites, code injection and monitoring the implemented TDS spread.
Since we know for sure that the Rogue 302-Redirectors (in short: 302redir) was created by the same actors behind the CookieBomb (and also RedKit EK and Kelihos), and in that video; as per proven in many CookieBomb hacked sites; we will know there is exist the conditional switch to be used to make multiple URL redirection happens.
You can also see in the below snapshot taken during the video running, that two URLs for forward/redirection was burped out via Jabber-base bot used in one thread of an injection scheme, it presents multiple redirection logic exists behind the tools mentioned, pic (click to enlarge):
To PoC the theory of multiple redirection is not so hard once we know how the usual threat of these types works. Our member of the development/coder department is making a very good PoC for the multiple forwarder to be used in Rogue 302 Redirector threat s per below capture:
We are terribly sorry, we can not release the whole PoC code for security reason yet, we promise to relese the code to known researchers only after threat alert level become lower.
Samples
These are the samples that I received and analysed, you can view the urls safely here-->HERE
Please be save friends, I hope this short story of awareness helps.
#MalwareMustDie!