A Step by Step Decoding Guide for CookieBomb's (as Front-end) Latest Threat, with Evil ESD.PHP Redirection (as the Back-end)
08 Nov 2013Background
Now so long ago after during my recovery (had eyes surgery recently), I posted in our paste bin a disclosure of ESD.PHP malware redirector "The Server Side's Evil Code", the link is here -->>[MMD Pastebin], it was good post and receiving many questions about it. The main questions asked obviously about (1) how ACTUALLY this threat redirector works (in actual example), and (2) how to decode (read: crack) it in practical point of view, which I took a rain-check for this quite a while. And today while sorting all of my pending research task I found the issue, so this writing hopefully answering many curiosity and can be used as reference in decoding and mitigating the similar threat.
So today we are going to play a lot with JavaScript and switch to the PHP codes.
I must warn you that I am not the natural coder of those two languages, so please bear on "my way" kind of decoding method.
Infection
It was started by a local site (as per below snapshot) that was detected to be infected by cookie bomb script infector:
Some javascript was called from this site as per captured traffic below:
Code Analysis
I found two types of CookieBomb codes was injected in that site, the older one and "a bit" recent ones (noted: plural.. since multiple injection was detected), the obfuscation is using same kind of generator, as per snipped below: It looks like not so much differences spotted between those evil codes, isn't it? 
But, after deobfuscation the differences appears, for your convenience I compared the deobfuscated codes below:
It looks obviously CookieBomb codes, so let's see where does it go. The older one goes looks already in the site for quite long so it infected EK in the site that's not exist anymore, so I skipped it.
Spoofing a CookieBomb ;-)
OK. Let's pay attention to the newer code.
Let's assemble the request for passing the correct condition and values this infector expect. Any tools or command line can be used for this purpose, I myself using any kind of method and gaining same result, but I prefer to use shell for this operation to be able to adjust here and there, the access is as per seen in the success attempt below: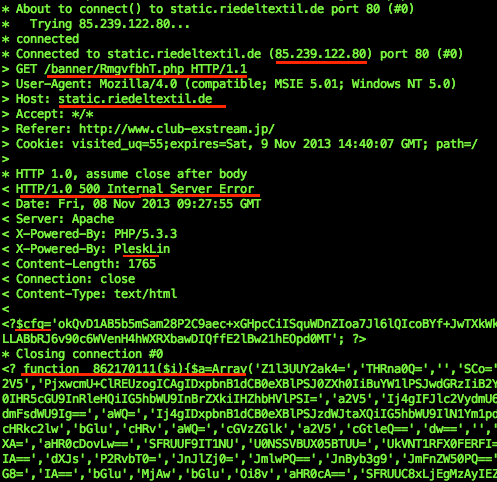
Obviously the HTTP/1.0 500 Internal Server Error was accrued, some autonatio may not getting anything after the error, but the rest of the data is all that I need, the data parts contains two blob of codes as per explained below:
Now the partial form of the ESD.PHP codes was seen, let's go and crack this. It's not so difficult.
Decoding the threat
As we saw, the two blobs of codes is not JavaScript anymore, is PHP. And is a ESD script. So let's open the reference of previous ly disclosed the server side script here-->>[MMD Pastebin]. All you have to do is basically putting the pattern I pasted in the paste bin into this one. Step by step method is:
Take the Array blob put it into the modified PHP script below: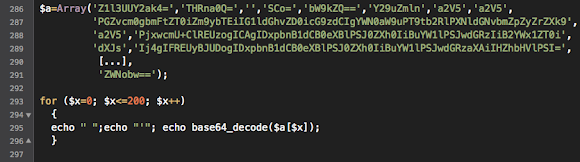
And let's run it, you'll get the value similar below, which I separated into sections for the better understanding: 
You can also simulate it into any PHP environment to find the below output:
Moving along.. we will need to fill these variables:
$key = _862170111(0);Using the "cracked key" part decoded above to know the threat actual destination (for redirection), and we need the FORM information decoded above too to know the operation performed by this threat.
$Salt = _862170111(1);
$Gamma = _862170111(2);
Now is for extracting the key parts, using the decoded array values we know that the values are:
$key = 'gYwQF6jN';Now fill those variable with its values in the below script to generate the $c, which is the key of everything:
$Salt = 'LtgkD';
$Gamma = '';
$key = 'gYwQF6jN';And all we have to do is just executing the script to get the output below:
function string_cpt($String, $Password)
{
$Salt = 'LtgkD';
$StrLen = strlen($String);
$Seq = $Password;
$Gamma = '';
while (strlen($Gamma) < $StrLen)
{
$Seq = pack('H*', sha1($Gamma . $Seq . $Salt));
$Gamma .= substr($Seq, 0, 8);
}
return $String ^ $Gamma;
}
$c = string_cpt(base64_decode($cfg), $key);
print "$c";

Let's put the values into the exact values in the cracked FORM above to fill the matrix and understanding what these are all about:

Well, obviously the infection will redirect user to IP: 5.152.200.50 and requesting access to 5.152.200.50/wds/ohlo.php, with the failover to access http://localhost/. Be noted that we need the value of KEY:'1lwk8Ch7tUUKQyO' and ID:'28435' in researching further, the below code is explaining the POST command that will be executed by using all of the above matrix's values:
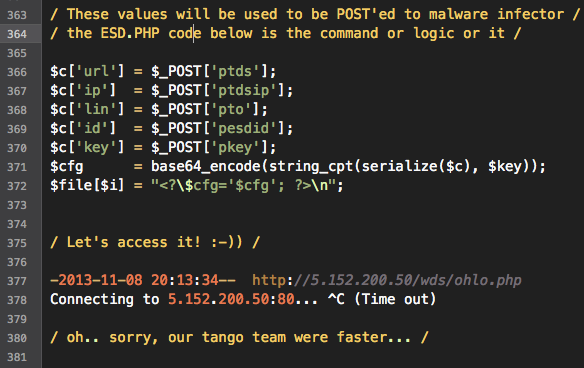
Yes, we have the redirection by reversing without simulating the infection. The point of this post is helping the IR good friends to have a reference in investigation this infection, and also by understanding this decoding method, hopefully, many filtration logic can be applied to prevent the wide infection of latest CookieBomb with using ESD.PHP logic.
#MyTwoCents Seriously. Better not activating you browser's #Cookie unless you confirm the site that inquiring it. #CookieBomb #mitigation
— MalwareMustDie, NPO (@MalwareMustDie) November 10, 2013
Epilogue
Thank's for @kafeine for the grabs for the server side codes and allowing me to pastebin-ed it, to MMD Germany team (can't mention more) for PHP codes discussion, and to all MMD folks, you all rocks.
Additionally for your information CookieBomb is a serious threat, it was operated by an automation as per snipped in the below twitter snapshot, and is related to the way much bigger threat that drives many more infection with Exploitation Tools with or without BotNets, I hope this threat also will be prioritised more.
Snapshot of #CookieBomb injection tool. See those login PWD grabbed? They #BRUTE site for #password, see panel option pic.twitter.com/NVQFyas1n0
— MalwareMustDie, NPO (@MalwareMustDie) September 24, 2013
Be free to ask in comment, it is moderated for security purpose. Ah, BTW, please don't worry for this disclosure, even though the bad actors will change the threat'S logic after I released this disclosure, their level isn't that high, and we can easily crack them again, and again, and again. Have faith friends!
#MalwareMustDie