MMD-0013-2014 - "Shadow Logger" - .NET's FUD Keylogger
02 Jan 2014Background
Our team found this threat and we decided to openly raise awareness about it. Is a Keylogger with bragging of being Fully Undetected (FUD), the sad part is, it is.. which causing the background of this disclosure. It crashed my IDA Pro during opening the bins, gotta break 2 of my RATs to run & analyze it, yes it is infected and a bad stuff that should be eliminated on the first attempt.
As per previously post also mentioned, we (read: MalwareMustDie,NPO - Anti CyberCrime & Malware Research Group) work not only in defensive way but being active to spot the threat as early stage as possible, and inviting thus support law enforcement & CERT folks to initiate the crime case upon it.
Source of the threat
During the analysis process of a new malware sample of "logger.exe" binary we received from a therat report, we figured further that the sample is the Shadow Logger, the malware keylogger binary. Checking deeper in some forums we found more details and the " sales product campaign banner" of this malware:
The longer information of the campaign info itself, which included the malicious purpose in details:


The Bad Actor's ID:
The message goes in pair with the account that promoting it. Below is the account that responsible for the threat (after while we also "suspect" that he's the coder) which is using the Skype ID of "allan.ridha" and living in Sweden:
His confession of his own Skype ID is as per below:

He is recently back to promote his malware keylogger (Shadow Logger):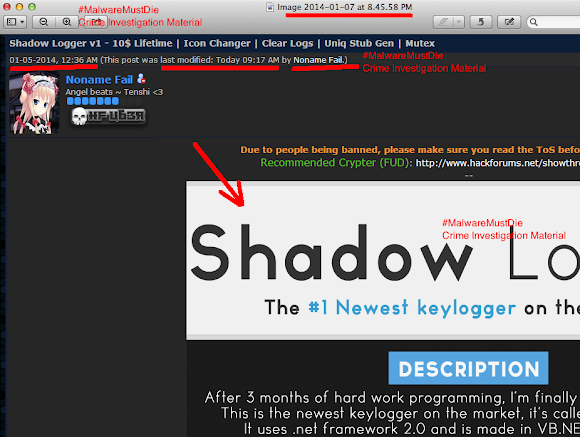

He confessed his own name here:
*) Click the image above to be redirected to the forum's google cache URL to confirm.
Trails of IP address is showing where he is: (he confessed it himself with his photo :-) )
Tracked into Sweden..

Additionally he even made a TUTORIAL to build keylogger VB malware code in HIS youtube account-->>HERE
The video in 4:23 contains his email address: allan.ridha@gmail.com
PoC picture:

Following his M.O. in using SNS we can search his Facebook and Skype account easily too.
Here's his facebook--> https://www.facebook.com/allan.ridha contains his pictures: 
In his facebook contents of timeline he is writing in swedish. so it's a proof supporting the fact that he's in Sweden.
Another proof that is showing he is living in Sweden is the example of picture the demonstration picture he is using for his keylogger which leavingthe trails of language he's living: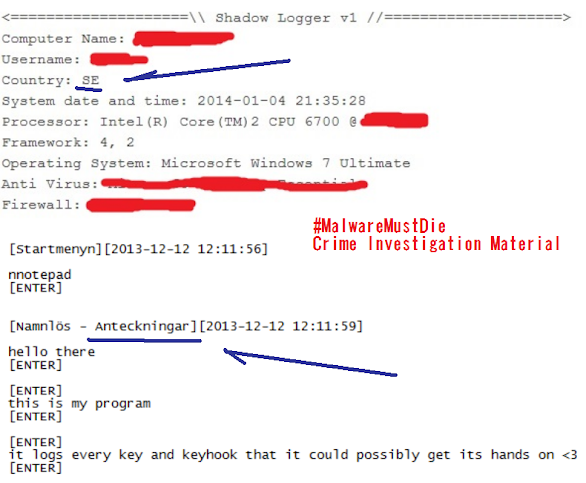 The account appeared in Skype Directory is showing same handle name used in promoting the Shadow Logger in some forums:
The account appeared in Skype Directory is showing same handle name used in promoting the Shadow Logger in some forums: 
Be free to check by yourself all of the fact above, and please don't tell us that he is innocent. Any effort to build a malware, even by SKIDS, has to be terminated as soon as possible, otherwise you won't know what he will sell and code when he is 40 year old.
Please mark this bad actor and we hope this post is giving enough verdict to LE (Law enforcement), as coder and making effort to sell/promote keylogger malware, to open a legal case against him in LE side.
@Europol_EU @jaapvoss @INTERPOL_Cyber @FBIMostWanted New #FUD #Keylogger #malware coder ID is disclosed in: http://t.co/XXfgAtvSVI #Report
— MalwareMustDie, NPO (@MalwareMustDie) January 8, 2014@Europol_EU @TroelsOerting @jaapvoss please download this video http://t.co/9a8yCPuyw9 as evidence of case: http://t.co/XXfgAtvSVI #URGENT
— MalwareMustDie, NPO (@MalwareMustDie) January 8, 2014Malware Sample & FUD PoC
This is the PoC of FUD, /* click to link to VT page */
The detection today is showing the malicious result ratio:
Antivirus Result Update
----------------------------------------------------
AVG PSW.MSIL.KNO 20140107
Ad-Aware Trojan.GenericKD.1485223 20140108
AntiVir TR/Dropper.MSIL.21049 20140107
Avast Win32:Malware-gen 20140108
Baidu Trojan.MSIL.Agent.aQh 20131213
BitDefender Trojan.GenericKD.1485223 20140108
Bkav W32.DropperArtemis.Trojan 20140108
DrWeb BackDoor.Comet.731 20140108
ESET-NOD32 variant of MSIL/Kryptik.QZ 20140108
Emsisoft Trojan.GenericKD.1485223(B) 20140108
F-Secure Trojan.GenericKD.1485223 20140108
Fortinet W32/Agent.DFZR!tr 20140108
GData Trojan.GenericKD.1485223 20140108
Ikarus Trojan-PWS.MSIL 20140108
K7AntiVirus Trojan (0001140e1) 20140107
K7GW Trojan (0001140e1) 20140107
Kaspersky Trojan.MSIL.Agent.dfzr 20140108
Kingsoft Win32.Troj.Agent.xh(kcloud) 20130829
Malwarebytes Trojan.MSIL 20140108
McAfee RDN/Generic.dx!cwd 20140108
McAfee-GW-Ed. Artemis!9E5848B5CE98 20140108
eScan Trojan.GenericKD.1485223 20140108
Panda Trj/CI.A 20140107
Sophos Mal/Generic-S 20140108
Symantec Trojan Horse 20140107
TrendMicro TROJ_GEN.R0CBC0EA814 20140108
TrendMicroHouse TROJ_GEN.R0CBC0EA814 20140108
nProtect Trojan.GenericKD.1485223 20140108
Below is the sample to share w/usual password (click the pic)
Malware Binary Analysis (Verdict)
Here's the PE:
Some encryption..
Some PE strings-->>[PASTEBIN]
It'll generate this popup:
And here is the full sysinternals record of processes executed by the sample and you can find some traces of the suspicious behaviors that usually spotted in capturing process -->>[PASTEBIN]
Below is the stacks per modules loaded:
mscorwks.dll!CreateApplicationContext+0x6d4The process after restarted showing PoC autostart:
mscorwks.dll!CorExeMain+0xa54
mscorwks.dll!ClrCreateManagedInstance+0x8aea
KERNEL32.dll!GetModuleFileNameA+0x1b4
ntoskrnl.exe!ExReleaseResourceLite+0x1a3
ntoskrnl.exe!PsGetContextThread+0x329
ntoskrnl.exe!FsRtlInitializeFileLock+0x83f
ntoskrnl.exe!FsRtlInitializeFileLock+0x87e
win32k.sys+0x2f52
win32k.sys+0x3758
win32k.sys+0x3775
ntdll.dll!KiFastSystemCallRet
USER32.dll!GetCursorFrameInfo+0x1cc
USER32.dll!SoftModalMessageBox+0x677
USER32.dll!MessageBoxIndirectA+0x23a
USER32.dll!MessageBoxTimeoutW+0x7a
USER32.dll!MessageBoxExW+0x1b
USER32.dll!MessageBoxW+0x45
System.Windows.Forms.ni.dll+0x2b5cd3
System.Windows.Forms.ni.dll+0x2b58e8
ntoskrnl.exe!ExReleaseResourceLite+0x1a3
ntoskrnl.exe!PsGetContextThread+0x329
ntoskrnl.exe!FsRtlInitializeFileLock+0x83f
hal.dll+0x2c35
mscorwks.dll!CorExeMain+0x17b3
mscorwks.dll!InitializeFusion+0x118ab
mscorwks.dll!InitializeFusion+0xf65b
mscorwks.dll!InitializeFusion+0xfa44
mscorwks.dll!InitializeFusion+0xf855
mscorwks.dll!InitializeFusion+0xfcba
mscorwks.dll!GetCLRFunction+0xe4b2
mscorwks.dll!CorLaunchApplication+0x24aa9
mscorwks.dll!NGenCreateNGenWorker+0x2f12f
mscorwks.dll!InstallCustomModule+0x8697
mscorwks.dll!InstallCustomModule+0x853d
mscorlib.ni.dll+0x2a31b3
The Autostart trace:
\REGISTRY\USER\S-1-5-21-1214440339-926492609-1644491937-1003\With the below command line (cmd):
Software\Microsoft\Windows\CurrentVersion\Run
"C:\WINDOWS\system32\cmd.exe" /c reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run"The .NET components in memory:
/f /v "gens" /t REG_SZ /d "C:\Documents and Settings\Administrator\Local
Settings\Temp\breakfast.exe"
Some registry calls dumped from malware's memory area-->>[PASTEBIN]
The memory was mapped by these libraries:
C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\culture.dllAdditionally the registry change values:
C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\mscorjit.dll
C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\mscorrc.dll
C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\mscorwks.dll
C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\mscoreei.dll
C:\WINDOWS\WinSxS\x86_Microsoft.VC80.CRT_1fc8b3b9a1e18e3b_8.0.50727.1433_x-ww_5cf844d2\MSVCR80.dll
C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.5512_x-ww_35d4ce83\comctl32.dll
C:\WINDOWS\WindowsShell.Manifest
C:\WINDOWS\assembly\GAC_32\mscorlib\2.0.0.0__b77a5c561934e089\sortkey.nlp
C:\WINDOWS\assembly\GAC_32\mscorlib\2.0.0.0__b77a5c561934e089\sorttbls.nlp
C:\WINDOWS\assembly\NativeImages_v2.0.50727_32\System.Drawing\c91f68c2920882e02aec00eeabb6b415\System.Drawing.ni.dll
C:\WINDOWS\assembly\NativeImages_v2.0.50727_32\System.Windows.Forms\0c70e5d82578be2f6c0dde89182261c5\System.Windows.Forms.ni.dll
C:\WINDOWS\assembly\NativeImages_v2.0.50727_32\System\36dbfcf62e07d819b3de533898868ecf\System.ni.dll
C:\WINDOWS\assembly\NativeImages_v2.0.50727_32\mscorlib\642534209e13d16e93b80a628742d2ee\mscorlib.ni.dll
C:\WINDOWS\system32\CLBCATQ.DLL
C:\WINDOWS\system32\COMRes.dll
C:\WINDOWS\system32\MSCTF.dll
C:\WINDOWS\system32\RichEd20.dll
C:\WINDOWS\system32\SETUPAPI.dll
C:\WINDOWS\system32\WININET.dll
C:\WINDOWS\system32\cmd.exe
C:\WINDOWS\system32\comctl32.dll
C:\WINDOWS\system32\imm32.dll
C:\WINDOWS\system32\l_intl.nls
C:\WINDOWS\system32\mscoree.dll
C:\WINDOWS\system32\rpcss.dll
C:\WINDOWS\system32\shdocvw.dll
C:\WINDOWS\system32\shell32.dll
C:\WINDOWS\system32\urlmon.dll
C:\Windows\AppPatch\sysmain.sdb
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{a1094da8-30a0-11dd-817b-806d6172696f}\ New Value: [ Drive ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{a1094daa-30a0-11dd-817b-806d6172696f}\ New Value: [ Drive ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders New Value: [ C:\Documents and Settings\Administrator\Application Data ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders New Value: [ C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders New Value: [ C:\Documents and Settings\Administrator\Cookies ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ New Value: [ 1 ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ New Value: [ 1 ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ New Value: [ 1 ]
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Windows\CurrentVersion\Run New Value: [ gens = C:\Documents and Settings\Administrator\Local Settings\Temp\breakfast.exe ] I will update upon fixing my RAT, the data above are ones that I could recover so far. Be free to make your good analysis of this keylogger FUD.
Mr. Marc Ochsenmeier (@ochsenmeier/twitter), the author of binary analysis PEStudio, was helping us in checking Shadow Logger (w/thank's) in PEStudio as per below tweets:
"Shadow Logger" viewed by PeStudio, with "hints" of suspicious intent... pic.twitter.com/GZpyRUu2ou
— Marc Ochsenmeier (@ochsenmeier) January 2, 2014@ochsenmeier the same "Shadow Logger" with more details... pic.twitter.com/GcXOjJpLO3
— Marc Ochsenmeier (@ochsenmeier) January 2, 2014The Malware's Source Code - Crime Evidence
After digging a little further we "secured" the source code of this malware, this source code is passed to the AV industry, well-known malware researchers and law enforcement only.
Download -->>[HERE]
Mirror Download -->>[HERE]
read instruction in the video to unlock.
Additional:
#MalwareMustDie Intelligence Case: ShadowLogger bad actor erased evidence :-) #PoC we hit jackpot + we got his all ID pic.twitter.com/3EWigPNP1M
— MalwareMustDie, NPO (@MalwareMustDie) January 9, 2014Thank's to our crusader for very good detection & investigation!
#MalwareMustDie!