MMD-0016-2014 - The JackPOS Behind the Screen
13 Feb 2014The background
As the credit for the current threat's awareness, a lot of you probably noticed the JackPOS malware's posted at: Xylit0l's post in Kernel Mode here -->>[kernelmode], in the IntelCrawler press release here -->>[IntelCrawler], and Josh Grunzweig's analysis on Trustwave Spiderlabs here -->>[LINK]This post is an additional intelligence data supporting to the threat's technicalities written in the main investigation of the threat by the above mentioned gentlemen, it is our shares which may help law enforcement to aim better cannon directly to the bad actors (read: Moronz) who is actively in effort on selling and promoting the threat, the one behind the distribution of JackPOS malware scene.
As per always mentioned in previous posts, we (read: MMD / MalwareMustDie,NPO - Anti CyberCrime & Malware Research Group) work not only in defensive / mitigating way against the threat, but being proactive to spot the root of threat as early stage as possible, and inviting thus support law enforcement & CERT folks to initiate the crime case upon it.
DarkK0de (DK) Crook's Forum
This information was all compiled from our eyes in the DK forum. It was stated the promotion, the testing information, screenshot, latest specification of the JackPOS (furthermore I will refer it as "the product"), the screenshots and the contact information of the bad actor (read: moronz) behind it. I am sorry, after "internal discussion" it was decided not to paste DK forum screenshots itself, since that will raise the risk in blowing away our intelligence channel.
What we posted here may help to add more image & information of the "product" design of JackPOS, to the one that IntelCrawler, Xylit0l & Josh were working hard on analyzing it, in the following sections. To be noted, please understand, we are not adding more technicality details..but adding the campaign product design data, and also we are not aiming fame or riding on the flux of news for this threat. It's just that we did not see the right aim on clues of on-going investigation on the threat's source so far, so this is the share to lead law enforcement friends to aim closer to the target, the right "crook's forum" as the source of this malware campaign: "The DarkK0de".
And for you, the all malware crooks that I know that you're reading this post too, we want to let you know, MMD is different, WE BREATH BEHIND YOUR NECK! and we mean it, no matter how tight your "poor security" environment for a so-called a gathering buff (a.k.a. "forums"? ..whatever..) is. Just STOP NOW your malicious activity before is getting too late! Go and get a decent day work like all of us and live a decent life without fear. Consider this as a warning.
OK, the main course:
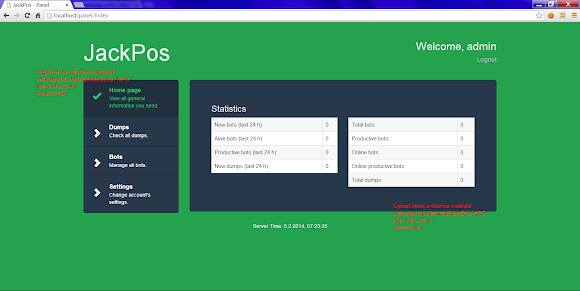
Screenshots
What DK was posting screenshots is as per it is:
Promotion Thread
Malware: (functions & specs)
- Coded in modern c++
- Size 145 kbytes (upx packed)
- Small resource usage, ~90% of time 4 mbytes RAM and 0-2% cpu usage
- Doesn‘t use regular expressions
- Grabs track1/track2
- Update / Execute virus
- Process persistence, if process closed, automatically will start again
- Registry persistence, if registry key deleted or changed, it` restored
- Very stable and well tested
- Same track1/track2 won't be sent second time to panel (saved hashed of
dumps in a file)
- Once it founds processes with valid data, the virus scrap just them in -
a loop of 100 times, then rescan all the processes till it finds
productive ones. (Done in one thread for stability)
Product Updates:
The new version of virus have some new features that the old one doesn't:
- Support of Unicode dumps in processes
- Much more stable
- Improved panel (issues with archivation of dumps and bots),
also changed exporting
- Once it founds processes with valid data, the virus scrap just them
in a loop of 100 times, then rescan all the processes till it finds
productive ones. (Done in one thread for stability)
The Price:
1 bin = 1,5K BTC
The seller / tester contact information
As per se:
Seller jabber: mindark@jabbim.comthis Rome0 guy is a well know carder and scammer, with the below contacts (Kudos MMD DE team!)
Tester jabber: Rome0@Darkode.com
ICQ 22222193
Jabber 22222193(at)jabber.cz
Prologue
The above information is enough to lead the law enforcement to perform the action to get the real actors ID behind the screen. It is reachable, and all we pass it to the justice.
Herewith we are backing off on the investigation and intelligence of this case for the law to follow properly.
MalwareMustDie, NPO., is not owning any source code / samples / reversing data for this threat, we are posting this to support other entities mentioned above for this investigation exclusively, so please ask the mentioned front liner posters for the the further details.
Credit: Kudos MalwareMustDie Intel Dept, InterCrawler (link), Xylibox (link) & Josh Grunzweig (link).
Q & A:
@jgrunzweig Finishing check, Josh. I think we hit seller & not coder. Stuff like this goes in pair in campaign. Nice WriteUp! /cc: @Xylit0l
— MalwareMustDie, NPO (@MalwareMustDie) February 13, 2014#MalwareMustDie!, we repeat "MUST!!" die. We're on it.
This post is dedicated to MMD Georgia Crusaders.