DDoS'er as Service - a camouflage of legit stresser/booter/etc
09 Jun 2014The background
After visiting some hacked FTP sites as per reported in the previous posts [-1-] and [-2-] , I figured out connection that some IRC scripts running leads to the group/individuals performing a DDoS'er attack services. I personally found it interesting to check thorough and deeper to its source, so this weekend I made a visit to DDoS'er as services with some records on of their malicious activities. The reason is simply investigation to confirm some segment of IPs gathered from previous cases to these services. During the trip I made memo in here and there so this post will gather it all for the easier search. So it is not about bragging anything to anyone, just a share.This is an explanation on why we are aiming "some" #DDoS'er/booters/stresser recently: http://t.co/pdXPBuJGbl
#MalwareMustDie via @reddit
— MalwareMustDie, NPO (@MalwareMustDie) June 11, 2014DDoS as Service
DDoS and their services are not a new stuff. These services are cleverly hiding their maliciousness under the words of "for education" or "for tester" and so on, in their promotion or TOS statement written in their public home pages or via description in the demonstration videos they uploaded to some video sites. However, if you see some XXX and YYY communities where hackers are gathered, these services are making strong campaign in a very different tone, the usage of terms like "powerful", "hit", "takedown" and so on came up in the surface that are suggesting attack tools in promotion. Further, we can see screenshots of "success attack" in real cases that were openly shared to proof how "powerful" their services are. The video posted in here will explain more than words of the previous statements. So the market is there, with youngsters are in majority, and we can say it is a fruitful steady money to catch, explaining the competitive promotion.
Among tons of "DDoS'er As Service" spotted, the below list is some that I picked to study. I extracted their campaign and details information in the snapshots of campaign images & videos in the next section, some are including a bit of comments.
NetGuard
Big Bang Booter
Critical Stresser
Wrath Stresser
Apocalypse Stresser
Titanium Stresser
Collected Items
For MMD friends' who like this collection, I gathered some of the campaign materials they are using. Well, they really love to use a real (literally..in size) long promotion which mentioning similar terms in pricing, duration on service and TOS. With reckoning one same term that they all used: a no refundable payment :-)
In a short limited time I can managed to compile videos of these services that contains the demonstration (to be clear: is what they provided, not me), is a quite good reference for learning what these are actually about:
Some DDoS/Stresser/Booter terms to know..
During investigation on these attacker services, finally I also learned a "trend" of recent terms used by these DDoS'er with the correct explanation collected below which can be used as quick reference for the attack method or in the scripts that they are using during checking infected sites by these attacker's front end tools. We mentioned the same explanation in previous post in investigating their attacker scripts, but this explanation is more accurate, is a very good know how to know :
1. UDP Flood
Is a DoS to flood the target with the varius combination of UDP packet, a sessionless/connectionless computer networking protocol. Thi sattack is effectively working for the home connections. UDP flood are applified by script (program) and that can be amplified to over 20Gbps, practically to make the target is as good as offline.2. Chargen
Chargen is another UDP type flood attack, working effectively on using port 8080 for optimal results. This atack is generated by Chargen script logic (PHP/Perl/C) that can be amplified over 20Gbps. The target is the Chargen (port 19) service which derrives the name, can be spoofed into sending data from one service in a computer to another service on another computer. This attack can consume incleasing amount of network bandwith causing loss of performance or a total shutdown of the affected network segments. This attack can disable a unix server by causing it to spend all of its time processing UDP packets that it has echoed back to itself.3. UDPLag:
Just like UDP flood but this attack will not hit the target offline, instead it will make them lag.4. ESSYN Flood
Applified spoofed SYN attack that abuses the TCP 3-way handshake by never responding to the target's TCP confirmation response, made it wait for the handshake done indefinitely.5. Slowloris
An extremely useful method of attack to webservers running Apache, Tomdat and GoAhead. By keeping as many as possible connections open for as long as possible by only sending partial requests and thus blocks access to the server for other clients.6. Rudy (R U Dead Yet)
By sending small packets of 1 byte through a HTTP POST request it will force the connection with the server to stay open. RUDY is harder to detect and prevent.7. ARME
ARME is considered a layer 4 attack method. It is pretty strong due to it eats up all of the SWAP memory of a servers runs Apache, eventually letting it flood the HDD resulting into out of operation and the server services will be shutdown.8. Resolver
This is not the attacker techniques but the common function of the DDoS'er tool that exists in the market nowaways to resolve (8.1.) Real IP address of the Host protected behind the Cloudflare service, (8.2.) Real IP address of the Skype users, to perform the above attacks.DDoS Source Code (L7+L4) & Amplification IP list
Along with the investigation we collected and secured the recent source codes that has been used for DDoS activities, together with its companion the amplification IP address list, and also grabbed some know how that's been shared in the xxx lair by the skids and hackers. Below is the video of what is shared, check it first to make sure that you need it or not:
The download for the package (5.32 MB) is here-->>[Secure Code: 777022].
You will need the password for the archive, so please put comment in the bottom of this post for the request & explaining a bit about who you are, why you need the source code, and where we can contact you (no comment will be published).
The purpose of the sharing is to raise scan detection ratio for those codes/scrips/binaries, forwarding the knowledge used by attacker to the DDoS prevention entities, a share to the security community who's fighting this threat. We don't take any responsibility of the mis-used of the shared material passed to the unknown third parties.
Epilogue
In the end, this information hopefully to explain how DDoS is served and how DDoS is always on operation. Also how some of these services are wrapped with a simple GUI to be used for the attack. Suspending domain or mitigating DDoS services like these is not making much effect, and we need more firm act to stop individuals and infrastructure used to perform it. They are using common domains, web sites, even YouTube for promotion, moreover some of them are using known DDoS protection service to guard their DDoS'er sites (see below picture), it's just went too far, and maybe now is a right time to say "STOP". 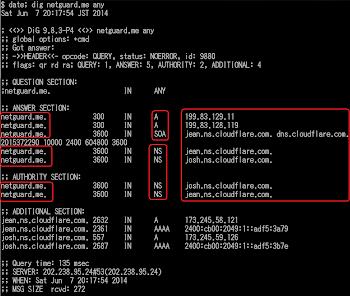
But stopping these are easy to be said than done. I was thinking that maybe we need to push this awareness more to raise the importance in making a smoother scheme to fight this threat, hoping this post and other similar previous posts by others of this issue can escalate the process.
Kudos twitter friends with great comments!
Thank's to DOMAIN.ME & PW Registry for the instant suspensions. Thank you so much to these cool IT guys: @cesi0_ @DarkSunsetSX @NotBluntMan @BugTracK @LibidinousPrick @jedisct1 @VriesHD @whalezeye and all friends that favorites and RT, for the great support & comments during the trip (see below). And to MMD team: @essachin @malm0u53 @wirehack7 @MichalKoczwara for the support & for tango help!
. @MalwareMustDie thanks for letting us know! We've started the investigation.
— domain .ME (@domainME) June 7, 2014Lol Pics of the day . #MalwareMustDie #DDOS pic.twitter.com/rCOz7CmvJQ
— sachin (@essachin) June 9, 2014@MalwareMustDie @jedisct1 Most of the kids running these are teenagers. Just find them and call their parents up. I'm sure that'd stop them.
— BluntMan (@NotBluntMan) June 8, 2014#DarkSunset Twitter / jedisct1: @MalwareMustDie pic.twitter.com/5bnjWviOLL pic.twitter.com/Y6BtyQdsyu, see more http://t.co/vjd9kLnke5
— Dark Sunset (@DarkSunsetSX) June 8, 2014@MalwareMustDie Haha "wanna be hackers" #fail
— Michal Koczwara (@MichalKoczwara) June 8, 2014@domainME @MalwareMustDie My mom hits harder than those kids! Pun intended.
— BugTracK (@_BugTracK) June 8, 2014@MalwareMustDie cool, musta been the smoke-clouds from toasted moronz ~ best wishes for yer health
— whalezeye (@WhalezEye) June 8, 2014@MalwareMustDie They provide servers specially for running your own DDoS service. I guess they have a few resellers.
— Frank Denis (@jedisct1) June 7, 2014@MalwareMustDie correction - BIGbang is up BINGbang is not.
— ␀ (@cesi0_) June 7, 2014@VriesHd @MalwareMustDie every android app is a potential botnet. By design. Google ibecame the ultimate botnet with android API.
— Albrecht (@LibidinousPrick) June 7, 2014@MalwareMustDie @LibidinousPrick Well I've had my doubts on a few to be fair. I mean, it's a good way to scout the bad ones..
— Kira 2.0 (@VriesHd) June 7, 2014@MalwareMustDie many DaaS like this.
— trudulu (@trudulu) June 7, 2014@MalwareMustDie https://t.co/dd0FqOGfGv blacklisted as Malicious site
— Malwared (@Malwared_) June 7, 2014@DaveMarcus @Tinolle1955 @MalwareMustDie I get a lot of "timed-out" stuff on my browser. But no DDoS attack. How is that different?
— CyberProwl! (@F706L3665) June 7, 2014@MalwareMustDie Pay to get DDoS'ed, one way to get attention lolz....
— Doctor No (@DoctorNoFI) June 7, 2014@MalwareMustDie @CloudFlare CloudFlare guards w/o bothering w site content.That's the tactic they use to grow their biz. W/O responsibility.
— RealName GoesHere (@vxer) June 7, 2014@vxer @MalwareMustDie @CloudFlare It's the same path most domain registrars take. They're not legally obliged to take action, so they won't.
— MalwareTech (@MalwareTechBlog) June 7, 2014@MalwareMustDie most if not all of these are law enforcement traps from our criminal system of justice.
— Albrecht (@LibidinousPrick) June 7, 2014@MalwareMustDie So you're looking into HackForums booters? I know a while ago they were recommending ecatel highly for attack scripts etc.
— formerly Wack0 (@TheWack0lian) June 10, 2014@LibidinousPrick @MalwareMustDie If only that was true.
— Kira 2.0 (@VriesHd) June 7, 2014@NotBluntMan @MalwareMustDie @jedisct1 http://t.co/5nqzncAc1F speaking of ddos, nice perl script you had on the zimbra's nikolas
— DigitalFelon (@digitalfelon) June 8, 2014Stay safe folks! #MalwareMustDie!





