MMD-0033-2015 - Linux/XorDDoS infection incident report (CNC: HOSTASA.ORG)
24 Jun 2015Background
This post is an actual malware infection incident of the"Linux/XOR.DDoS" malware (please see previous post as reference-->[LINK]) and malware was in attempt to infect a real Linux server.
Incident details:
Source of attack:
An attack was coming from 107.182.141.40 with the below GeoIP details:
"ip": "107.182.141.40",
"hostname": "40-141-182-107-static.reverse.queryfoundry.net",
"city": "Los Angeles",
"region": "California",
"country": "US",
"loc": "34.0530,-118.2642",
"org": "AS62638 Query Foundry, LLC",
"postal": "90017",
"phone": "213"
The attacker was compromising a Linux host via ssh password bruting as per below evidence:
[2015-06-23 01:29:42]: New connection: 107.182.141.40:41625
[2015-06-23 01:29:42]: Client version: [SSH-2.0-PUTTY]
[2015-06-23 01:29:43]: Login succeeded [***/***]
..to then executing a one liner shell (sh) command line below:
..and then the malware initiation commands was executed on the compromised system:
The attacker used web server's (domain:44ro4.cn) panel screenshot taken at the time the attack was in progress:
The IP info of this panel:
(Additional) The domain information:
"ip": "198.15.234.66",
"hostname": "No Hostname",
"city": "Nanjing",
"region": "Jiangsu",
"country": "CN",
"loc": "32.0617,118.7778",
"org": "AS11282 SERVERYOU INC",
"postal": "210004"
Below is more proof of the domain's used, a check mate:
;; QUESTION SECTION:
;44ro4.cn. IN A
;; ANSWER SECTION:
44ro4.cn. 600 IN A 23.228.238.131
44ro4.cn. 600 IN A 198.15.234.66
;; AUTHORITY SECTION:
44ro4.cn. 3596 IN NS ns2.51dns.com.
44ro4.cn. 3596 IN NS ns1.51dns.com.
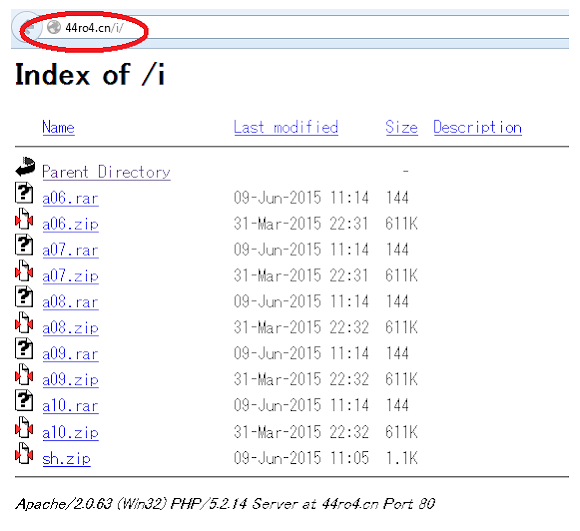
Infection method, camouflages and overall summary
I examined further the infection source, what it seems is not what it is at all, what looks like zip archives are ELF malware, and what looks like zips are a shell script malware installers, to be clear, see the illustration below:
Rule number 1 in MMD is : Always check under the hood :) 
So the bad actor is making a pair of installer and faked it as zip and downloading the exactly same filename of ELF faked as rar. The reason for faking these archives is simply to avoid the filename blocking from several firewall/IDS filtration. This is just unbelievably irritating, isn't it?
This is the Linux/XorDDOS malware we posted before-->[LINK], the post-infection of this malware made the infected machine to act as bot, remotely controlled for malicious process, config, deny IP, daemon and configurations. They are using XOR'ed encryption communication, processes are sent with md5 encoded beforehand. The main function of this malware ELF is for a stealth DDoS attacker botnet.
The important highlight of this incident and the malware used are:
(1) The usage of US infrastructure used for this malware infection (attacker IP from US host, one IP of panel used for infection, two servers for CNC, with the abuse of .ORG domain registration) with the new scheme worth to be exposed & followed in as incident response and awareness of what this threat does. And all of these just happened about 12h ago..
(2) The usage of multiple hosts in this Linux/XorDDoS, in total: four CNCs. Three of those CNCs are hard coded in hostnames (has domain related) and are receiving the callback from the infected machine, while one of the host is functioned as download server which the infected machine is requesting backdoor to download suspected malicious files.
(3) XOR encryption function is used now to decrypt the drops, reading the configuration file downloaded from the remote hosts (yes, what it downloaded seems to be the config file), and for sending the CNC communication data.
Here is the PoC:
These are the CNC interactive calls trapped in the kernels:
Those calls' DNS requests:
- in tcpdump with the timestamp:
08:21:20.078878 IP mmd.bangs.xorddos.40274 > 8.8.8.8: 27458+ A? aa.hostasa.org. (32)
08:21:20.080602 IP mmd.bangs.xorddos.38988 > 8.8.8.8: 44387+ A? ns4.hostasa.org. (33)
08:21:25.092061 IP mmd.bangs.xorddos.45477 > 8.8.8.8: 58191+ A? ns3.hostasa.org. (33)
08:21:25.269790 IP mmd.bangs.xorddos.51687 > 8.8.8.8: 22201+ A? ns2.hostasa.org. (33)
Calls to CNC establishment, I pick only one, each callback does this, noted the way it uses Google DNS:
The CNC callback traffic was encrypted, here is the initial callback taken from two separate environments:
Some decrypting for memo:
Here is what coded in the binary for this part:
..yes, the download function is hard coded in binary:
And also the hard evidence in traffic too:)
Interesting facts
These are the malware project source code files used, it is the set of Linux/XOR.DDoS compile set (in C, without "++"), this went straight to my collection libraries for the future reference, thank's to the bad actor and have a nice day to this malware's coder :-))
The malware autorun installer shell script hard coded in the binary, this is so generic..many ELF malware made in China is using this concept:
The one of typical characteristic of malware is the self-copy to /tmp directory on regex '[a-z]{10}'< this can be used to mitigate the initial execution actually:
Spotted the XOR encryption to be run from installer and "supposedly" to be used on decrypting configuration data, in the sample I cracked the key is BB2FA36AAA9541F0
This is the usage of the encryption above during the installation to self copy the malware file, for reversers, see the comment & trail the code:
-and this..
The ACL function (to deny access by IP) to protect the infected hosts:
Investigation for legals & cleanup process:
The hosts serving CNC are as per checked in the DNS record below:
;; ANSWER SECTION:
aa.hostasa.org. 300 IN A 23.234.60.143
ns2.hostasa.org. 300 IN A 103.240.140.152
ns3.hostasa.org. 300 IN A 103.240.141.54
ns4.hostasa.org. 300 IN A 192.126.126.64
;; AUTHORITY SECTION:
hostasa.org. 3600 IN NS ns4lny.domain-resolution.net.
hostasa.org. 3600 IN NS ns1cnb.domain-resolution.net.
hostasa.org. 3600 IN NS ns3cna.domain-resolution.net.
hostasa.org. 3600 IN NS ns2dky.domain-resolution.net.
;; ADDITIONAL SECTION:
ns3cna.domain-resolution.net. 2669 IN A 98.124.246.2
ns2dky.domain-resolution.net. 649 IN A 98.124.246.1
ns1cnb.domain-resolution.net. 159 IN A 50.23.84.77
ns4lny.domain-resolution.net. 2772 IN A 98.124.217.1
Up and alive CNCs are in USA:
These other two CNCs are allocated in Hongkong network:
"ip": "23.234.60.143",
"hostname": "No Hostname",
"city": "Newark",
"region": "Delaware",
"country": "US",
"loc": "39.7151,-75.7306",
"org": "AS26484 HOSTSPACE NETWORKS LLC",
"postal": "19711"
"ip": "192.126.126.64",
"hostname": "No Hostname",
"city": "Los Angeles",
"region": "California",
"country": "US",
"loc": "34.0530,-118.2642",
"org": "AS26484 HOSTSPACE NETWORKS LLC",
"postal": "90017"
"ip": "103.240.140.152",
"hostname": "No Hostname",
"city": "Central District",
"country": "HK",
"loc": "22.2833,114.1500",
"org": "AS62466 ClearDDoS Technologies"
"ip": "103.240.141.54",
"hostname": "No Hostname",
"city": "Central District",
"country": "HK",
"loc": "22.2833,114.1500",
"org": "AS62466 ClearDDoS Technologies"
The domain HOSTASA.ORG is beyond doubt proven to be used for this malicious purpose, three hostnames fake themself with hostname to look like a DNS servers, which is NOT. Below is the registration data from NAME.COM where it is registered as .ORG, with the Privacy Protection:
Domain Name:"HOSTASA.ORG"
Domain ID: 2D175880649-LROR"
"Creation Date: 2015-03-31T06:56:01Z
Updated Date: 2015-05-31T03:45:36Z"
Registry Expiry Date: 2016-03-31T06:56:01Z
Sponsoring Registrar:"Name.com, LLC (R1288-LROR)"
Sponsoring Registrar IANA ID: 625
WHOIS Server:
Referral URL:
Domain Status: clientTransferProhibited -- http://www.icann.org/epp#clientTransferProhibited
Registrant ID:necwp72276k4nva0
Registrant Name:Whois Agent
Registrant Organization:Whois Privacy Protection Service, Inc.
Registrant Street: PO Box 639
Registrant City:Kirkland
Registrant State/Province:WA
Registrant Postal Code:98083
Registrant Country:US
Registrant Phone:+1.4252740657
Registrant Phone Ext:
Registrant Fax: +1.4259744730
Registrant Fax Ext:
Registrant Email:hostasa.org@protecteddomainservices.com
Tech Email:hostasa.org@protecteddomainservices.com
Name Server:NS3CNA.DOMAIN-RESOLUTION.NET
Name Server:NS1CNB.DOMAIN-RESOLUTION.NET
Name Server:NS2DKY.DOMAIN-RESOLUTION.NET
Name Server:NS4LNY.DOMAIN-RESOLUTION.NET
DNSSEC:Unsigned
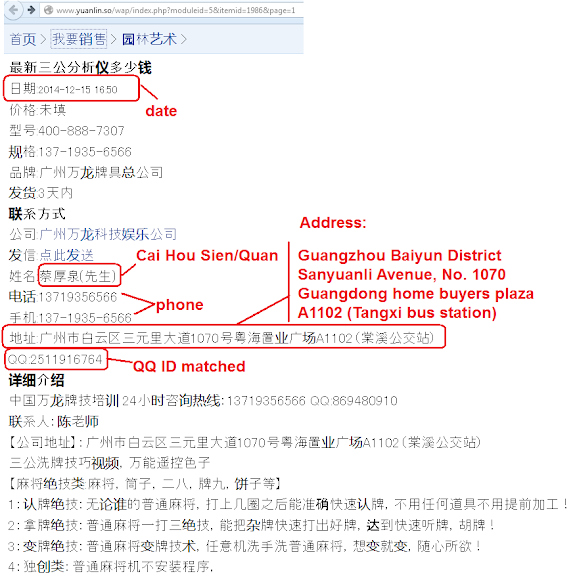
Additionally, for the 44RO4.CN domain used, which is registered in DNS pointing to the malware payloads web panel, that is not a coincidence, it is registered under below QQ ID and (maybe fake) name;
Domain Name: 44ro4.cnps: CNNIC has more information of this registration, I took liberty to query them to find this crook is using the same and other ID to several poor reputation .CN domains, under the same and different name too, on the same QQ:
ROID: 20141229s10001s73492202-cn
Domain Status: ok
Registrant ID: ji27ikgt6kc203
Registrant: "蔡厚泉 (Cai Hou Sien/Quan)"
Registrant Contact Email: "2511916764@qq.com"
Sponsoring Registrar: 北京新网数码信息技术有限公司
Name Server: ns1.51dns.com
Name Server: ns2.51dns.com
Registration Time: 2014-12-29 10:13:43
Expiration Time: 2015-12-29 10:13:43
DNSSEC: unsigned
Domain RegistrantID NameAnd after seeking for a while, all of these reference lead to the individual identification here:
------------------------------
n1o9n.cn ej55v35357p95m 沈涛
u7ju0.cn ej55v35357p95m 沈涛
568b5.cn ej55v35357p95m 沈涛
93t9i.cn ej55v35357p95m 沈涛
5ntdu.cn ej55v35357p95m 沈涛
v90b8.cn ej55v35357p95m 沈涛
av732.cn ej55v35357p95m 沈涛
iqny7.cn ej55v35357p95m 沈涛
ewkp7.cn ej55v35357p95m 沈涛
8vu55.cn ji27ikgt6kc203 蔡厚泉
tj17e.cn ej55v35357p95m 沈涛
o88pn.cn ji27ikgt6kc203 蔡厚泉
Which is living nearby the Tanxi Bus Station in Sanyuanli street, Baiyun district, Guangzou prefecture, PRC, as per described in ths map:
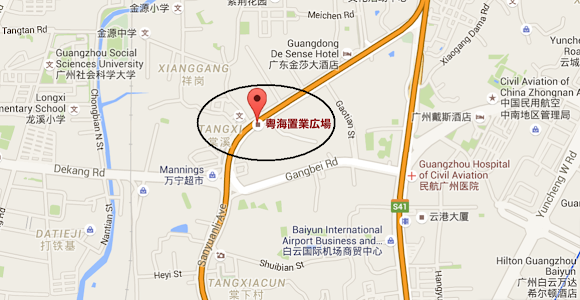
I will leave this data for the authority to follow this lead further.
Detection ratio and samples
ELF samples are all in Virus Total with the below links:
(a06.zip) = 3c49b5160b981f06bd5242662f8d0a54
(a07.zip) = bcb6b83a4e6e20ffe0ce3c750360ddf5
(a08.zip) = a99c10cb9713770b9e7dda376cddee3a
(a09.zip) = d1b5b4b4b5a118e384c7ff487e14ac3f
(a10.zip) = 83eea5625ca2affd3e841d3b374e88eb
Fellow researchers & industry can grab the sample from kernelmode here-->[LINK]
#MalwareMustDie!
