MMD-0035-2015 - .IptabLex or .IptabLes on shellshock.. sponsored by ChinaZ actor
01 Jul 2015The background
.IptabLex & .IptabLes ELF DDoS malware is the malware made by China DDoSer crime group, designed to infect multiple architecture of Linux distribution, was aiming for Linux boxes in the internet with the low security and authentication flaw in SSH as vector of infection, was an emerged ELF threat in 2014.Historically, MalwareMustDie, NPO (MMD) is the first entity who detected this malware around May last year and named it as Linux .Iptablesx|s on our last year's alert MMD-0025-2014 [link] released on June 15, 2014. And we build malware repository for this ELF family for sharing samples and trend for researchers and industries on kernelmode started from September 4th 2014 [link], since the threat was gone so wild at the time and there was so few information about this malware that causing low awareness and detection ratio, so we managed all we can to suppress the growth of infection rate.
The DDoS attacks originated from this malware, in quantity of incidents and traffic used, was so massive in 2014 causing some warning was released from important security entities in September 2014, as per announced by Prolexic (thank you for mentioning MalwareMustDie) [link] in their Threat Advisory with "High Risk" level, following by Akamai's warning referred to the Prolexic's advisory announcing the world wide warning [link] of .IptableS|X.
Afterward, Linux .IptableS / .IptablesX ELF malware was still be detected in the wild until the end of October 2014, but since November 2014 we did not find any significant wave of infection using these family, wiped by the emerge of many other China DDoS new malware families that we detected also afterwards. From the early this year (January 2015), we started to assume the malware popularity and development of .IptabLes|x was stopped..
However, on June 27th 2015 I was informed in the twitter by a friend @TinkerSec for what was suspected as Linux/ChinaZ infection. I supported him with ELF binary sample's "real time" analysis in twitter as per shown in his report below:
Malware Detection & Analysis - Discovery by @TinkerSec & Analysis by @MalwareMustDie - Consolidated with @Storify - https://t.co/UYO9KDniOr
— Tinker (@TinkerSec) June 26, 2015Straight to investigation: The shellshock, ChinaZ, .IptabLes|x and BillGates
This report is not into details for each malware's technical analysis since the involved malware in this threat are the well-known type and previously analyzed ones (I posted them in here, in repository kernelmode and in VirusTotal too), but I will highlight the infection scheme to clarify what this threat actually is, and to point some information that can lead law enforcement to the actor behind the scene.
The received two reports are coming from two different time, different unrelated sources of the two pattern of shellshock attacks as per shown below, again, thank's to @tinkersec and @benkow for the share:
Let's see it as clean code (always beautify any malcode we read, we are not crooks, we should read it plain, clear and structured), there are many clue inside of these one-liner infection command actually, see below:
This shellshock code itself is showing the attackers IP address for both attacks are coming from 58.213.123.107 and the shellshock commands used were a common way seen for executing bash command via User-agent() and a direct GET command with shellshock vulnerability strings. This shellshock code is showing us, in a glimpse, that the ChinaZ malware crooks is spreading their ChinaZ payloads < what exactly ChinaZ bad actors want us to think. So let's see further..
The second fact..the first & the second shellshock attacks in log were detected by the different researchers in different continents and different infecting time (June 26 and June 30)), but it is having the same ELF payload:
It's pretty odd for me to find shellshock same ELF malware that lasts more than 3 days, specially to Linux/ChinaZ since they have their own codes and builders..weird. Why?
And look at what has been "specifically found" in that payload sample:
This is the signature of the Linux/.IptableS|X malware! There is no ChinaZ source code is having IptabLes|x interactive shutdown and restart command like this. See how the coder try to hide those within bunch of real iptables (note the characters) firewall shutdown command. Moreover, it makes so much sense why there are command closefirewall() to stop the running iptables service instance in the victim system for the purpose of infecting IptabLes|x malware:
Now many mysteries are solved eventually :-)
Why they did this? Why they use IptabLes|x ? So far the conclusion is apparently either ChinaZ crooks starting to drop their original payload (because we reversed and exposed them way too much?) ..Or there's someone wants to play as "ChinaZ" and spread IptablesS|X instead.
Well..okay, let's dig further information into the panel used for the infection source, and let's see what else we can gather over there now :)
Okay, for you who haven't seen these web panel before, it is a modified HFS web server (a good and legit web server, my fav tool in work actually) Chinese version on 202.103.243.104 and contains .Iptables|X x32 and x64 versions and.. a Linux/BillGates ELF DDoS malware too! Wow, so now we are facing the fact that we may have a "ChinaZ crooks" using .IptableS|X and Linux/BillGates as payload. Noted: there are so many download score for the x32 version of IptableS|X (see in the screenshot, more than 4,000 hits for download) explaining there were so many running Linux box may got hit by shellshock infection script sent by attacker and downloading by this malware. Yes, even now, shellshock still indeed effective to spread bash-basis attacks/malware infection.
The attacker IP is running as bot to infect all linux server's with the web server scanned under below detail:
Noted: we seriously need to stop this IP attacking the internet as soon as possible!
58.213.123.107||4134 | 58.208.0.0/12 | CHINANET | CN | chinatelecom.com.cn
ChinaNet Jiangsu Province Network
{
"ip": "58.213.123.107",
"hostname": "No Hostname",
"city": "Nanjing",
"region": "Jiangsu",
"country": "CN",
"loc": "32.0617,118.7778",
"org": "AS4134 No.31,Jin-rong Street"
}
And the panel is running in IP with the below detail:
As you can see, both attacker and infection panel are running from the same route of AS4134.
202.103.243.104||4134 | 202.103.192.0/18 | CHINANET | CN | chinatelecom.com.cn
ChinaNet Guangxi Province Network
{
"ip": "202.103.243.104",
"hostname": "bbs.gliet.edu.cn",
"city": "Guilin",
"region": "Guangxi",
"country": "CN",
"loc": "25.2819,110.2864",
"org": "AS4134 No.31,Jin-rong Street"
}
Below is the PoC of the panel domain used, could be a hacked server of an educational network in China.. or could be a hacked domain instead:
Malware analysis
The technical analysis online I did on Linux/IptableS|x sample while suporting @TinkerSec on twitter (see the tweet I embedded above for the link) is correct, so I am not going to add more details on those, and the point is, it highlighted this CNC information:
"domain: v8.f1122.orgCNC hard evidence taken during the test:
IP: 61.160.212.172
port 1122 "
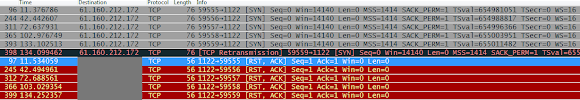
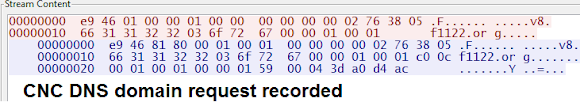
Detail information of the CNC domain and IP address
.IptabLes|x CNC information:
And the domain registration info is below and looks freezed now :)
61.160.212.172| - |23650 | 61.160.212.0/24 | CHINANET-JS-AS | CN | chinatelecom.com.cn
ChinaNet Jiangsu Province Network
{
"ip": "61.160.212.172",
"hostname": "v8.f1122.org",
"city": "Nanjing",
"region": "Jiangsu",
"country": "CN",
"loc": "32.0617,118.7778",
"org": "AS23650 AS Number for CHINANET jiangsu province backbone"
}
Well, WENDINGBA@163.COM is associated with Xihuang Li and 5 other names. A total of 1,382 associated domains were identified, most of them are registered in GoDaddy or ENOM. He is a professional crook in the field. Below is the snip of the first 20 domains, the information is available for al of us to access:
"Domain Name:F1122.ORG
Domain ID: D174941520-LROR
Creation Date: 2015-01-03T06:46:16Z
Updated Date: 2015-03-05T03:45:24Z
Registry Expiry Date: 2016-01-03T06:46:16Z
Sponsoring Registrar:GoDaddy.com, LLC (R91-LROR)"
Sponsoring Registrar IANA ID: 146
WHOIS Server:
Referral URL:
Domain Status: clientDeleteProhibited -- http://www.icann.org/epp#clientDeleteProhibited
Domain Status: clientRenewProhibited -- http://www.icann.org/epp#clientRenewProhibited
Domain Status: clientTransferProhibited -- http://www.icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited -- http://www.icann.org/epp#clientUpdateProhibited
Registrant "ID:CR184376377"
Registrant "Name:xihuang li"
Registrant Organization:
Registrant "Street: shanxishengdatongshibeijie23hao"
Registrant "City:shanxishengdatongshi"
Registrant "State/Province:shanxisheng"
Registrant Postal Code:037000
Registrant Country:CN
Registrant "Phone:+86.3522036283"
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant "Email:wendingba@163.com"
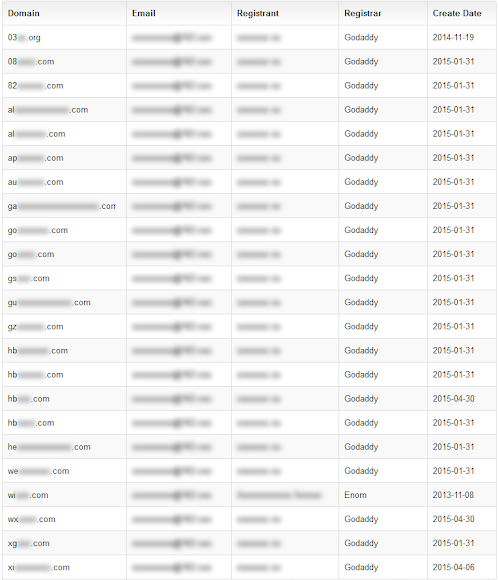
The Linux/BillGates is as usual, please find our previous MMD posts about these samples, this one has nothing to add. The CNC information is as per below:
Domain: udp.f1122.org
IP: 61.160.213.18
Port: 25001
Proof of the callback to CNC downloading configuration file:
socket(PF_INET, SOCK_STREAM, IPPROTO_IP
sendto(5, "W\204\1\0\0\1\0\0\0\0\0\0\3udp\5f1122\3org\0\0\1\0\1", 31, 0, {sa_family=AF_INET, sin_port=htons(53), sin_addr=inet_addr("DNS")}, 16)
recvfrom(5, "W\204\201\200\0\1\0\1\0\2\0\n\3udp\5f1122\3org\0\0\1\0\1\300"..., 1024, 0, {sa_family=AF_INET, sin_port=htons(53), sin_addr=inet_addr("DNS")}, [16])
connect(4, {sa_family=AF_INET, sin_port=htons(25001), sin_addr=inet_addr("61.160.213.18")}, 16)
open("/XXXX/conf.n", O_RDWR|O_CREAT, 0644)
write(5, "\0\364\1\0\0002\0\0\0\350\3\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\1\1\2\0\0\0"..., 69)
close(5)
Proof that the CNC is ESTABLISHING connection from the malware:
$ date
Wed Jul 1 15:25:44 JST 2015
(snips)
28443 28453 txt REG 8,6 1223123 1048605 /sudp
28443 28453 0u CHR 1,3 0t0 1192 /dev/null
28443 28453 1u CHR 1,3 0t0 1192 /dev/null
28443 28453 2u CHR 1,3 0t0 1192 /dev/null
28443 28453 3uW REG 8,1 5 261598 /tmp/gates.lod
28443 28453 4u "IPv4 127246603 0t0 TCP MMD:32977->61.160.213.18:25001 (ESTABLISHED)"
The above mentioned CNC hostname in DNS shows:
;; QUESTION SECTION:
;udp.f1122.org. IN A
;; ANSWER SECTION:
udp.f1122.org. 600 IN A 61.160.213.18
;; AUTHORITY SECTION:
f1122.org. 600 IN NS f1g1ns1.dnspod.net.
f1122.org. 600 IN NS f1g1ns2.dnspod.net.
;; ADDITIONAL SECTION:
f1g1ns1.dnspod.net. 350 IN A 113.108.80.138
f1g1ns1.dnspod.net. 350 IN A 125.39.208.193
f1g1ns1.dnspod.net. 350 IN A 180.153.9.189
f1g1ns1.dnspod.net. 350 IN A 182.140.167.166
f1g1ns1.dnspod.net. 350 IN A 111.30.132.180
f1g1ns2.dnspod.net. 1015 IN A 115.236.137.40
f1g1ns2.dnspod.net. 1015 IN A 115.236.151.191
f1g1ns2.dnspod.net. 1015 IN A 182.140.167.188
f1g1ns2.dnspod.net. 1015 IN A 101.226.30.224
f1g1ns2.dnspod.net. 1015 IN A 112.90.82.194
With the IP is located in:
As per predicted, the Linux/BillGates sample is using the same domain of f1122.org and located in the same network as per CNC of IptableS|X, we have the same actor here operated in both CNC, this is a hard evidence. And as always the crooks were closing the connection after I connected :-)
61.160.213.18| - |23650 | 61.160.213.0/24 | CHINANET-JS-AS | CN | chinatelecom.com.cn
ChinaNet Jiangsu Province Network
{
"ip": "61.160.213.18",
"hostname": "udp.f1122.org",
"city": "Nanjing",
"region": "Jiangsu",
"country": "CN",
"loc": "32.0617,118.7778",
"org": "AS23650 AS Number for CHINANET jiangsu province backbone"
}
In the previous ChinaZ report [link] it was shown that the CNC was registered under email bm18801463268@163.com and this time it uses the email of wendingba@163.com, I am sure we have the same crook(s) here. It is nice to inform that we contacted 163.com for more details, and that info to be shared to law enforcement only.So have a nice day to the bad actor, your crime is exposed and all of your malware are reversed and blogged here, using another malware binaries is not gonna stop us nailing you all over the internet, we know all of the stuff you use! ChinaZ MUST Die! Proof of concept that CNC 58.221.254.153 belongs to ChinaZ: Builder, Hard code & CNC software
Supporting to the cyber crime investigation that follows the case. Our team also has confirmed that the 58.221.254.153 belongs to ChinaZ actor, contains the ChinaZ builder, a windows application, contains the code of ChinaZ in that builder, and using CNC used for ChinaZ.
PoC #1: This is the builder: -->[VT]
If you run it, it will seek for binary templates of ELF (x32 or x64) and windows (x32) in the subfolders, and popping up the menu to build the package under any desired IP. The port number is a fixed number of 29136, encryption used in the templates is not allowing modification for this value, by this, we know this bad actor is not the software coder but a mere player:
The reversing code shows how the builder work, it is a safe application. Sorry I have to do day work so this is only a short peek of my reversing for you, it shows the path of the template binary used for this builder to make it work. If the path doesn't exist the builder will not build anything:
PoC #2: The builder's template is ChinaZ: -->[VT] and [VT]
I am taking the template binary of the builder used of "\\Arch32\\DDosClientTemp32", the x32 template ELF file, to PoC is it the ChinaZ or not. In the previous BLOG about the ChinaZ we disclosed the GitHub URL used to develop the ChinaZ malware, our friend's @benkow suggested to take it as example to make a smart PoC as per below snip code, the marked part are functions that ChinaZ used specifically:
And the code is perfectly matched to the binary value in "\\Arch32\\DDosClientTemp32" 
PoC #3: The CNC software of ChinaZ -->[VT]
In the same zip it was found the CNC software of ChinaZ, contains the below files and log:
And if you runs it the CNC software of CNC is run and bound to your port to listen to ChinaZ DDoS client/agent/bot to connect to you: 
Based on the 3 PoCs above we are sure beyond any doubt that; Host in 58.221.254.153 that attacked many Linux hosts in the internet with the shellshock attack to infect malware binaries belongs to ChinaZ actor(s), and therefore the ID data stated in previous chapter are all directly related to ChinaZ bad actor(s) in this case and ChinaZ previous post MMD-0032-2015.
Thank Benkow for spotting "stuff" in 58.221.254.153
Samples & Virus Total link
These are the samples I uploaded with correct names in the VirusTotal:
1122.32.ELF.IptableX.DDoS 58eefd9183ac89a1b99dda02e0ab4092
1122.64.ELF.IptableX.DDoS 8d18ddc23603726181ebb77931aa11f3
sudp.Elf.BillGates.DDoS 84d431618cbbbf56fe0cc3d34f62a655
..and all of the samples I share in kernelmode here [link] and in here [link] and also in here [link].
ChinaZ's IpabLes|x and.. Linux/Xor.DDOS!! - a new variation:
The same machine served same IptabLes|x was spotted online:
@WhiskeyNeon @c0mmand3r420 @DHAhole @TinkerSec It's same m/c we saw back then, except now global IP is new. No doubt. pic.twitter.com/fNF7X1dmaX
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015These are the shellshock used, the panels, the same ELF bin and the traffic:
@MalwareMustDie screenshots of this case is attached from various sources | thx to all pic.twitter.com/MB5NRPmvA5
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015Same IP also used as landing for shellshock attack on July 10th 2015
@MalwareMustDie atack log on Jul 10 2015 pic.twitter.com/kRRhWoNTvc
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015But this time instead of using Linux/BillGates as additional malware, it uses LinuxXOR.DDoS instead:
..and it looks like #ChinaZ actor starting to spread #Linux/XOR.DDoS'er #ELF #malware too.See the HIT
#MalwareMustDie pic.twitter.com/12y46gw1HS
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015The location of the new IP is also shifted to the Beijing..
Where ChinaZ crook is now..
211.147.2.192|ASN4847|211.147.0.0/21|CNIX
Beijing 39.9289,116.3883
CNCGROUP China169 pic.twitter.com/5I1DHmPKcc
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015The samples are here:
@MalwareMustDie verdict samples VT
https://t.co/0tUopyurdo
https://t.co/lmjmb1m3ux
https://t.co/nlVkrrSYPT
Repo:
http://t.co/feoiCwK8gZ
#MMD
— ☩MalwareMustDie (@MalwareMustDie) July 13, 2015#MalwareMustDie!