MMD-0036-2015 - KINS (or ZeusVM) v2.0.0.0 tookit (builder & panel source code) leaked.
05 Jul 2015This sharing has been closed due to time limit (60days) - Thank you
The background
KINS (or ZeusVM to be precised) v2.0.0.0 tookit (builder & panel source code) was leaked and spread in all over the internet. On Jun 26th 2015 we were informed (thank you Xylit0l) about this and after several internal discussion, considering that: "Still so many bad guys know about this than good guys.." today we decided to raise warning about this matter by this post. So this is an information to those who may not know about the leaked package yet, and/or maybe want to have the archive of what has leaked from the trusted source.
Together with this warning also we would like to inform that KINS version 3 is on the black market now with the price of 5k according to a certain crook's affiliated forum.
This is a team work, two friends Xylit0l [link] and unixfreaxjp [link] are on the case building this report, testing, recording, screenshots, takedown sites that spread the leaked packages as much as possible..
What was leaked exactly?
What was leaked is NOT KINS version 2.0.0.0 source code but the KINS version 2.0.0.0 builder binary, as per seen in the below screenshot (taken by Xylit0l).. 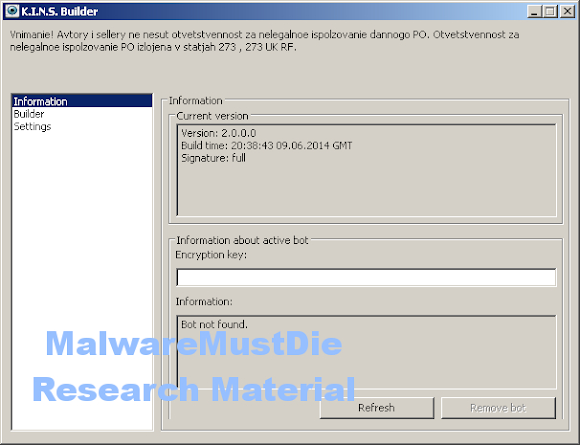
..and the panel's source code as per shown in the video embedded to this post. Pictures of KINS used web panels are as the below images (taken by Xylit0l). It shows the classic style of ZeuS botnet panel: 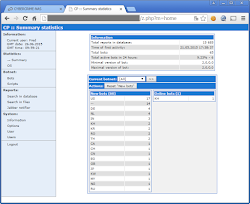
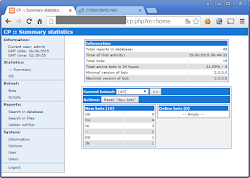
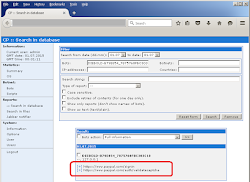
Pictures/info posted are MMD research material bound to legal disclaimer-->[link]
Eventhough the name used by the coder is KINS 2.0.0.0. the builder configuration and the binary generated by the builder is of ZeusVM (version 2.0.0.0) and is a completely different to previous KINS version we announced in here-->[link].
Previous KINS version don't use steganography (way of hiding information by embedding messages within other, seemingly harmless messages, in this case Zeusvm hides configuration codes embedded in JPG file) while this one do, and the generated ZeusVM bot binary is similar to ZeusVM v1 and v2 samples posted in kernelmode repository-->[link] This is why we put ZeusVM in the title of the post, an evidence that KINS has adapted ZeusVM technology in their malware. This is maybe a bit confusing if you don't follow recent ZeuS malware evolution time frame, but it's the fact of what had been found & analyzed by experts.
Enough talking, show us the package!
Below is the video of what has been leaked. The video shows you: (1) the archive information and some leak sources, (2) the builder and its general demonstration (JPG config demo is in the next video), (3) the panel and its code, and the (4) ZeusVM web injection proof of concept screenshots after tested by Xylit0l in the latest version of the Firefox browser (yes, it is working fine in IE). I took the video during testing.
PoC Video #1:
PS: The comment in 2:34 has a mistake. It supposed to be "The binary & crypted module files"
Where is that Steganography PoC?
Below is the video demonstrating the Steganography technique used by the KINS/ZeusVM 2.0.0.0. The demonstration is showing us that builder can inject encrypted configuration code of KINS2/ZeusVM2 to any JPG file feed to the builder to camouflage the config. We compare the "before" and "after" code injection data of the JPG files used & generated in hex editor for comparison detail. Xylit0l and I discussed a lot to get the right injecting test scheme with correct template of its configuration..finally made it right. Sorry, we break malware apart but not using them.
PoC Video #2:
As additional information to these videos:
1. This is list of blocked IP by KINS/ZeusVM 2.0.0.0 panel's .htaccess-->[link]
2. The mod files built in hex (head):
3. The log of correct configured building:
4. The SHA256 of the builder: 7b6cc23d545dea514628669a1037df88b278312f495b97869b40882ca554fa9a [VT]
5. In Botconf [link] 2014 conference our friend @MAK of CERT Polska [link] presented a good research paper of ZeusVM threat that can be used as reference to ID the binary built-->[link]
Snapshot of important codes
The version, template built date and default config items: 
The "kinsdb" was clearly stated in MySQL database name of the botnet panel too: 
The PHP encryption function spotted in panel's source code to encrypt the database: 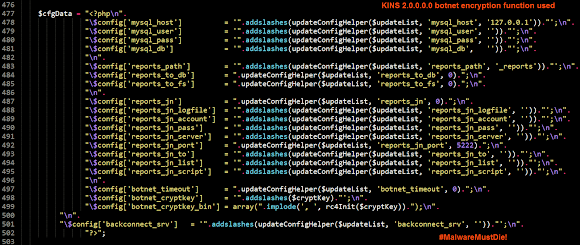
So what does it mean?
(1) We will see more of ZeusVM (version 2.0.0.0_) botnet operated in our internet since its malware & configuration builder is "FREE as air" and is "go public" now, not only from usual cyber crime crooks, but anyone with this toolkit in hand can generate ZeusVM 2.0.0.0 binaries and set it to botnets via its panel; and ; (2) We also we can expect to see a KINS/ZeusVM new version (version 3) soon too.
This is a very important information for the security community. The archive is wide spreading now, we tried very hard to take down some leaked package shared in download sites one by one but it is just way out of hand. Please help us to not letting this archive spread and distributed in the internet.
It is better for all anti malware and all threat filtration industry to know and request the leaked archive and start to research the blocking and mitigation methods, if you haven't started it yet. You can get archive or builder from here or VirusTotal or from other trusted sources. The ITW (in the wild) emerge of many KINS 2.0.0.0 leaked tookit botnets threat has been started..
This is the update of the latest information, current date is: Mon Jul 6 23:41:30 JST 2015
As per shown in the video above, in the default configuration of the KINS 2.0.0.0 there is the image file of "server.jpg" provided by the malware coder for creating a steganographic KINS2.0.0.0 JPG injected crypted configuration file, with the graphic physical look as per below:
We follow the current detected KINS botnet up and alive operated in the internet and we found that at least 10 botnets are using the same default configuration picture and 6 of them are up and alive in the below URLs!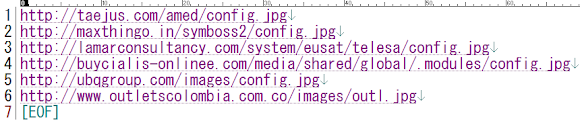
The bove listed URLs are KINS 2.0.0.0 steganographic config files online, generated from the builder shown in the demonstration video of leaked KINS2 toolkit in the previous section. Those URLs are currently accessible UP and ALIVE in the internet, spotted as per now..
So the new botnets using the leaked package of KINS 2.0.0.0 are actually start popping up in the internet ..running by crooks or blackhats and actively in action to infect KINS 2.0.0.0 bot PC clients to some victims..are used for the bad purpose only..
Xylit0l was advising me to add this section for security folks to notice that the leaked KINS2" toolkit is actually has started to be used and emerged into new threat wave, and I decided the best way to convince all of you is by the video.. so I recorded the confirmation I made in video below to be used as PoC evidence of the mushroomed of usage for KINS 2.0.0.0 leaked toolkit, aand (maybe) can be used for the crime evidence..
FYI..we are not happy nor proud to write this.. This is sad, to know that something bad will happen and it is actually happened in front of our own eyes.. FYI, we are still trying hard to spot and to take down new shared downloaded archive of leaked toolkit distributed in several "blackhat" forums,to do whatever we can to reduce this threat, please help us to do so. And thank you very much to many media download service for your kindly cooperate to help us to delete the shared malicious malware toolkit, you are the true heroes for this cause.
How to get the archive? (for the case from MalwareMustDie, NPO)
Please post the comment with your email address informed for the full archive request and we will send you the download link. Your post will not be published and your email address will not be shared. But please be patient for the sharing process. All follow up will be done manually and will be logged. We will prioritize requests coming from anti virus companies and threat filtration products. Then the governments' CERT & law enforcement related research entities. We will not share to individual or unnamed request, this is a very dangerous malware building tool, a crimeware and NOT sample of malware or toys to play with.
Noted: We have every right also to not sharing the archive and not responding to any untrusted/suspicious requests.
For more information of our sharing policy please read our legal disclaimer here-->[link]
Additional section
Several takedown efforts we made: (there are more of these effort than we posted here)
The bad actors who spread this leak are ↓not noticing being taken down↓ :-)
Crooks spread KINS2 leaked toolkit w/many tricks & to many download sites.
This is PoC of 1of them!
#MalwareMustDie pic.twitter.com/F3twg4QJaD
— ☩MalwareMustDie (@MalwareMustDie) 2015, 7月 8The surge of "freeware" KINS2 leaked botnets is on..
The fact: We monitored the surge of this leak-basis KINS 2.0.0.0 botnets, to found that since we start monitoring on July 7th 2015 (around midnight JST) and now..July 9th around 10am (JST), 16 new botnets are up and 11 of them are actively infecting. These detected botnets were built by the default setting of the leaked botnet toolkit. Below are two proof videos (you can see what I mean by default setting in that videos), I took them in July 7th 2015 and July 9th 10am.
The point: Please ask yourself..if less than 2 days the (known only) 16 botnets were popping up .. how many botnets we can expect within a month operated and infecting us with the same surge pace?
The Plan to mitigate this surge:
- takedown EVERY shared archives that spread by crooks in the internet
- release blocking sigs soon (if you are not yet)
- block default toolkit configuration object used download web traffic filtration scheme
- seek & clean up infrastructure used by surged botnets before it gets too many
@MalwareMustDie well.. don't say that we didn't warn you about this.. for 2 days = 16 botnets, how many for a month then? do the math.
— ☩MalwareMustDie (@MalwareMustDie) July 9, 2015Thank you for reading, please help to spread this awareness and stay safe!
Thank Xylit0l, he is doing very hard effort to fight, detect and act against this threat for YEARS.
MalwareMustDie!









